APT41 Now Targeting Southeast Asian Entities With New Shellcode Loaders and Backdoors
- APT41 has been spotted to use a new toolset against targets in the Southeast Asia region.
- The goal of the actors is cyberespionage, and their tools allow them to move around undetected.
- In their latest campaign, APT41 is exploiting the CVE-2021-26855 (ProxyLogon) vulnerability.
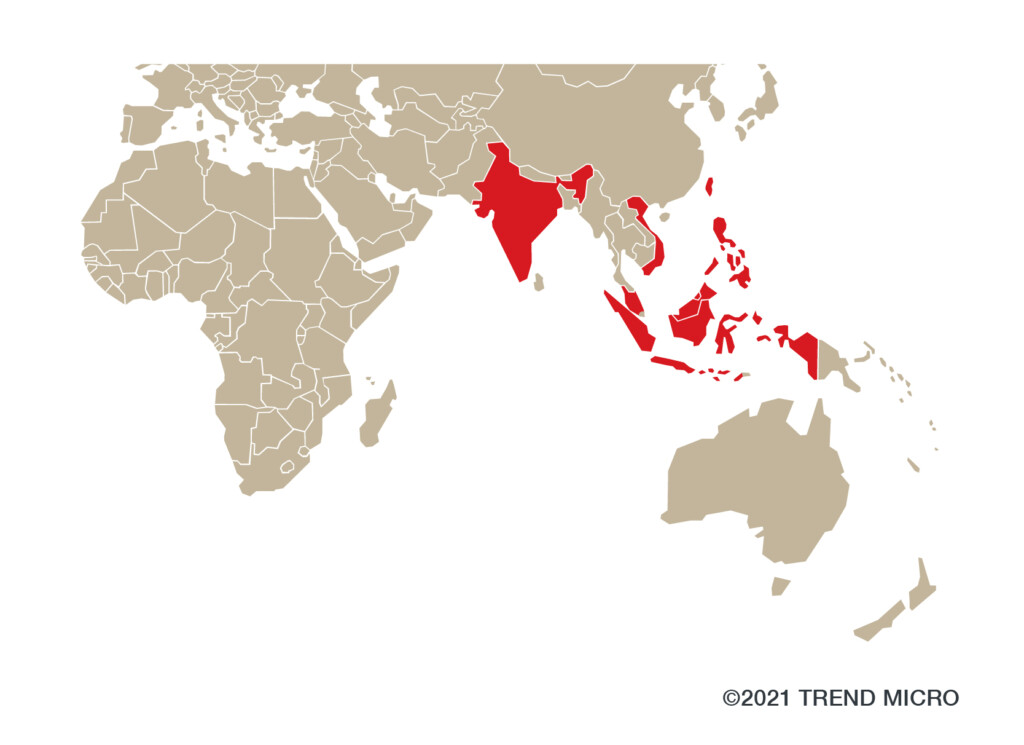
Actors of the APT41 group have been observed by researchers at Trend Micro in a new campaign targeting India, Indonesia, Malaysia, Taiwan, Vietnam, and the Philippines. The sophisticated hackers are using novel shellcode loaders such as ‘StealthVector’ and ‘StealthMutant’, and a new backdoor dubbed ‘ScrambleCross’.
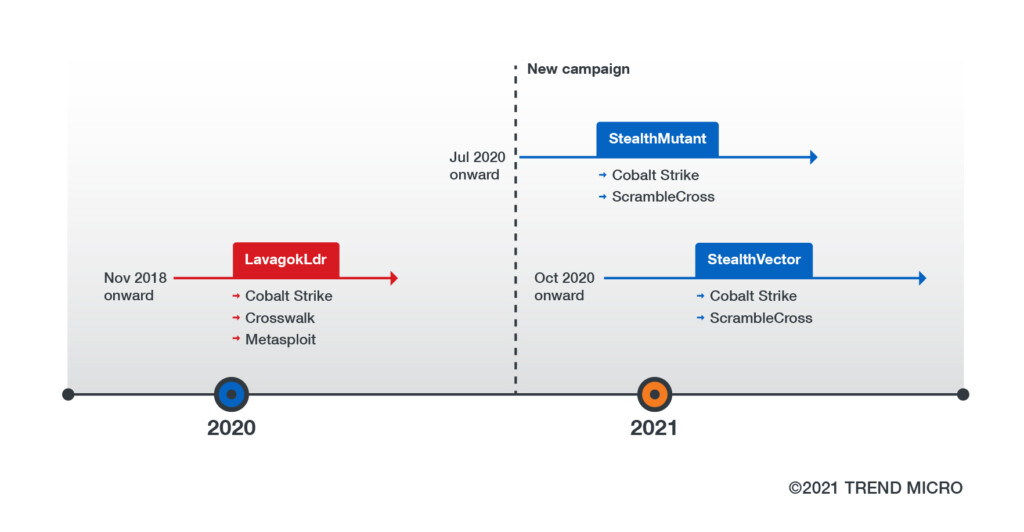
As the technical report reveals, the campaign goes as far back as July 2020, but APT41 has been updating its exploit methods and toolset along the way. The only tool that has remained stable since November 2018 is Cobalt Strike, the widely abused threat emulation software.
