Academics Utilize NFC to Generate Fake Taps on Android Phones
- Researchers from Tokyo have managed to generate fake taps on Android devices.
- By using a signal generator, they could induce electric signals that tricked the screen into registering ghost taps.
- The method doesn’t work on all Android phones but it could be used on ATMs and voting terminals as well.
Researchers from the Waseda University in Tokyo have managed to exploit the NFC (Near Field Communications) module that lies inside most Android phones today, to generate fake 'ghost' taps on the screen without the user being able to realize anything. The main scenario of the attack, as demonstrated through the following video, would be to display a dialog on the phone and then generate a fake tap on an unsafe choice no matter where the user’s finger is pointing. This could lead to unwillingly connecting to a precarious Wi-Fi network, grand approval to risky permissions, pair with a malicious Bluetooth device, and many more exploitation scenarios.
The testing rig that the three academics built consists of a 5mm thick copper sheet that is connected to a DDS signal generator, a Raspberry Pi computer, a high-voltage transformer, an NFC reader/writer, and a battery pack for the system to operate. The researchers claim that the whole attack rig can be compacted and placed inside a coffee table or a surface where people may put their smartphones on. The NFC range is between 4 and 10cm, so as long as the contraption and the smartphone are within this distance, the exploitation can work.
Image source: zdnet.com
As long as the NFC functionality on the smartphone is enabled, the phone continuously monitors nearby transmissions, as it should be, but this creates the security problem. The attack rig sends specially crafted electrical signals to the smartphone’s capacitive touchscreen, which basically generates fake taps either horizontally or vertically. As there is no cursor, the user cannot possibly realize what is happening, and the hijacking of the user taps occurs in a stealthy and ghost-like manner.
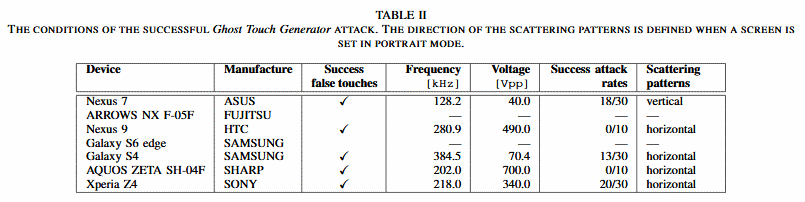
By testing this method against seven different smartphones, the researchers have realized that each device has different operational frequency and voltage ranges. This means that in order to carry out a successful attack against a device, one would need to configure the attack rig to match the technical requirements of the target model. In two cases concerning Samsung and Fujitsu screens, the false tapping attacks failed, so this is not a universally successful exploitation method.
Image source: zdnet.com
It is also important to clarify that the particular attack method is not only effective against NFC-enabled smartphones but any device with a capacitive touchscreen. This includes ATMs, voting machines, and other types of mission-critical devices that should ensure the users’ protection against tap hijacking attempts. That said, the Japan Computer Emergency Response Team is already working on notifying the screen manufacturers of this new type of exploitation, so hopefully, there will be mitigation measures rolled out soon.
Do you keep your smartphone’s NFC enabled, or do you prefer to have it disabled for security reasons? Let us know in the comments down below, and also on our socials, on Facebook and Twitter.