A British Security Company Leaks Five Billion Records Online (Update)
- A UK security firm has exposed 5.5 billion records online via an unprotected database.
- The data concern known and previously disclosed leaks that were used for security purposes.
- This incident still could have given actors the opportunity to steal "cleaned" and organized dumps.
Researcher Bob Diachenko has found yet another unprotected Elasticsearch instance online, containing a collection of reported data breaches. In total, the leaking database contained more than five billion records laid out in a well-structured form, with the cluster having two collections given the name “leaks_v1” and “leaks_v2”. So, it appears the company that managed the database had collected these records from security incidents that occurred between 2012 and 2019, then organized the data, and stored it for their own purposes. The main problem here is that the security firm leaked the data again, and these records were reintroduced online in a form that hackers would celebrate to have.
The owner of the database is a British security company dealing with threat intelligence, incident response, and phishing simulation. The database was first indexed on March 15, 2020, and Diachenko found it a day after. He alerted the company immediately, but they did not respond quickly to acknowledge the incident. Still, the database went offline within an hour following the notification, so the impact of the re-exposure was at least kept to a minimum.
How about that? A UK-based security company inadvertently exposed its 'data breach database' (which was probably part of their threat intelligence solution) spanning 2012-2019 era, with around 5.5B+ records. Now secured. No response. Story in progress.
— Bob Diachenko 🇺🇦 (@MayhemDayOne) March 17, 2020
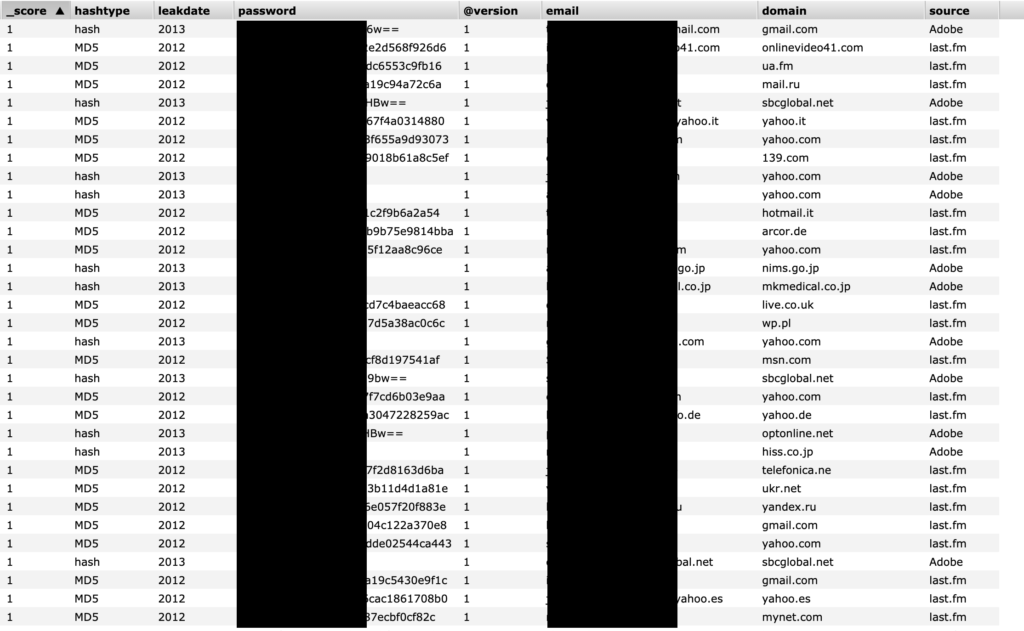
The types of data that was included in each data entry were the following:
- hashtype (the way a password was presented: MD5/hash/plaintext etc.)
- leak date (year)
- password (hashed, encrypted or plaintext, depending on the leak)
- email domain
- source of the leak
Source: Security Discovery
The most prominent sources of leak that the researcher could confirm by analyzing the data were: Adobe, Last.fm, Twitter, LinkedIn, Tumblr, and VK. It is almost certain that there are more notable leak sources in there, but analyzing 5.5 billion records isn’t exactly a walk in the park. That is especially the case when one of the collections, “leaks_v2”, was updated in real-time, being fed with more data from leaks that occur. Possibly, the security company is monitoring dark web marketplaces and forums, grabbing dumps, and adding them to their database. Hopefully, they do it for research, reporting, and protection purposes. Allegedly, no customer data had been exposed or breached.
Although the firm maintains an active presence on social media, they have made no statements about the discovery. There’s an ample amount of irony going on here, as a security firm should know better when it comes to protecting Elasticsearch instances. Even if the exposed information isn't fresh, re-leaking it in a very usable form is a mistake that we would expect a different kind of entity to do.