SystemBC Infections Exceed 10,000, Including Systems Linked to Government Hosting
- Global Scale: Silent Push analysts identified more than 10,000 unique IP addresses infected with SystemBC malware, with the highest concentrations in the U.S., Germany, and France.
- Government Targets: The investigation revealed infections within sensitive infrastructure, including IP addresses hosting government websites in Burkina Faso and Vietnam.
- Evolving Threat: A previously undocumented SystemBC variant written in Perl was identified, targeting Linux systems and indicating continued development.
Silent Push has released new findings regarding the SystemBC botnet, identifying over 10,000 infected IP addresses worldwide. Although Europol's Operation Endgame disrupted the malware's infrastructure in May 2024, recent analysis confirms that SystemBC, also known as Coroxy or DroxiDat, remains highly active.
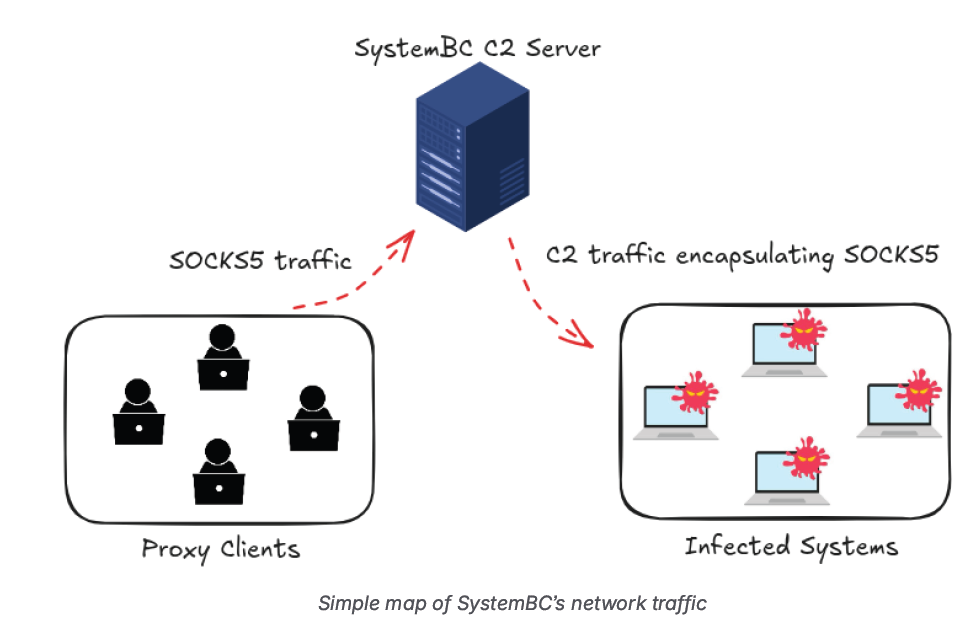
The malware functions as a multi-platform proxy that converts compromised systems into SOCKS5 proxies. These proxies are frequently used by threat actors to obfuscate malicious traffic and maintain persistent access to victim networks, often serving as a critical precursor to ransomware.
New Perl Variant Targets Linux Systems
A significant discovery in the report is the identification of a novel SOCKS5 proxy malware variant written in Perl. This previously undocumented iteration is designed to infect Linux systems and has shown zero detections across major antivirus engines.
The Perl variant is delivered via a dropper that hunts for writable directories before deploying hundreds of embedded payloads. This evolution suggests that the developers behind the SystemBC botnet are actively adapting their toolset to bypass detection and expand their target surface beyond Windows environments.
The Silent Push investigation found that much of the Command and Control (C2) infrastructure relies on abuse-tolerant hosting providers, with the highest concentration of infected IP addresses observed in the US, followed by Germany, France, Singapore, and India.
Furthermore, the discovery of compromised government infrastructure in Vietnam and Burkina Faso underscores the malware's reach into sensitive sectors.
Implications for Cybersecurity Defenses
The persistence of SystemBC highlights a critical challenge for defenders. The malware often facilitates the initial stages of intrusion chains that lead to devastating ransomware attacks. Organizations are urged to monitor for SystemBC indicators, as early detection of this proxy traffic can prevent downstream compromise.
In August 2024, SystemBC was distributed in a new data theft campaign using fake IT calls. In November 2025, the DanaBot Banking Trojan also resurfaced with Version 669, and SmokeLoader returned in December 2024 after the Operation Endgame takedown.
Operation Endgame, conducted between May 27 and 29, 2024, aimed to disrupt criminal services and take down infrastructure used by malware droppers, including Bumblebee, IcedID, Pikabot, Smokeloader, and SystemBC.