“Agent Smith” is a Silent Malware That’s Already Inside 25 Million Devices
- A new Android virus has already infected millions of devices, and no one realized.
- The malware named “Agent Smith” is a very silent app supplanter and ad pushing tool.
- The actors are already moving to their next campaign, following a kill switch logic.
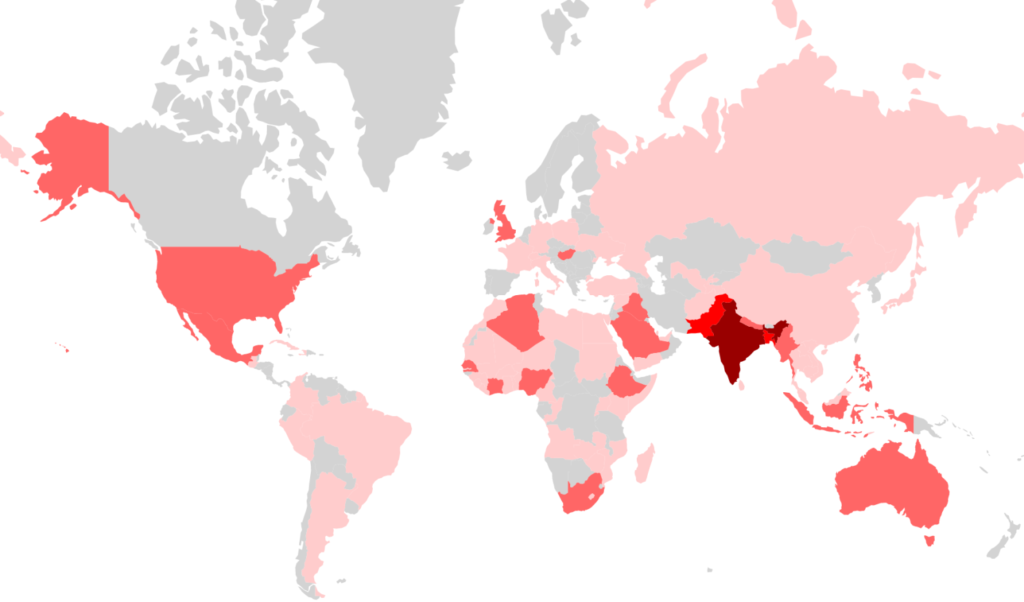
Five researchers of Check Point have recently discovered a new variant of a mobile malware tool that is using infection and multiplication techniques which won it the name “Agent Smith”. More specifically, this new malware has already infected 25 million devices without anyone noticing, as it gets disguised as a Google system app. Moreover, Agent Smith replaces other installed apps on the device with its own malicious versions, and for all that, it requires no user interaction whatsoever. So far, the targeting of Agent Smith seems to be focused on Pakistan, Bangladesh, and India, but it looks like there's already an opening towards the UK, USA, and Australia as well.
image source: research.checkpoint.com
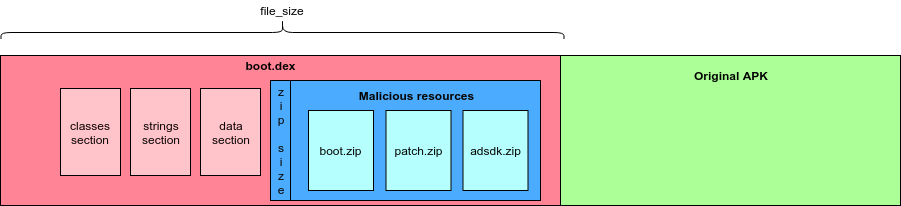
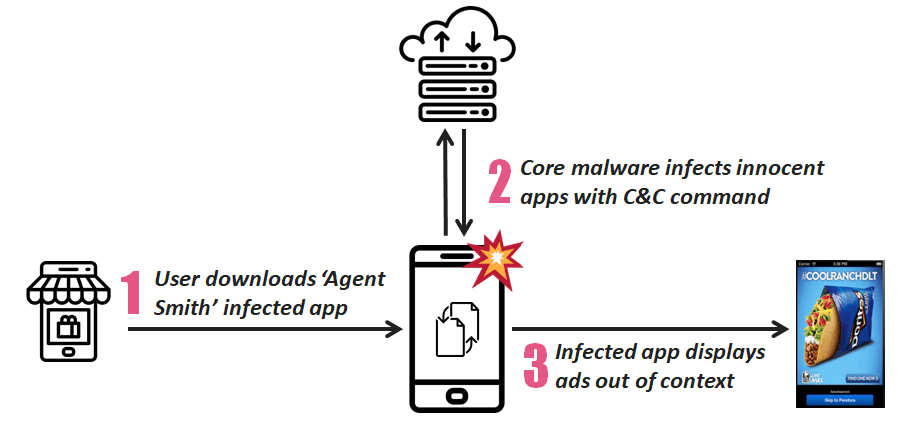
The infection starts by convincing the user to download and install a malicious APK from outside the Play Store. This is the dropper that is usually a photo app, a game, or an adult entertainment app. Once installed on the device, the dropper decrypts and installs Agent Smith which is immediately disguised as “Google Updater” and hides its icon entirely. The malware then extracts the app list to figure out what’s installed on the infected device, and then receives any correlations from its C2 server and replaces the apps with its own versions.
