The Waterbug Cyberespionage Group is Using New Tools Against Governments
- Waterbug returns with a new toolset, and new infrastructure hijacking tricks.
- The cyberespionage group has launched three successful attacks using a wide range of new backdoors.
- Waterbug is also riding the 'living off the land' wave, as it keeps them hidden and dangerous.
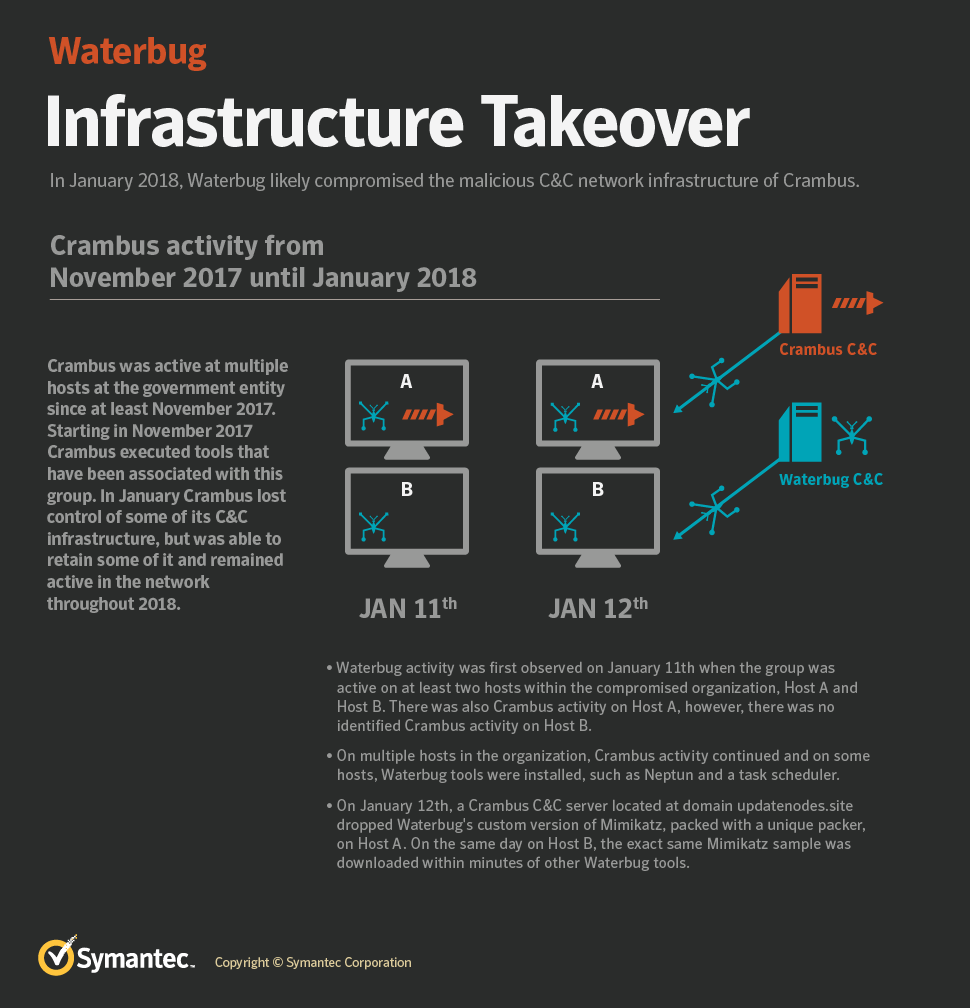
Symantec reports that the Waterbug cyberespionage group is currently using a new toolset, something that they observed during the group’s most recent attacks against Middle Eastern governments. The group has launched three attacks lately, which combined several new backdoors while also using infrastructure that is thought to belong to another hacking group. One new backdoor by Waterbug is the 'Neptun', which targets Microsoft Exchange servers and is a hard-to-detect malware that can download additional files, execute shell commands, and send stolen data to its C2 server. The Neptun attack involved infrastructure belonging to the Crambus (OilRig, or APT34) group.
