New Trickbot Campaign Distributing Phishing Emails via Legitimate Cloud Services
- One of Trickbot’s latest variants is circulating once again via payroll-themed phishing messages.
- The actors are using a legitimate email delivery and cloud document hosting services for obfuscation.
- The recent campaign has claimed hundreds of victims, infecting the host systems with the popular credential stealer.
Unit 42 researchers have captured the signs of a new Trickbot campaign that is using legitimate cloud service providers to obfuscate the delivery of malicious emails to prospect victims. Trickbot has been around since 2016, and it’s one of the most widely-used and successful credential stealers out there. Actors are still deploying it as it remains highly versatile in its functionality and capabilities. From worming to email inbox parsing, and from modular setups to network reconnaissance, Trickbot is a nasty type of infection that is hard to deal with once it finds its way in.
Source: Unit 42
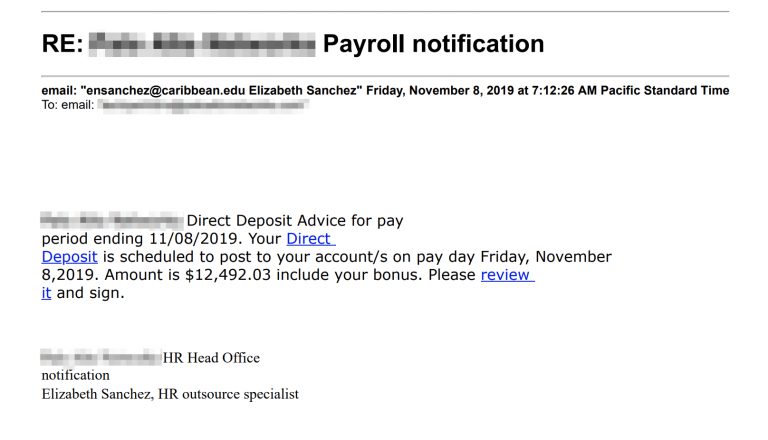
This latest campaign that was discovered by Unit 42 culminated between November 7 and 8, with the period of the campaign spanning between November 4 and 22, 2019. The subject lines of the phishing emails concern payroll topics, payment bonuses, and relevant notifications. Surely, promising money to the victims is a great way to bait them to download the malicious document attachment. In this particular case though, the documents were hosted on Google Drive, and the email delivery service that was used is "SendGrid". This helped the phishing actors achieve a high level of much-needed obfuscation, hiding the malicious URLs behind layers of apparent legitimacy.
Source: Unit 42
The sender uses compromised ".edu" email addresses which aren’t very convincing in the context of payrolls, but they add some credibility in general. Thanks to SendGrid’s "click tracking" features, the actors know when the recipient clicks on the sent link, and when the Google Document is downloaded from the Google Drive. This document is the actual payload downloader, which retrieves the Trickbot from the C2 infrastructure and executes it. The researchers have identified two documents/downloaders that are used in this campaign, both signed by "PERISMOUNT LIMITED". While these files appear with the document icon on Windows, they are actually executables.
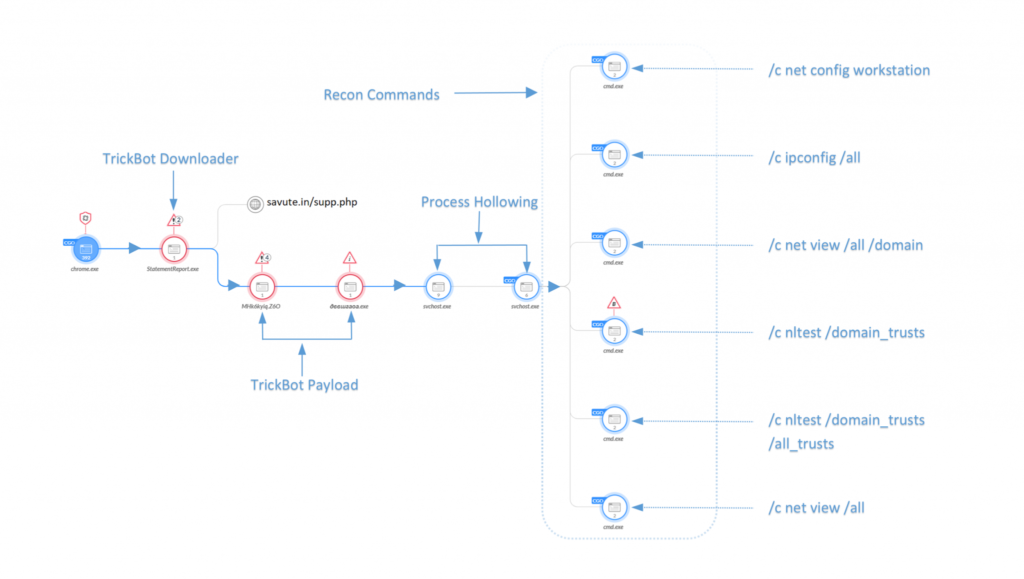
As for the payload itself, the Trickbot variant that was used is one of the newer versions, capable of "process hollowing" functions. The payload carries the name "erfd1.exe", or "SetupDesktop.exe". According to the data that Unit42 could generate by monitoring the campaign, the scale of the infections is already measured in the hundreds. As for the URLs that you should avoid clicking, these are the following: "savute[.]in/supp.php", "lindaspryinteriordesign[.]com/supp.php", "maisonmarielouise[.]org/supp.php", "clementeolmos[.]com/supp.php". As always, make sure that you’re using a robust AV tool that is up to date, apply OS security patches, and don’t trust unsolicited email messages no matter what claims they make.
Have something to comment on the above? Feel free to do just that in the section down below, or on our socials, on Facebook and Twitter.