APT28 Russian State Campaign Against Western Firms Intensifies, Gathering Intel on Ukraine Aid
- The Russian General Staff Main Intelligence Directorate is more aggressively targeting the U.S. and more.
- These cyber espionage campaigns try to gather intelligence on the coordination and delivery of military aid to Ukraine.
- They leverage brute forcing, spearphishing, credential harvesting, malware delivery, and exploitation of high-profile software flaws.
The Russian GRU’s 85th Main Special Service Center (Unit 26165)—also known as APT28 or Fancy Bear—is pursuing an aggressive cyber espionage operation targeting Western logistics entities and technology firms.
This General Staff Main Intelligence Directorate (GRU) campaign, ongoing since 2022, is part of a broader effort to gather intelligence on the coordination and delivery of military aid to Ukraine, a new joint advisory from cybersecurity authorities across the U.S., U.K., Europe, Canada, and Australia warns.
Key findings from the advisory highlight several critical elements of this campaign
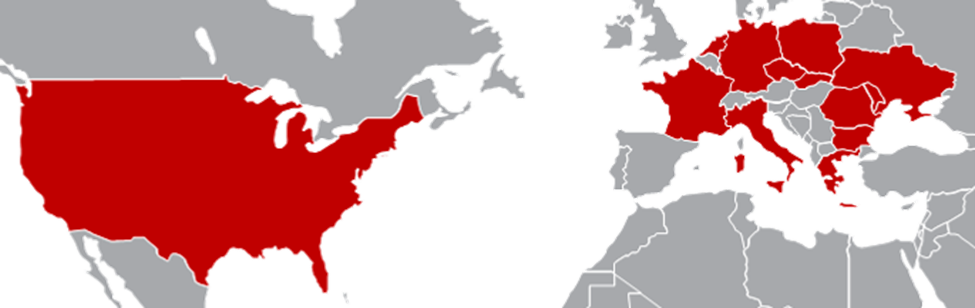
Attack targets include logistics providers across air, maritime, and rail sectors, IT service companies, and organizations closely linked to the transport and defense of Ukraine.
The campaign’s scope extends throughout NATO nations and partners, with dozens of entities in the U.S., France, Germany, Poland, the Netherlands, and other countries affected.
Tactics, techniques, and procedures (TTPs) employed by Unit 26165 feature credential guessing and brute force attacks, spearphishing with both credential-harvesting and malware delivery, and exploitation of high-profile software vulnerabilities, such as Microsoft Outlook (CVE-2023-23397), WinRAR (CVE-2023-38831), and multiple flaws in Roundcube webmail.
After initial access is established, attackers conduct lateral movement using native tools (PsExec, Impacket, Remote Desktop Protocol) to escalate privileges, persist by modifying email permissions or registry keys, and exfiltrate data, including sensitive information about shipments, schedules, and cargo.
A notable aspect of the campaign is the targeting and compromise of IP camera infrastructure, particularly at Ukrainian borders and key transport nodes. This enables real-time monitoring of aid and logistics movements, with 81% of compromised devices located in Ukraine.
Malware observed in these intrusions includes HEADLACE and MASEPIE, with advanced credential theft and data exfiltration capabilities. The campaign’s tradecraft demonstrates a sophisticated blending of living-off-the-land techniques with bespoke malicious payloads.
Last year, the notorious Russian hacking group Cadet Blizzard was linked to the GRU 161st Specialist Training Center, also known as Unit 29155.