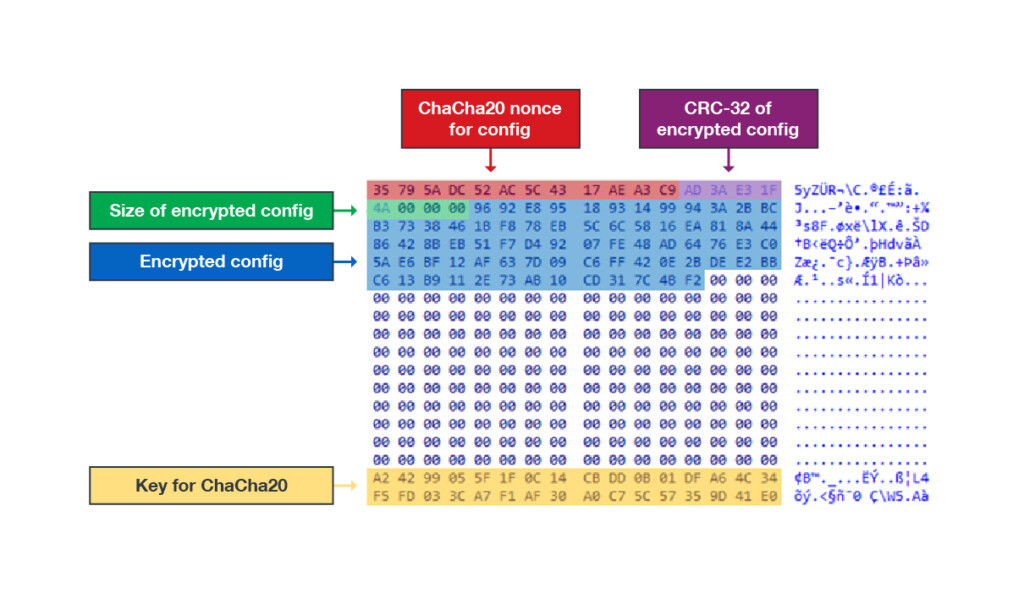
The two new shellcode loaders are written in C/C++ and are quite versatile, being configurable up to a point. They can run payloads on specific locations, uninstall themselves, disable ETW (Event Tracing for Windows) to evade detection, and also try out credentials. The configuration itself is encrypted with ChaCha20, while the payloads have been observed to use AES-256-ECB. Older versions used XOR, so there has been an evolution on that front too.
The attack vectors are the following:
- SQL injection through a script into the MS SQL Server
- Exploitation of the CVE-2021-26855 (MS Exchange Server ProxyLogon) to upload a malicious web shell
- Addition of the “InstallUtil.exe” installer app into the scheduled tasks
Even though the researchers haven’t seen any phishing emails as part of this campaign, it is very likely that this is how the initial infection takes place. As for the attribution, the latest campaign uses the same DLL (Storesyncsvc.dll) and similar API loading procedures that have been linked to previous campaigns. Signature checking and function decoding processes are also the same as those that have been seen by the group in the past, so the attribution is made with high confidence - if not certainty.
As for the goal and targets profiles, APT41’s latest campaign is done for cyberespionage, and the targeted entities are typically engaged in the airline, computer hardware, automotive, infrastructure, publishing, media, and the IT industries. APT41 is believed to be a state-sponsored Chinese group, so they have a strong interest in spying on the aforementioned companies in the Indo-Pacific region. Most recently, they were spotted targeting key power grid units in India, causing power cuts during periods of tension between the two countries.