image source: research.checkpoint.com
These custom versions are downloaded and installed as updates, and their difference with the original apps is that they push ads for financial gain. However, and as the researchers point out, this is only part of the malware’s capabilities as the apps could easily be used for eavesdropping and banking credential theft. As users suddenly lose all original versions of their apps without having a clue about what could be the source of the ads, it would be very hard for the victims to realize what has happened on their device.
image source: research.checkpoint.com
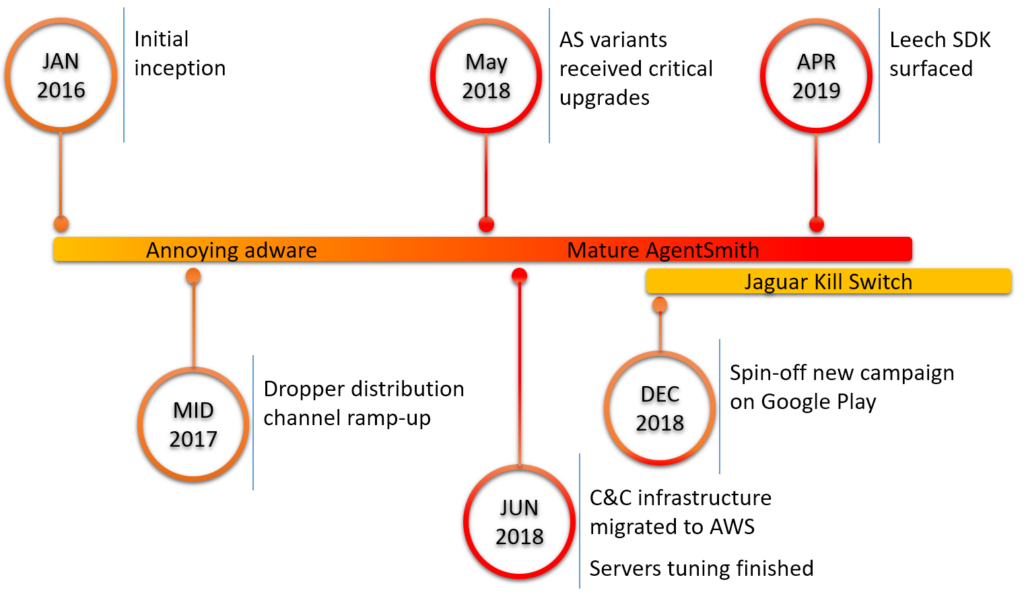
Check Point warns that while there are multiple dropper apps out there, the five most downloaded (7.8 million times) are the following: Color Phone Flash, Photo Projector, Rabbit Temple, Kiss Game: Touch Her Heart, and Girl Cloth Xray Scan Simulator. The researchers have also discovered that the actors have also planted the malicious SDK of Agent Smith on 11 apps that were available on the Google Play Store but have been removed upon their report. Moreover, the developers have already prepared their next step, which is a spin-off campaign called “Jaguar Kill Switch” because it follows a kill switch logic and replaces the ad serving action with more nasty payloads.
image source: research.checkpoint.com
By investigating the data that they had in their hands, Check Point researchers were led to a Chinese internet company that is engaged in Android app development and global promotion. The Guangzhou-based company even has a couple of now-expired job postings that seem to be relevant to the Agent Smith campaign, and not so closely related to their legitimate business.
Have something to comment on the above? Feel free to leave us your views in the section down below, or join the discussion on our socials, on Facebook and Twitter.