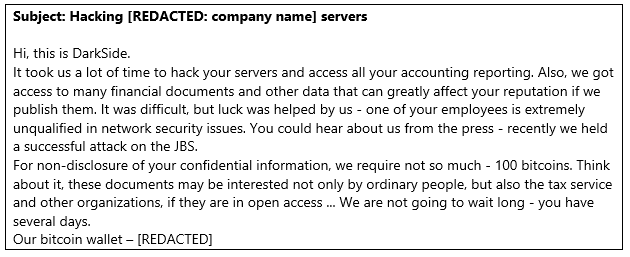
Actors Pretending to Be ‘DarkSide’ Target Large Food and Energy Companies
- A group of amateur actors is looking to cash in on the reputation of ‘DarkSide.’
- The actors send emails asking for 100 Bitcoin and threaten to release stolen data if they are not paid.
- There are no signs of cyberattacks, no proof produced, and even the details mentioned are false.
Such was the impact of the ‘DarkSide’ attack on the Colonial Pipeline that they gained widespread notoriety status across all industries. Crooks don’t like to leave elements of this type unexploited, so there’s a group that is now pretending to be ‘DarkSide,’ hoping that this will help them intimidate their victims and convince them to pay the requested ransom
As reported by Trend Micro, there’s a surge of large companies engaging in the food and energy sectors, who claim to have received threatening emails from a sender who claims to be ‘DarkSide.’
The crooks demand the payment of 100 Bitcoin in ransom - otherwise, they threaten to release sensitive information that they supposedly stole during a cyberattack onto the recipient’s network. The distribution of these emails begun on June 4, 2021, and it’s ongoing. In some cases, the actors have used the contact forms that are available on the company websites, but they were careful enough to use Tor and mask their real IP address.
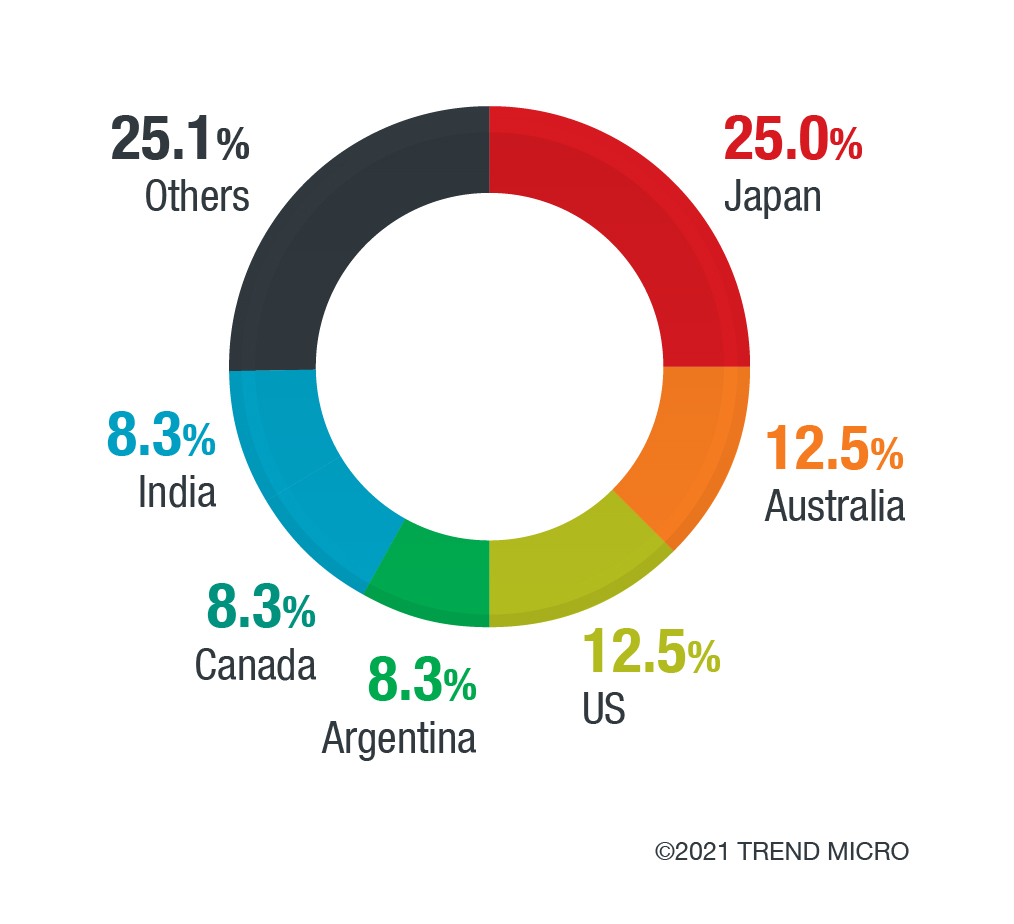
The largest volume of messages was sent to companies that reside in Japan, with Australia, United States, Argentina, Canada, and India following with significant shares too. Japanese companies aren’t easy targets to extort and convince to pay the ransom, so this is a weird choice of focus for these actors. In fact, TrendMicro says the one and only Bitcoin wallet address used in all threatening emails hasn’t received any payments yet.
The aspect of the cyberattack isn’t confirmed by anything, be it proof of stolen data or signs of system interruption through ransomware encryption. To make their bogus claims even more obvious, the actors messed up heavily by presenting the recent attack against JBS as their work, whereas this was attributed to REvil, a totally different ransomware group. So, in summary, this is pretty amateurish and certainly very hard to convince someone to hand over such a significant amount of money.
Still, this doesn’t mean that it couldn’t be an example for other, more diligent actors to follow, or maybe a method that could be used at a wider scale and against smaller entities that are more likely to get tricked. Right now, all of the tricky emails arrive from either “darkside@99email[.]xyz” or “darkside@solpatu[.]space”, so if you got one, feel free to disregard it.