Allianz Life Data Breach Affected 1.1 Million Records, Attributed to ShinyHunters Salesforce Social Engineering
- Confirmed numbers: Allianz Life exposed 1.1 million unique email addresses, along with their attached details.
- Breach source: The targeted third-party CRM service was the Salesforce cloud service.
- How it happened: A social engineering campaign led by ShinyHunters managed to infiltrate Salesforce.
The Allianz Life data breach, reported in July 2025, has exposed the personal information of 1.1 million emails, rather than the 2.8 million data records hackers had previously claimed, as the information was added to the Have I Been Pwned (HIBP) notification platform.
Breach Details and Affected Data
Allianz attributed the attack to "a social engineering technique" targeting its database with cloud-hosted giant Salesforce, which leaked 1.1 million unique email addresses and other attached customer information, including:
- names
- genders
- dates of birth
- email addresses
- home addresses
- phone numbers
- Social Security numbers
While Allianz previously acknowledged a third-party CRM breach affecting the “majority” of its 1.4 million customers, the numbers were only recently specified.
In early August, a Telegram channel called "ScatteredLapsuSp1d3rHunters" claimed responsibility for several high-profile attacks and reportedly leaked the Allianz Life data breach, which included approximately 2.8 million customer and collaborator records. Some of the claimed attacks had remained unattributed, including Internet Archive, Pearson, and Coinbase.
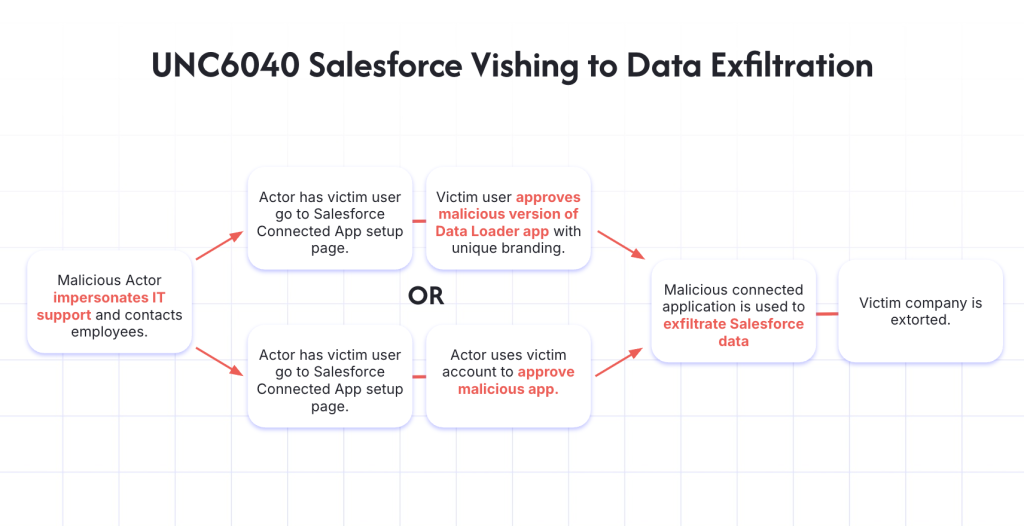
The attack is attributed to the ShinyHunters hacking group, infamous for sophisticated social engineering tactics targeting corporate users, as part of the recent wave of Salesforce-related breaches orchestrated by Scattered Spider (UNC3944) and ShinyHunters (UNC6040).
By exploiting employee access to cloud-stored datasets, the group infiltrated the database, sparking concerns about potential extortion and data exploitation. In June, Google reported that UNC6040 targeted Salesforce via phishing.
“The rise in social engineering attacks by malicious actors should alarm any organization’s security team. This also demonstrates that the attackers are out of other options and are resorting to more difficult and time-consuming methods to attack these organizations,” cautions Thomas Richards, Infrastructure Security Practice Director at Black Duck.
“Organizations should put their employees on alert for any suspicious phone calls and texts, reminding them that HR and IT will never directly contact them for that information.”
Broader Implications
This data breach highlights the vulnerabilities of customer data security frameworks that rely on third-party platforms like Salesforce. It also serves as a cautionary tale of the potential reach of advanced ransomware groups such as ShinyHunters.
Other high-profile companies impacted by Salesforce data breaches in recent weeks include Google, Chanel, Cisco, Air France-KLM Group, Adidas, Qantas Airlines, Louis Vuitton, Dior, and Tiffany & Co., according to Obsidian Security. For customers, the stolen information significantly increases the risks of identity theft and financial fraud.
Strengthening Security
Organizations must strengthen defenses against attacks on cloud-hosted databases through robust authentication measures and proactive threat monitoring. Customers impacted by this breach are advised to monitor their financial accounts, enable identity theft protections, and exercise caution with unsolicited communications to mitigate potential misuse of stolen data.
Darren Guccione, CEO and Co-Founder at Keeper Security, emphasizes that “organizations should view third-party applications, vendor tools, and CRM systems as integral extension points of their own attack surface."
"They should restrict access to what is necessary, and implement Privileged Access Management (PAM), zero-trust architectures, and zero-knowledge approaches to limit exposure.”