Android Malware ‘FluBot’ Appears to Be Unstoppable Now
- FluBot is back on the rise and is spreading across Europe rapidly, so it could soon reach the U.S.
- The particular malware remains pretty elusive thanks to the constantly changing C2 map.
- The Spanish police delivered a blow to FluBot distributors recently, but that wasn’t enough.
The Android malware known as ‘FluBot’ has been around since the end of 2020 and seems to be going through its best of times right now in spite of some hiccups it had two months ago. More specifically, back in March, the Spanish police raided some locations from where ‘FluBot’ distribution SMS originated and took down key distribution infrastructure. According to multiple reports from various sources, FluBot is spiking again, and its appearance in the United States is only a matter of time.
The actors use various lures to convince the recipient of their smishing messages to click on the included URL. In most cases, we see the impersonation of package delivery services since this is working so well today with everyone ordering goods online. For example, Italians are reporting phony DHL notices, whereas Germans are seeing FedEx messages.
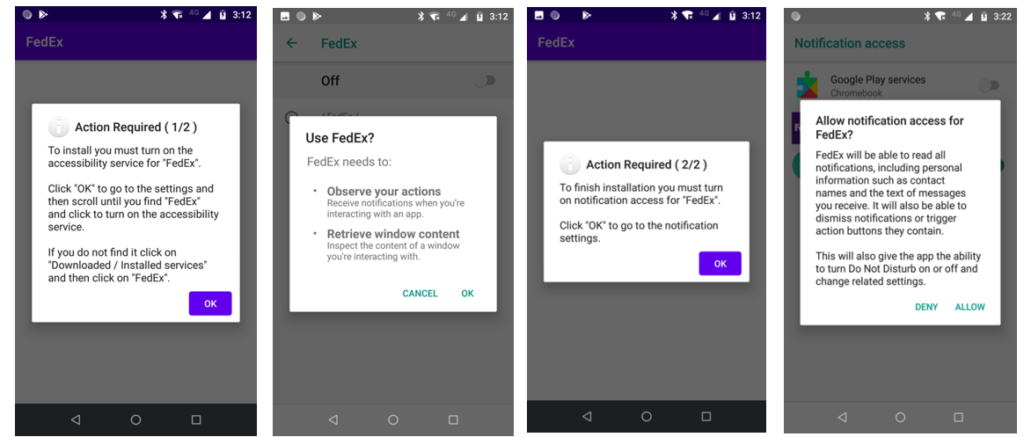
In all these cases, the recipient is informed about a parcel out for delivery and is offered a tracking link. The link leads to downloading an app, supposedly the service’s official tool, but in reality, it’s an APK carrying the FluBot malware.
If this stage is reached, the app requests Android Accessibility Service and Notification access, which most users will mindlessly grant, and FluBot can then begin its main operations. That could include credit card and banking credentials stealing, SMS spamming, exfiltration of the full contact list to the C2, SMS interception, app notification interception, browser page opening, disabling of Google Play Protect, and more. Pushing display overlays is also in the FluBot’s bag of tricks, which is just another way to steal valuable credentials from the victims.
The problem with FluBot, and the thing that makes it such a persistent problem, is that it is distributed on a humongous scale, but its C2 infrastructure remains constantly elusive. No doubt, its domain generating algorithm (DGA) system that helps it generate a list of domains and constantly switch C2 communication channels plays a crucial role in that part. In fact, this was one of the elements that got upgraded from version 3.7 to the current 4.0 version.
The question that arises is how one can protect themselves against all that. Here are some basic things you can do to stay safe from FluBot and any Android malware for that matter:
- Delete unsolicited SMS or emails that make strange or unexpected claims.
- Do not install apps from outside the Play Store.
- Do not grant app permissions willy-nilly. Pay attention to the requests and evaluate them.
- Use a mobile security solution from a reputable vendor.