New Android Malware Capable of Bypassing Two Factor Authentication
- A new type of Android malware can read your notifications and grab 2FA passwords.
- For now, the malicious apps concern Turkish crypto-currency platforms, but it could expand soon.
- The apps also try to steal the users’ login credentials by pushing a fake authentication form.
According to an ESET report by researcher Lukas Stefanko, there’s a new breed of malware lurking in the Google Play store, capable of bypassing SMS 2FA protection layers. These apps can reportedly access one time passwords via SMS or even email, without having the relevant permissions. The way these malicious apps achieve that is by stealing the one-time passwords from the notifications that arrive on the victim’s device, while they also take the extra step of hiding the notifications immediately so that the user won’t realize what happened. Long story short, the apps are reading the notifications, so they don’t need to intercept the SMS or email messages.
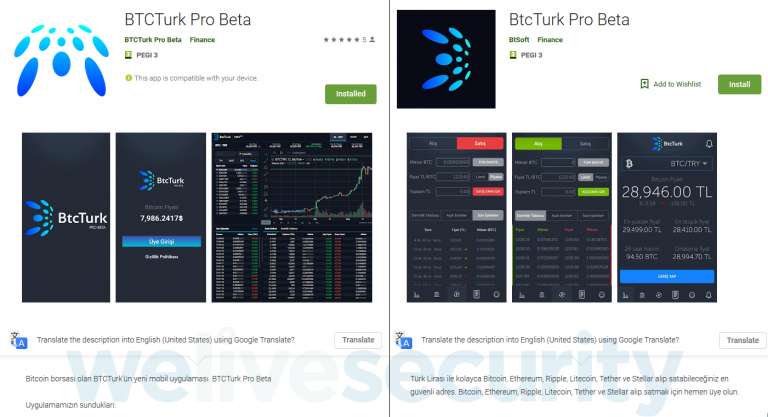
image source: welivesecurity.com
Google had established a more stringent approach with the SMS and Call Log permissions back in March, something that caused a headache to legitimate apps like ESET’s Mobile Security solution. This key change in the SMS permission policy has also driven crooks to find new ways to acquire those valuable one-time passwords, so here we are. According to Stefanko’s investigation, two apps that are already carrying these capabilities are the Turkish cryptocurrency exchange impersonating tool named “BTCTurk Pro Beta” which is apparently available by two different vendors, and another one called “BTCTURK PRO” which is a copy of the first. Another one that does the stealing but won’t follow with the notification dismissing is the “Koineks”, which is also focused on the Turkish crypto-currency scene.
All of these apps ask for “notification access”, which many users could perceive as a benign request. However, this permission grants them access to the content of the notifications displayed by any other app on the device, the power to dismiss them immediately, or even click on any links they may contain. The apps greet the user with a login page that will supposedly get them to the BtcTurk platform, but it’s only a phishing form which will send the login credentials to the attacker’s server.
If you want to stay safe against this type of risks, only download cryptocurrency apps from the official website of the service you wish to use, use a mobile security solution, and keep your Android as well as all apps up to date. The problem with this new malware that can read in notifications will definitely force Google to address it soon, but until then, it may find its way into a large number of applications in the app store. That said, you should be very careful with what you download and install on your phone, especially with the apps that ask you to grant them notification access permissions.
Have something to comment on the above? Feel free to do so in the section beneath, or on our socials, on Facebook and Twitter.