Actors Are Exploiting 0-Click Apple Mail Vulnerability Leading to RCE
- Researchers warn about a nasty flaw in Apple Mail, which is triggered by large email messages.
- The attack is pretty stealthy, while its success depends on the device specs and iOS version.
- Users are advised to use the latest iOS beta, or simply to use Gmail or Outlook for a while.
ZecOps researchers have discovered a vulnerability on iOS that involves the sending of an e-mail to trigger a remote code execution condition. The attacking potential spreads over two bugs, one that concerns an out-of-bounds write (OOB) and one that involves a heap-overflow flaw. The discovery happened on February 19, 2020, and by March, ZecOps had shared all possible triggering scenarios with Apple. The iOS maker patched the flaws with version 13.4.5 beta, but since some older devices are not eligible for the reception of this version, they will remain vulnerable to the discovered RCE flaws.
Unfortunately, both vulnerabilities have been exploited in the wild, first spotted targeting Apple E-mail on iOS 11.2.2 in January 2018. The researchers have recorded attacks against a Fortune 500 organization in North America, an executive from a carrier in Japan, a VIP from Germany, a European journalist, an executive from a Swiss enterprise, and MSSPs from Saudi Arabia and Israel. A specific threat actor launched the attacks, so this is not something that concerns every iOS user out there, but it is still a highly critical and potentially dangerous vulnerability.
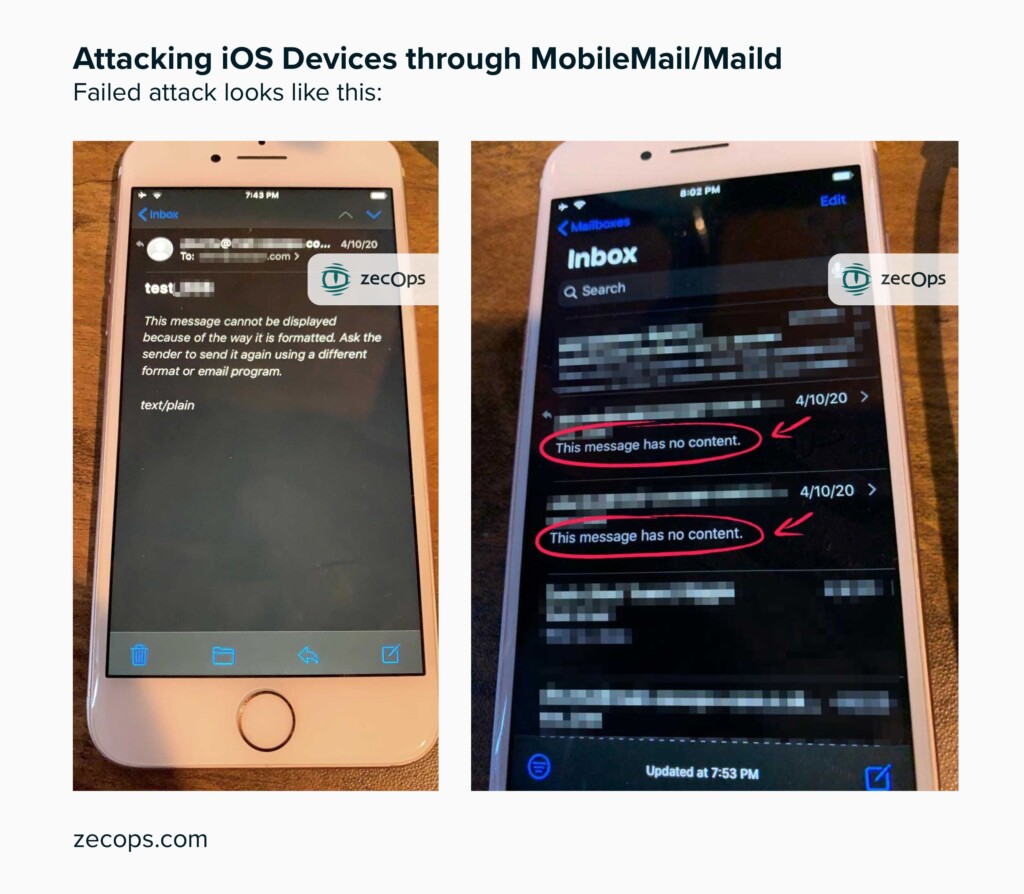
If you can’t update to iOS 13.4.5 beta, you are advised to use Gmail or Outlook instead of Apple E-mail, as these e-mail apps aren’t vulnerable. Triggering the flaws would cause a temporary slowdown of the Apple Mail app or even its crash. Besides that, nothing else would be noticeable, which makes the attack pretty stealthy. In the case of failed attacks, the target would get an error message, saying “This message has no content.” The trick to making the attack successful is by sending a message that will cause an inability to handle the return value of system calls correctly.
Source: ZecOps Blog
The researchers found that using a large enough e-mail would trigger the flaw, but using multi-part messages, RTF, or mixed formats would also work out. Naturally, the less physical RAM and virtual memory space a device has, the higher the chances of the attack being successful. For example, an iPhone 6 with 1GB of RAM, or an iPhone 7 with 2GB would be easy targets. Also, in iOS 12, the Mail app is using a single process for all data streaming, so the virtual memory space is even more confined and susceptible to exploitation. In iOS 13, Mail got a dedicated channel for parsing e-mails, so it is somewhat better protected, albeit still vulnerable.
In conclusion, it is important to clarify that the attackers would need to exploit a kernel bug to take full control over the target device. The above vulnerabilities would only allow the leaking, modification, or deletion of e-mails on the target device, but this would be more than enough in cyber-espionage operations anyway. On iOS 12, the victim must click on the e-mail to trigger the flaws, while on iOS 13, no clicking is required. Depending on what hardware and software you’re using, beware of the risks and take whatever risk-mitigating steps you can. If you're using an older iPhone device, maybe it's time to upgrade.