APT33 Targeting Oil and Aviation Firms Through Private VPN Network
- APT33 relied on a private VPN network to control small botnet and collect key information.
- The researchers took the opportunity and correlated malicious IP addresses with the VPN traffic.
- The threat actors have had their infrastructure exposed, so they will scrap and rebuild it.
As reported by Trend Micro researchers, the APT33 hacking group is currently targeting oil and aviation industries through a new C&C infrastructure that sits behind multiple obfuscation layers. The Iranians are known for several nasty online activities, with the most notable being their Shamoon data-wiping malware that targeted oil companies back in 2017. However, it looks like the group has now made a mistake in hiding their tracks, as Trend Micro has managed to identify a small private VPN network that they use to connect to data aggregators.
Source: Trend Micro
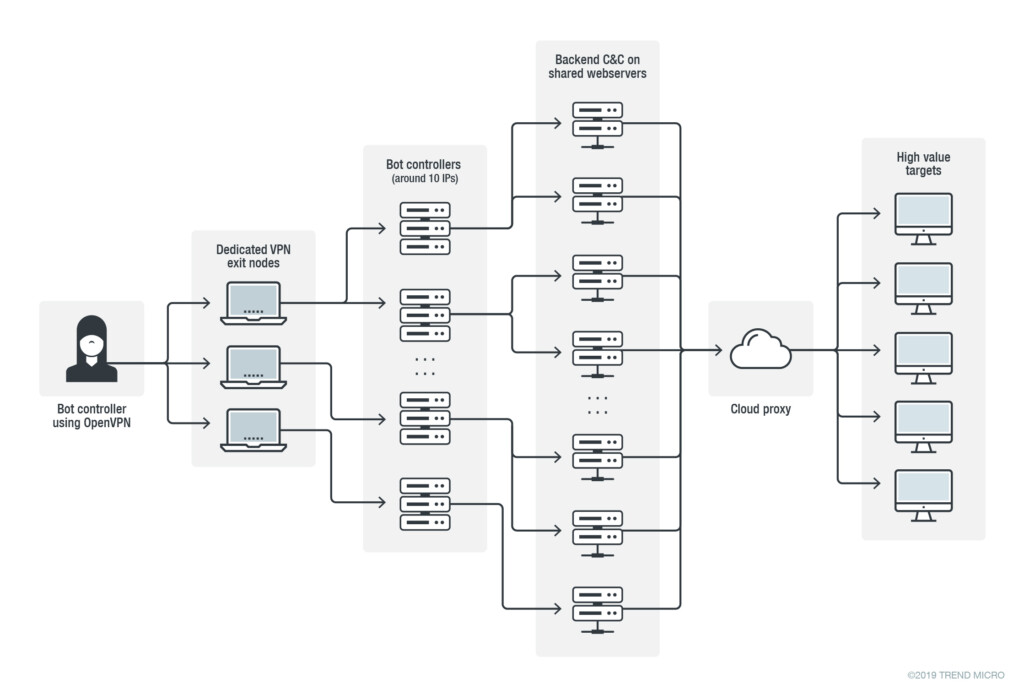
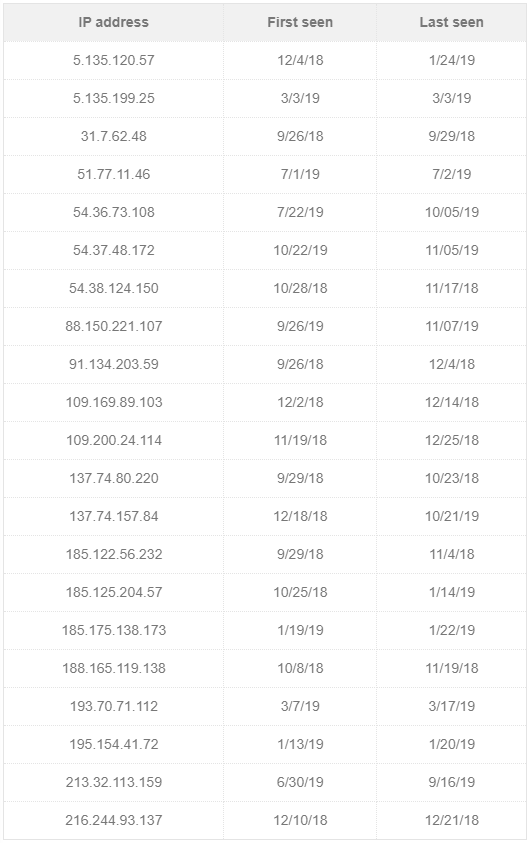
APT33 is deploying small botnets comprising of a dozen of bots each, controlled by several C&C domains that are hosted on cloud proxies. The researchers have already discovered ten live bot data aggregating and bot controlling servers, which seem to engage in very narrow targeting operations. The bot operator is hiding behind a custom VPN network, so the IP address and location is masked. The network’s exit nodes are changed frequently to make tracking more difficult. The thing is though because APT33 set up its own custom OpenVPN implementation, they made it easier for Trend Micro to actually figure out their real IP addresses. If they were using a commercial VPN solution, they would be able to “blend in the crowd” more easily. The result is the following IP address table which is connected to APT33 activity:
Source: Trend Micro
As the Trend Micro details, the actors are still targeting the oil industry, doing network reconnaissance. Other targets that were identified include U.S. companies and military hospitals in the Middle East. The websites that the hackers accessed through their private VPN network concern penetration testing firms, webmail, vulnerabilities databases, cryptocurrency websites, and various hacking blogs and forums. All that said, the APT33’s targeting is still focused on high-profile companies that deal with critical infrastructure, resources, and operations.
What all this means is that oil industry companies should cross-check their security log files with the IP addresses that were provided by the Trend Micro team. Other than that, the researchers give some solid security advice such as installing a multilayer protection system, an intrusion filtering mechanism, apply patches as soon as they become available, and invest in employee training. The APT33 has now taken a blow, but this won’t stop them from changing their infrastructure and obfuscation approach now. Their cover was blown, but they are far from being identified.
Have something to comment on the above? Share your thoughts with us in the comments down below, or on our socials, on Facebook and Twitter.