New Android Spyware Threat Poses as Antivirus in Japan
- An Android spyware is spreading rapidly in Japan, disguised as an anti-virus software.
- The malware is a new variant of FakeCop parading as 'Anshin Security,' flagging other antivirus for deletion while gathering a wide range of user data.
- The distribution is based on malicious URLs sent via email and SMS.
Japanese cybersecurity experts have identified a new variant of the FakeCop info stealer hiding behind the name of a legit privacy service app for Android by NTT Docomo called 'Anshin Security.' This spyware distributes a malicious APK in phishing links via email or SMS masked as the Japanese company KDDI. This malware also registered on 22 out of 62 AV engines on VirusTotal, which indicates that it has been developed to stay hidden across many parameters.
According to the cybersecurity firm Cyble, it collects SMS, contacts, accounts information, and apps list, modify or delete SMSs in the device database, device hardware information (IMEI), and sends SMS without the user’s knowledge.
Generally speaking, users do not look through the specific requests required by any AV software. Since antivirus software usually requires higher rights to operate on any device, users will grant them without looking. A custom packer masks the actual activity, which also throws off static detection by any other antivirus software.
The code itself is Bitwise XOR which is encrypted and filed within the assets folder. The file is only accessible by a specific app subclass’ executable function.
Further, the app will also look into other antivirus software and flag them as malicious, prompting the user to remove them. The app itself targets certain apps like the real Anshin Security, McAfee Security, and the Docomo Anshin Scan. These executions are hardcoded and will be flagged by FakeCop by default.
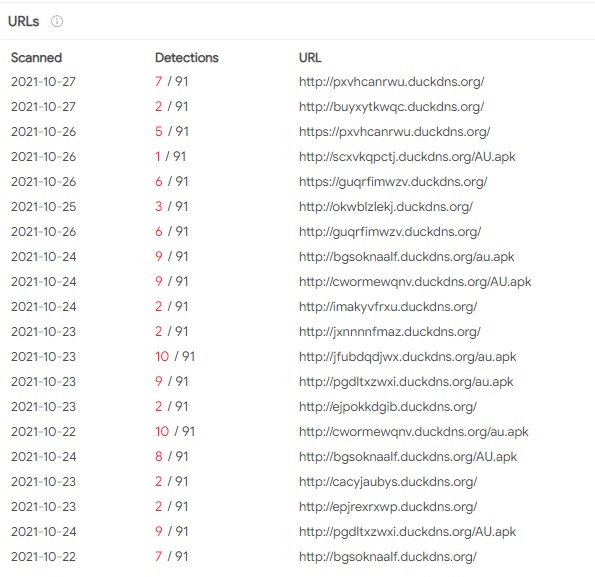
FakeCop also uses the 'duckdns.org' free dynamic DNS used to deliver, which was also used for other malware Medusa and Flubot. From that, the researchers have speculated that FakeCop might be a new malware from the same operators as Medusa and Flubot.
Users are recommended to use the latest versions of Google Play Protect, activate them, and also not click on unconfirmed URL links in SMS and email. They can also avoid installing APK files outside Google Play Store to avoid FakeCop and other malware.