Image source: symantec.com
Could this be a case of hijacking another group’s infrastructure to hide their tracks? As the evidence points, this is entirely possible. Besides the infrastructure, Waterbug used a custom version of Mimikatz which was downloaded from Crambus' very own Poison Frog control panel. Symantec also explores the possibility of this being a 'false flag' attempt to try and confuse the investigators by compromising Cambus’ systems and creating a disturbance. Another plausible scenario is that Waterbug compromised Crambus simply to gain quicker access to organizations that Crambus had already hacked.
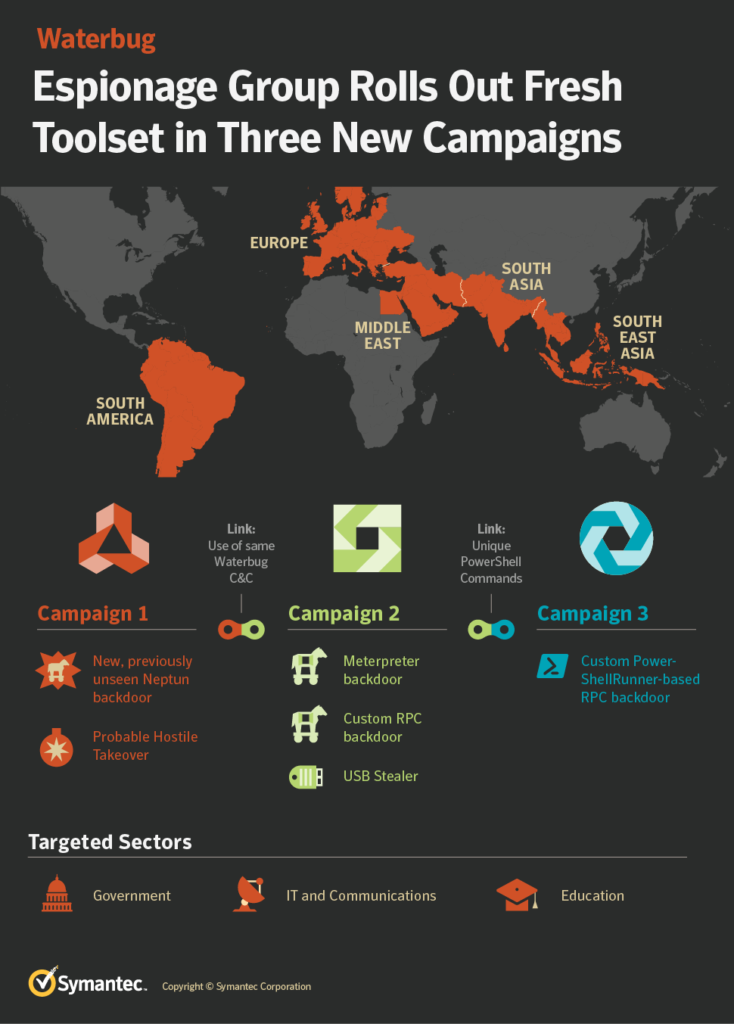
In the other two recent attacks, Waterbug used the Meterpreter and the RPC (remote procedure call) custom backdoors. These are based on publicly available tools that Waterbug modified as required. Meterpreter is disguised as a .wav audio file, while the RPC loader can execute the malicious code without invoking the powershell.exe, thus avoiding detection from AV tools. The scripts are hidden in the registry and are encoded with Base64. The following image gives an overview of Waterbug’s latest activities.
Image source: symantec.com
Waterbug is following the “Living Off the Land” trend which makes the attacks cleaner, harder to detect and stop, and generally leave fewer traces for investigators. By using PowerShell scripts, PsExec, and Microsoft Sysinternals extensively, the group is conducting file-less attacks and uses system tools as backdoors, which increases the level of stealthiness. In this context, Waterbug is using the same tools as many other cyber-espionage groups, like the Mimikatz for credential theft, the Certutil for file retrieval and decoding, the IntelliAdmin for RPC command execution, and the Sscan and NBTScan for network exploration.
Symantec attributes multiple attacks to the group, including 13 organizations across ten countries. Mostly, the attacks targeted ministries, IT organizations, and government agencies in the Middle East, South Asia, Europe, and Latin America.
Have something to say on the above? Share your views in the comments down below, or on our socials, on Facebook and Twitter.