Agari Gave Phishing Actors Credentials to See What They Do
- Agari has conducted an experiment, seeding its credentials to 8,000 phishing domains.
- The actors were relatively quick to access the compromised accounts and did so through web browsers.
- Most of the actors are based in Nigeria, although the first stage of the phishing operation is supported by other countries.
Phishing is a standard method of tricking people into giving away their credentials by making them believe they’re about to login onto their accounts on a website that looks legit. It is a cheap, effective, and easy way for actors to steal accounts and access valuable information or systems/networks. Agari has decided to carry out an experiment to better understand how these actors move, so they seeded over 8,000 phishing sites with credentials under its control to see what they do.
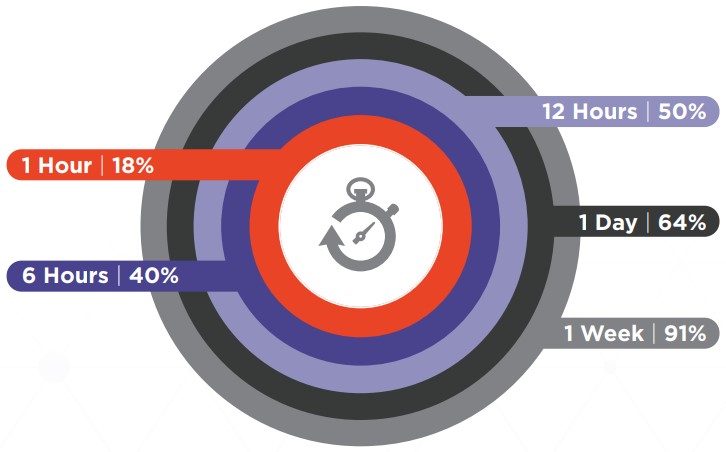
The first question is how quickly the actors would access the accounts they held the credentials for. As shown in the following diagram, half of the accounts were accessed within 12 hours of the phishing event, while 91% were accessed within the first week after the compromise.
In 18% of the cases, which is a significant percentage, the actors moved quickly and accessed the accounts within 60 minutes. All in all, victims of phishing attacks don’t have much time to realize what happened and reset their passwords before they lose access to their accounts forever.
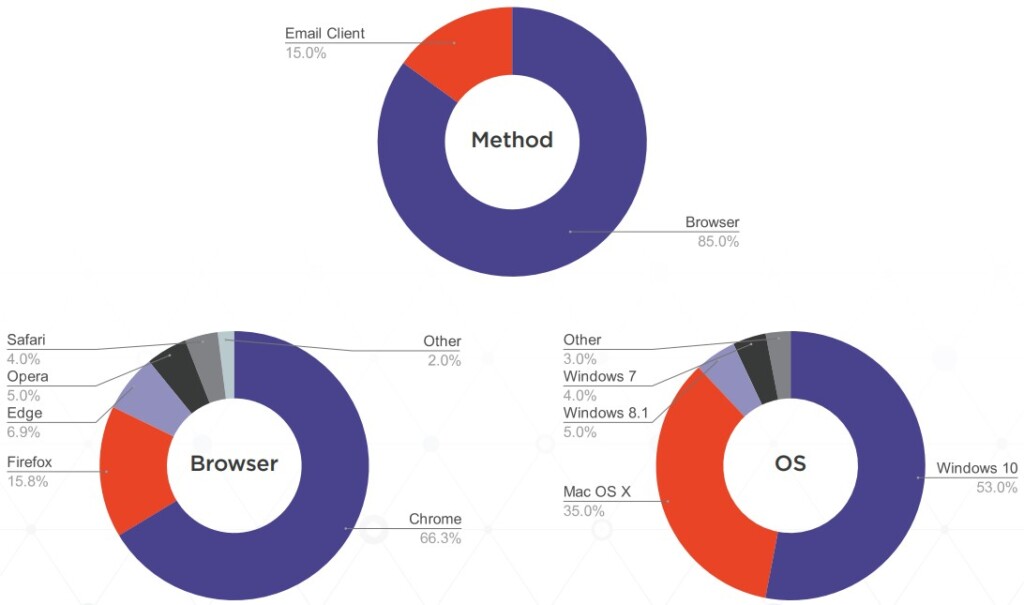
The second question is how the actors accessed the accounts. In the vast majority of the cases (85%), the phishing actors used a browser, while those who opted for an email client were few (15%). Notably, 35% of the phishing actors use macOS, which is much higher than the average market share for Apple’s OS. This tells us that crime pays well for phishing actors. And finally, a notable 4% is still using the outdated and insecure Windows 7.
