APT41 Leveraging Google Calendar for C2, Distributes TOUGHPROGRESS Malware
- PRC-based actor APT41 was seen misusing cloud services for C2 communications.
- A compromised official website was leveraged for distributing spear phishing emails.
- The exploited government site was used to target multiple other government organizations with malware.
A new campaign, attributed with high confidence to China-based APT41 (also known as HOODOO), showcased advanced evasion, modular payloads, and abuse of cloud infrastructure for stealthy command and control.
In late October 2024, GTIG discovered an exploited government website distributing spear phishing emails. Victims received links to ZIP archives containing a disguised LNK file and a directory of ostensibly benign JPG images.
However, two files served as a delivery vector for a multi-stage malware chain. The LNK file, disguised as a PDF, triggered the infection, displaying a decoy PDF and initiating a three-stage payload:
- PLUSDROP decrypted and launched the next module in memory.
- PLUSINJECT performed process hollowing on “svchost.exe”, injecting the final stage.
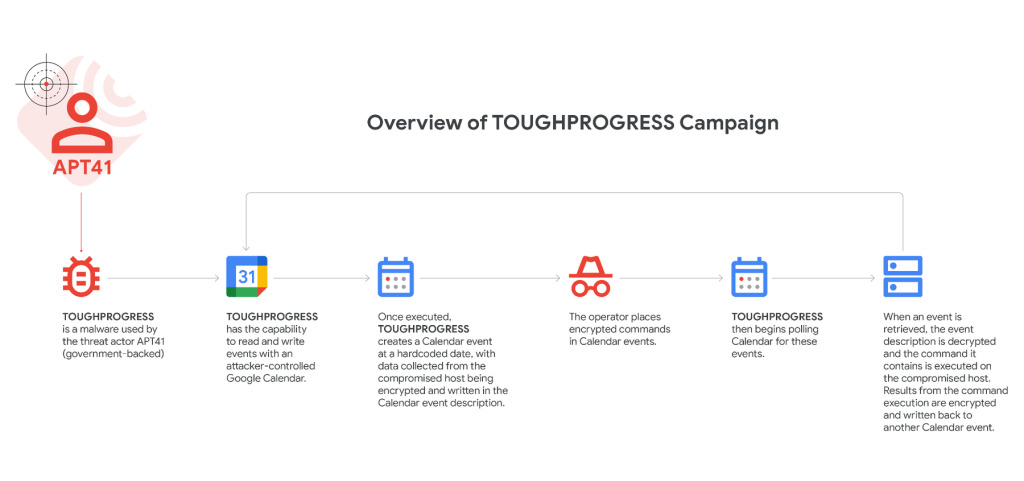
- TOUGHPROGRESS, the core malware, executed malicious operations and communicated via Google Calendar.
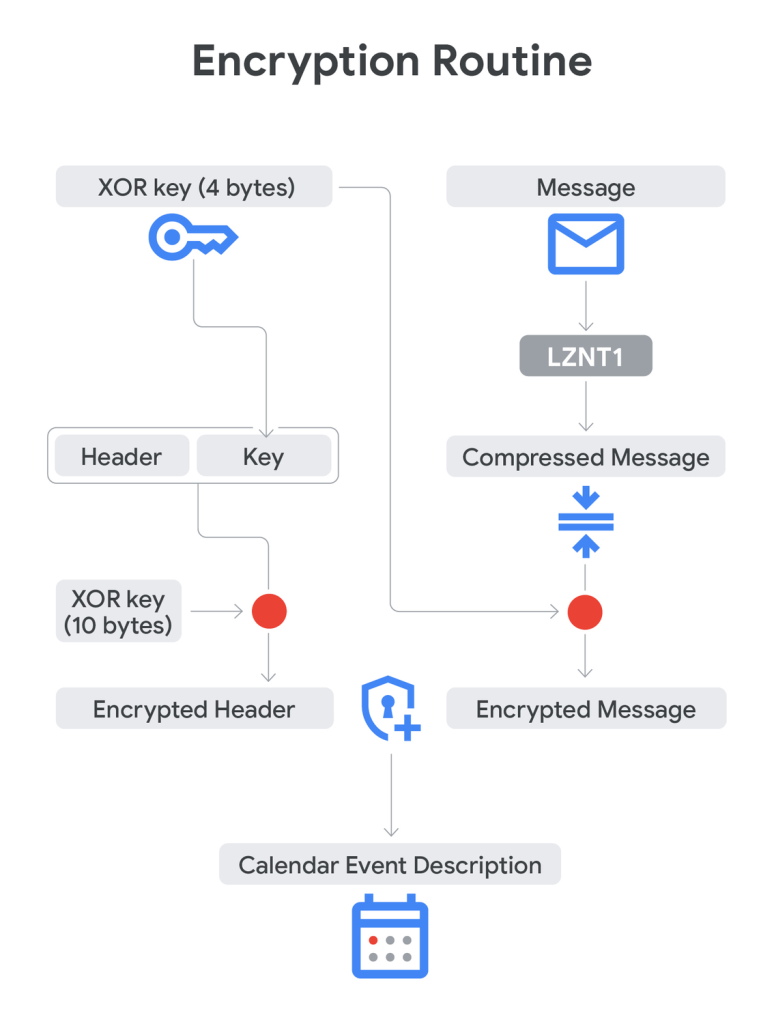
TOUGHPROGRESS stands out for its layered stealth and obfuscation, including encryption, compression (LZNT1), process hollowing, memory-only payloads, and advanced control flow manipulation.
The malware leverages register-based indirect calls, dynamic address arithmetic, and intentional register overflows, seriously hindering conventional static analysis.
Notably, TOUGHPROGRESS abuses Google Calendar for command and control (C2). It interacts with attacker-controlled events to receive encrypted commands and exfiltrate data by creating calendar events with encoded payloads and results.
All C2 traffic is protected by a customized encryption protocol featuring hardcoded and session-derived XOR keys.
GTIG, with Mandiant, reverse-engineered the malware’s encryption, identified malicious calendar fingerprints, and terminated attacker-controlled Workspace projects. They updated Google Safe Browsing with new detections and blocked related domains and URLs.
Impacted organizations received actionable intelligence, including network traffic samples, to support rapid detection and remediation.
Google dismantled the infrastructure that APT41 relied on for this campaign via custom fingerprints to identify and disable attacker-controlled Calendars and terminated attacker-controlled Workspace projects. Additionally, we
In partnership with Mandiant Consulting, GTIG notified the compromised organizations and updated file detections, adding malicious domains and URLs to the Google Safe Browsing blocklist.