Adidas Data Breach Investigation Underway Following Third-Party Intrusion Claims by Lapsus$ Group
- Partner Compromised: Adidas confirmed it is investigating a potential data protection incident affecting an independent licensing partner and distributor, though its own systems remain secure.
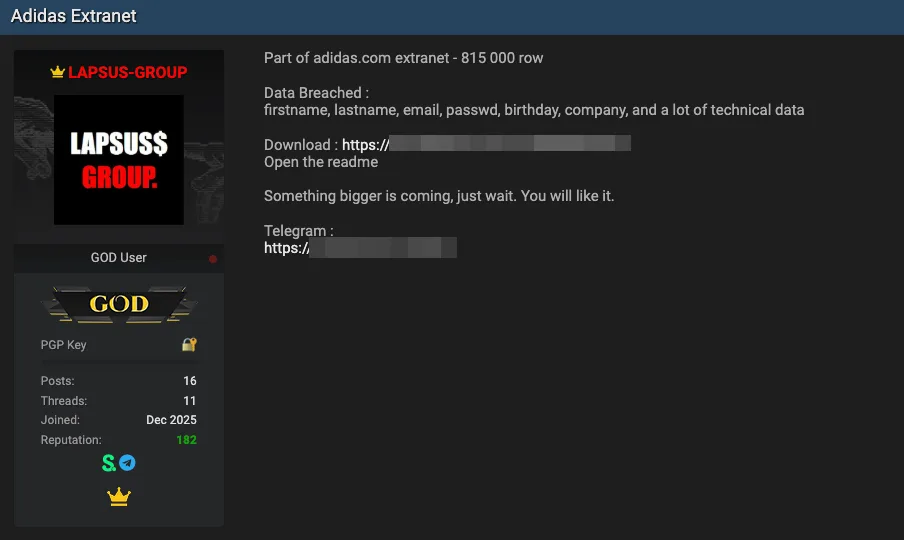
- Hacker Claims: A threat actor claiming to be the Lapsus$ Group alleges they have stolen 815,000 records, including customer PII and technical data, from the company's extranet.
- Data Exposure: The leaked data reportedly includes names, emails, passwords, and sensitive technical information, marking another security challenge involving third-party vendors.
Adidas is investigating allegations of a significant data breach involving one of its external partners. The German sportswear giant confirmed that it was made aware of a "potential data protection incident" at an independent licensing partner responsible for martial arts products.
The investigation was triggered after a user claiming affiliation with the notorious Lapsus$ group reported compromising the company's extranet. The company emphasized that its own IT infrastructure and consumer e-commerce platforms were not affected.
Lapsus$ Group Claims Responsibility
On February 16, the threat actor posted on a dark web forum, asserting they had exfiltrated approximately 815,000 records. The stolen files reportedly contain sensitive personally identifiable information (PII), including:
- First and last names,
- Email addresses,
- Passwords,
- Company names,
- Birthdays,
- Unspecified technical data.
This ransomware group, often associated with high-profile attacks on major tech firms, has recently been linked to collaborations with other cybercriminal entities, including Scattered Spider and ShinyHunters, to form Scattered LAPSUS$ Hunters, a new extortion-as-a-service alliance.
Supply Chain Vulnerabilities and Data Protection
Supply chain attacks have become a favored vector for cybercriminals, allowing them to bypass the hardened defenses of primary targets by exploiting third-party partners, often via social engineering. As global enterprises rely more heavily on interconnected networks of distributors and licensees, ensuring rigorous security standards for all partners is becoming essential to prevent data leakage.
This event follows a similar security lapse in May 2025, in which Adidas notified customers of data theftat a separate service provider. In November 2025, security researchers observed Scattered Lapsus$ Hunters impersonating Zendesk in a phishing campaign to steal credentials.
Last month, ShinyHunters were suspected of being behind an Okta SSO accounts vishing campaign using custom Phishing-as-a-Service kits.