Abusive MSI Packages Download and Execute Malware Scripts
- Researchers notice a rise in the spreading of malicious MSI files with malware-dropping instructions.
- The actors are currently targeting people from Brazil and Portugal, trying to grab financial details.
- The malicious packages pretend to come from reputable vendors, and in some cases, they are digitally signed.
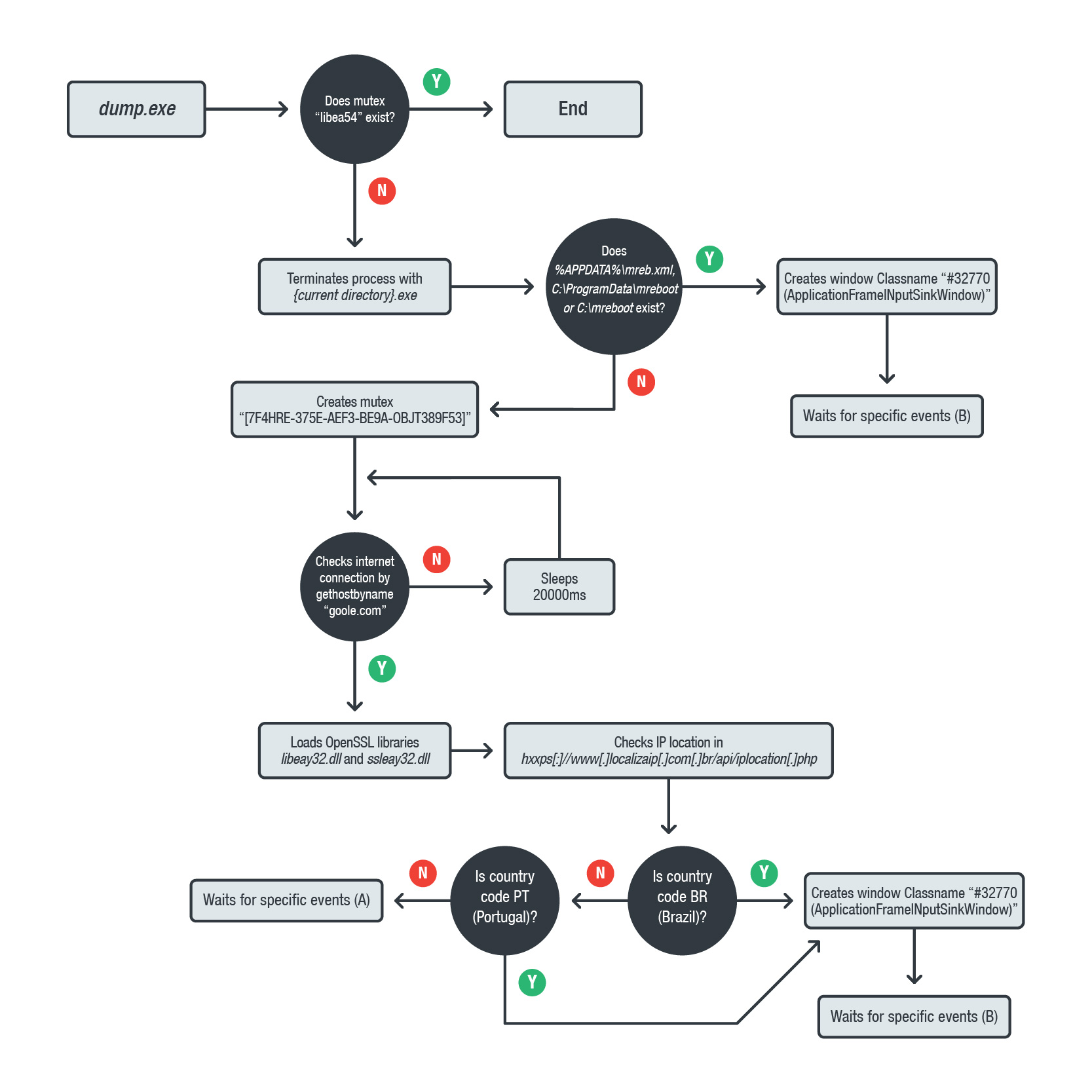
As reported by Trend Micro, there is a recent trend of spreading abusive MSI (Microsoft Software Installation) package files that were specifically created to pass malicious instructions that lead to the downloading and execution of malware. The various scripts that have been analyzed by the researchers can perform system shutdown, drop malware, and execute various types of custom code. The plethora of abuse is complemented by instructing the file to run code from local sources, a remote source, a streamed target, or a downloaded script. The malicious actors seem to have many options of malpractice through the peculation of the Windows MSI system, so there’s a wide range of exploitation possibilities.
One aspect of the malicious MSI files that Trend Micro considers to be a key in the effectiveness of these campaigns is the fact that they are bundled with elements that give them a certain level or type of legitimacy. For example, the researchers noticed that the trojan files contained in one of the malicious “.zips” that are downloaded by the MSI packages are digitally signed by Avira. Another characteristic that pertains to the same fake legitimacy image is the pretension of the files to be “Adobe Acrobat Research DC” components.
While there is a galore of malicious activity that can be recorded and ascribed to malicious MSI package files, the main targets of the actors seem to be the banking and financial information of their victims, sometimes achieved via keystroke capturing as well. Based on the language used in the spam email, the site redirection localization, and the self-checks conducted by the malicious scripts, the actors are currently targeting people from Brazil and Portugal. However, the same practices could be used to target other countries as well, since the principle would be exactly the same.
image source: blog.trendmicro.com
All that said, and since the problem lies in the MSI package installation system, the question that arises is what we can do to protect ourselves from this type of attacks? Besides using AV solutions from reputable vendors, you should abide by the following general “good practice” rules:
- Do not ever install MSI files that were downloaded from unknown and obscure sources.
- Update your software tools as well as the operating system as soon as a patch is rolled out.
- Execute MSI files in the constraints of a sandbox to detect possible system manipulation attempts.
- Prefer downloading and using “.EXE” files when possible.
Have you ever had a nasty series of events unfolding in your system following the installation of an MSI file? Share the details with us in the comments down below, and help us spread the word by sharing this post through our socials, on Facebook and Twitter.