Anubis Banking Malware Only Activates When the User is On The Go
- Malware ridden Android apps will only activate when the user is moving, monitoring the device sensor data.
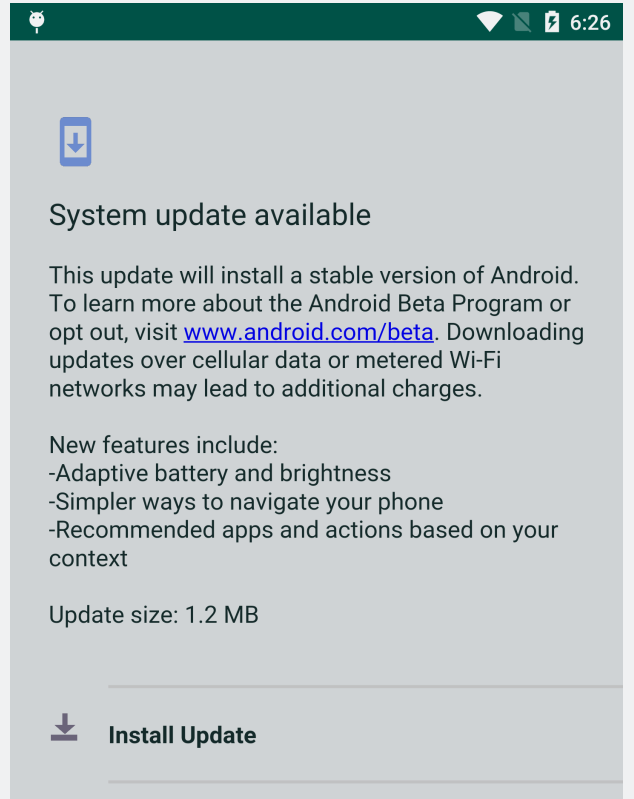
- The payload is delivered masked as an Android system update, urging the user to download it.
- The malware can act as a trojan, keylogger, and ransomware, all combined in a single package.
The Anubis malware that first made its appearance about a year ago has returned through two Google Play Store apps that pretend to serve as a currency converter and a battery saver. Upon closer inspection, the malware seems to employ a set of clever activity concealing techniques that make its detection less likely. More specifically, the apps used the motion sensors of the infected devices to check when the user is on the go and getting activated only then. Once the user stops moving, the malware gets deactivated and stays dormant until the next opportunity.
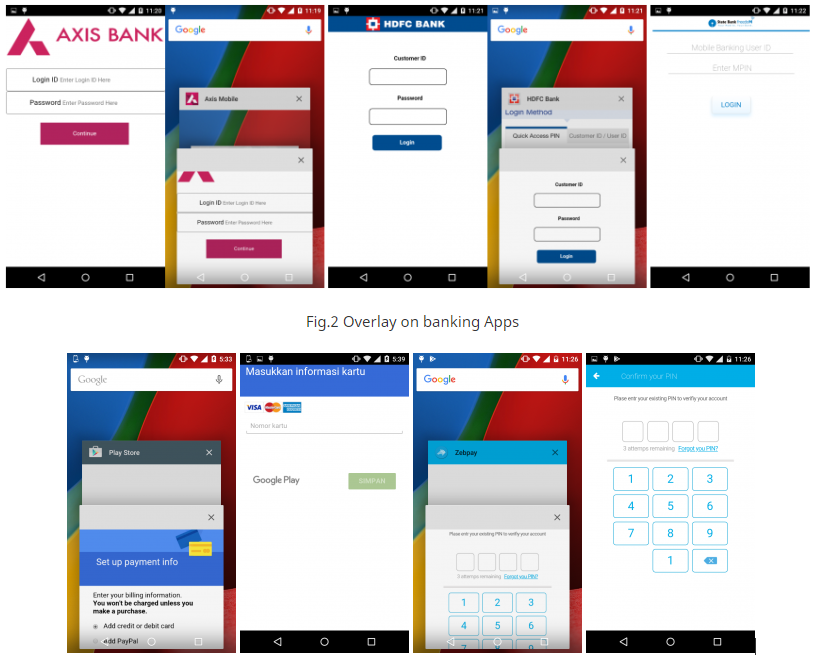
This also explains how the apps passed the filters of the stringent tests imposed by Google and got both approved for inclusion in the Play Store. The testers are using emulators to check the activity of the tested apps, but without having sensor data emulation, the malware didn’t get activated and so no malicious code activity was detected. When it does work, it tries to push a fake Android system update that is actually the payload APK that will ask for accessibility rights from the user. It then runs in the background and launches a fake bank service overlay screen to trick the user into inputting their credentials. Anubis is then either taking a screenshot of the filled out overlay screen or send the data in the form of logged keystrokes, so the job is done.
Image Credits: Trend Micro
Anubis can imitate 377 financial apps through its fake overlay screens, used across 93 countries, stats that are indicative of the activity and engagement of the actors that sit behind this malware. The battery saver app that came with it was downloaded about 5000 times before it got removed from the Play Store, and its functionality and eye-catching user interface have even won it a review score of 4.5 stars.
From the Quick Heal Technologies blog
Anubis is so versatile that it can also act as ransomware, as Quick Heal Technologies revealed back in August 2018. This makes the situation even more severe, as we are seeing that Android malware app developers are incorporating multiple attacking traits into a single package, implementing smarter methods to avoid detection, and offering a pleasant front-app to keep the users pleased.
Would you trust a battery saver app to manage the power settings of your device? Let us know in the comments section below, and don’t forget to share your thoughts on our socials as well, on Facebook and Twitter.