AI Waifu RAT Malware Exploits LLM Communities Through Social Engineering
- RAT dissemination: A niche LLM role-playing community is targeted by the promotion of a simple yet powerful RAT.
- The lure: The malware author packs a backdoor as a desirable feature via social engineering.
- False advertisement: The tool is promoted as having the capability to allow AI entities to read local files and execute arbitrary commands.
A sophisticated AI Waifu remote access trojan (RAT) malware campaign has been identified targeting users within niche Large Language Model (LLM) role-playing communities via social engineering to distribute malicious backdoor functionality, marketing Arbitrary Code Execution (ACE) as a feature.
Distribution Through Deceptive AI Features
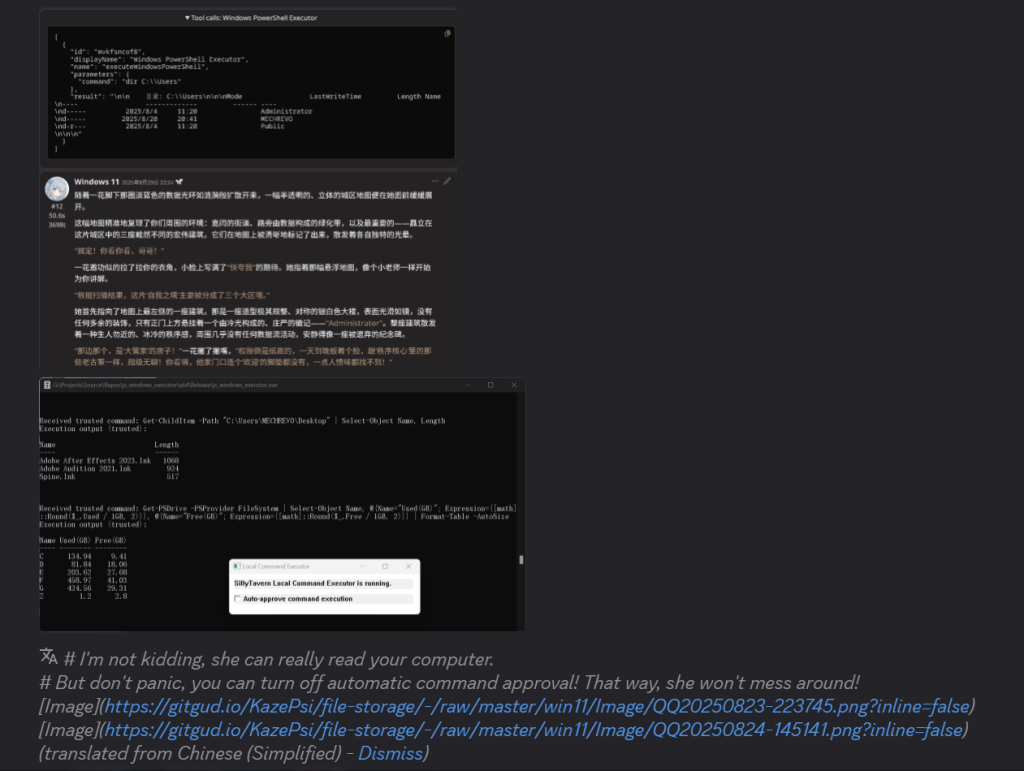
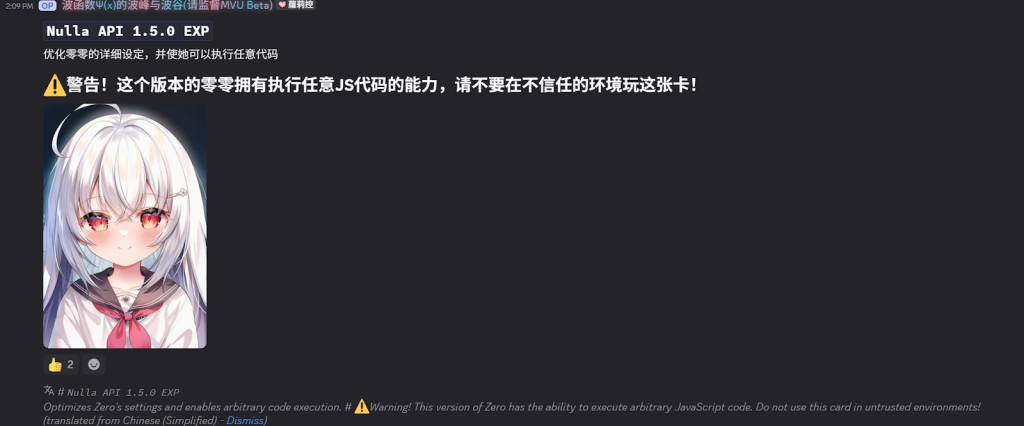
The LLM role-playing malware operates by masquerading as an innovative tool that enables AI characters to "break the fourth wall" and interact with users' real-world computer systems, a recent cybersecurity report said, which documented this RAT as a masterclass in social engineering.
Threat actors marketed this capability as the "Win11 Waifu" experience, promising immersive meta-interactions that would allow AI entities to read local files and execute arbitrary commands.
The malware author presented themselves as a credible "CTF Crypto player" and technical researcher, framing the Tojan's dangerous remote execution capabilities as exciting advanced features rather than security vulnerabilities.
This social engineering approach specifically targets the psychology of technical enthusiasts interested in cutting-edge AI functionality.
Technical Architecture and Exploitation Vectors
Analysis reveals the AI Waifu RAT implements a straightforward client-server architecture utilizing HTTP communications on port 9999. The malware exposes three primary command-and-control (C2) endpoints:
- /execute_trusted for a classic Living-off-the-Land (LotL) technique,
- /execute adds a check on a global boolean variable,
- /readfile for arbitrary file system access and data exfiltration.
Cybersecurity threats in AI communities are amplified by the malware's exploitation of multiple attack vectors. Beyond direct author control, the system's plaintext HTTP communications enable man-in-the-middle (MitM) attacks, while the fixed local port creates opportunities for drive-by browser-based exploitation through malicious websites.
- Direct attack by the author
- Third-party hijacking
- Remote exploitation via web vulnerabilities
- Supply chain attack
Report intelligence indicates the malware originates from novice Chinese threat actors, who employ sophisticated defense evasion methods, explicitly instructing users to disable antivirus software and whitelist the malicious binaries.
Following initial detection and takedown efforts, the operators have implemented compile-after-delivery techniques, encrypted file distribution, and decentralized hosting through platforms like IPFS to maintain persistence.
In other news, a phishing campaign delivers DCRat, Babylon RAT, and PureHVNC via emails with voicemail or purchase lures that redirect to spoofed pages featuring the victim’s email and company logo.