Android Cryptomining Trojan “UFO” Gaining Traction
- “UFO” tiny 200kb crypto miners is on the rise, driving Android IoT devices to their demise.
- Attackers use Coinhive to load mining Javascript code on a web browser page.
- The whole searching, targeting, infection, and mining process is getting streamlined, to the level of complete automation.
According to a Sophos Security report, the incidents of Android IoT (Internet of Things) devices getting infected by small but highly effective cryptocurrency miner applets are on the rise, as more and more hackers are looking to take advantage of devices that are left to do their own thing with minimal user monitoring. Such devices are casting dongles, smart TVs, smart speakers, central home controllers, and more. Those devices are connected to the internet and powered on at all times, so an attacker could exploit them by loading crypto miners and making money out of other people’s resources.
Android phones would be more ideal for this purpose since they pack more power, but the Android Debug Bridge sits behind the “USB Debugging” option that the user needs to enable on their own (tap “Build number” seven times to become a developer). However, Android IoT devices don’t have that layer, and attackers could push commands to them via known (or unknown) remote code execution vulnerabilities. According to the Sophos honeypot data analysis, this activity is currently on the rise and seems to originate from China, South Korea, Taiwan, Russian, Ukraine, Iran, the US, UK, and Sweden.
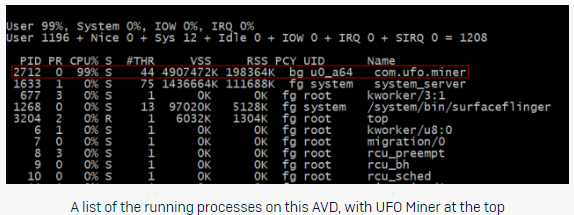
When the “UFO” crypto miners infects a device, the user gets no indication of the fact. There’s no app icon in the tray or a trace of any kind. However, and because “UFO” is exploiting 99% of the available resources, the device will get noticeably hot and painstakingly slow. The app utilizes the Coinhive service to embed a Javascript coin miner to a web page (run.html), using the Android Webview browser. According to the researchers, the creator of the UFO miner has actually set the CPU throttling at 80%, but the testing showed that this didn’t work for some reason as the mining load remained to 99%.
source: news.sophos.com
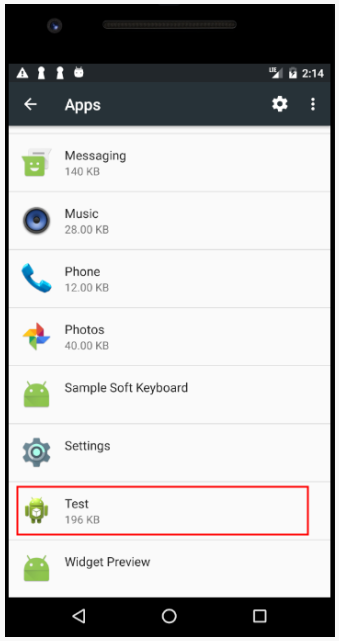
Having a coin miner running on your Android IoT device 24/7, squeezing its resources and getting it hotter than it’s meant to get means one thing, and that’s hardware decay and eventual failure. If the victim fails to notice the malicious activity for an extended period of time, which is often the case with this type of devices, it’s likely that the crypto mining will take its toll to it. Sophos researchers have found that all of the samples are currently named as “Test”, are of 200kb of size, and can be removed following standard procedures. A factory reset will also rollback the infection, while the blocking of access to “coinhive.com” on the network level would also prevent any exploitation from taking place.
source: news.sophos.com
Have you ever had an experience with an Android coinminer? Share the details with us in the comments section below, and also on our socials, Facebook and Twitter.