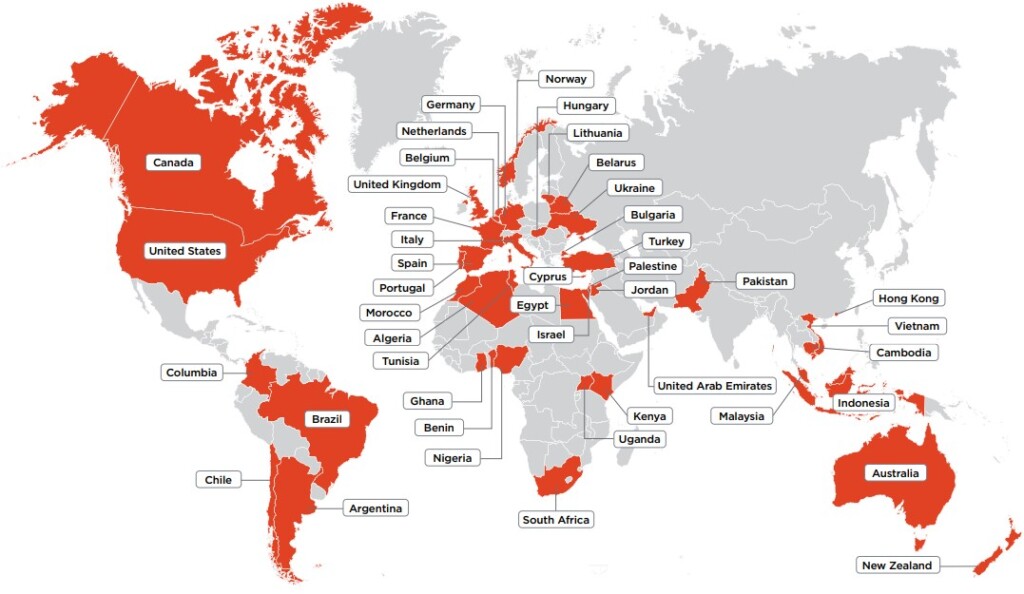
The third question is where the actors are located, although this is complicated due to the use of proxies and VPN tools. Agari clarified that only 25% of the actors didn’t use some form of a location-masking tool, and from the remainder, they were able to identify a small portion that had IP address leakage problems.
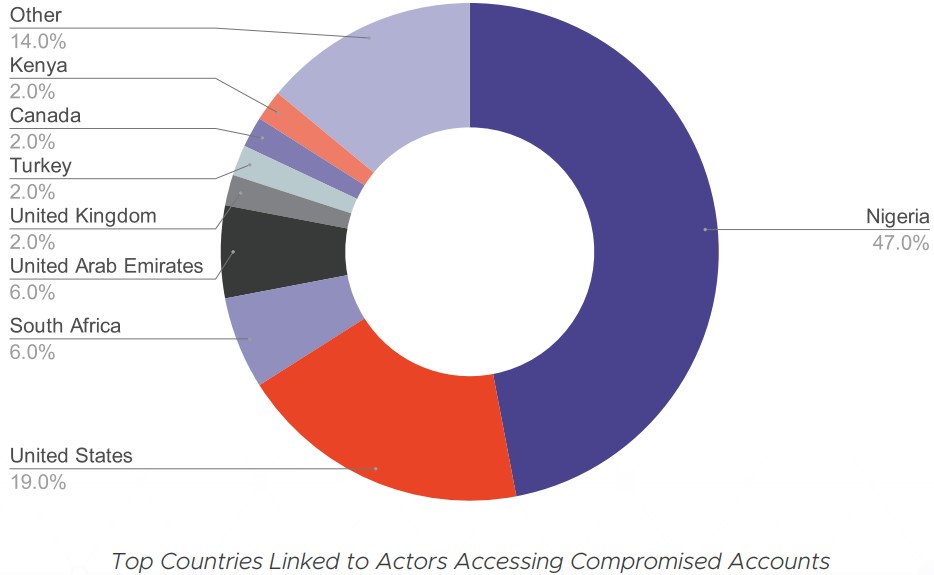
In summary, the researchers figured the real location of 41% of the actors, and interestingly, China, Russia, and North Korea aren’t even on the list. Those three are typically accused of hacking by western countries, but we can see that they are not involved in petty-level phishing.
The champion country for this is Nigeria, followed by the United States, South Africa, the UAE, the UK, Turkey, Canada, and Kenya. However, as the researchers point out, Russia, Eastern Europe, and North Africa still play a role in the phishing game, as they are usually involved in the initial compromise stage.