Threat Actors Target Iran Protest Supporters with New Malware in Cyberespionage Campaign
- New Malware: A cyberespionage campaign targeting supporters of Iranian protests is deploying a previously undocumented malware strain designated CRESCENTHARVEST.
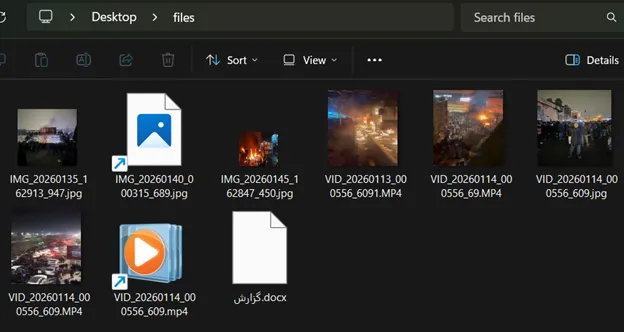
- Attack Vector: The malware is distributed through files bundled with legitimate protest footage, employing social engineering tactics to execute the malicious payload.
- Suspected Origin: Security researchers attribute the campaign to Iranian-aligned threat actors, architected to conduct surveillance operations against Farsi-speaking individuals in diaspora communities.
Supporters of Iran's anti-government protests are actively targeting via a sophisticated cyberespionage campaign that deploys a newly identified malware strain. The campaign debuted in early January, leveraging information scarcity caused by nationwide internet infrastructure disruptions.
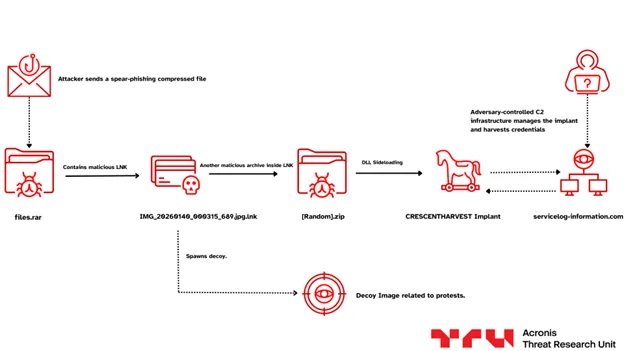
Threat actors are distributing weaponized files masquerading as legitimate protest videos and intelligence reports. These vectors deliver an advanced malware variant, CRESCENTHARVEST, engineered for comprehensive data exfiltration.
CRESCENTHARVEST Malware Capabilities
The CRESCENTHARVEST malware functions as a hybrid remote access trojan (RAT) and infostealer, according to threat intelligence analysis from Swiss cybersecurity firm Acronis. Upon successful deployment via DLL sideloading using a signed Google executable file, it maintains persistent access for remote command execution.
The implant hardcodes and organizes paths at startup, establishing a structured and modular command-and-control (C2) framework, allowing the threat actor to “remotely control individual capabilities and selectively activate data collection, reconnaissance or persistence features.”
Target data includes stored browser credentials, browsing history artifacts, and Telegram sessions. Researchers concluded these capabilities indicate development by Iranian-aligned advanced persistent threat (APT) actors.
Cybersecurity for Activists and Targeted Groups
Considering the telecommunications infrastructure restrictions implemented within Iran, security researchers assess that the campaign primarily targets Farsi-speaking Iranian nationals residing in foreign jurisdictions, along with journalists and human rights activists monitoring protest developments.
The report suggests the primary infection method may be spear-phishing or protracted social engineering to establish trust before payload delivery.
In other recent news, a high-speed ClickFix campaign delivered Matanbuchus 3.0 Malware and the new AstarionRAT. Earlier this month, cybersecurity researchers observed state-aligned actors exploiting Iranian protest unrest in a RedKitten AI-accelerated campaign