INC Ransom Backup Server Security Fail Enabled 12 US Companies to Recover Their Data
- Operational Error: A security failure exposed the INC ransomware group infrastructure, containing data exfiltrated from multiple victims.
- Data Recovery: Cybersecurity researchers accessed and recovered stolen data from 12 U.S. organizations, including those in the healthcare and manufacturing sectors.
- Investigation Insight: The investigation revealed hardcoded credentials and repository paths for the backup tool Restic, which the threat actors used in their operations.
A significant INC ransomware operational security failure has led to the successful recovery of stolen data for a dozen U.S. organizations in healthcare, manufacturing, professional services, and technology. The breakthrough came after the digital forensics and incident response firm Cyber Centaurs investigated an attack on one of its clients.
During the forensic examination, researchers discovered artifacts related to the legitimate backup tool Restic. Although the tool was not used in that specific attack, its presence and associated configuration scripts provided a crucial lead.
Exploiting Attacker Infrastructure for Data Recovery
Cyber Centaurs researchers theorized that the INC ransomware gang was likely reusing its Restic-based infrastructure across multiple campaigns. Analysis revealed:
- Credentials staged in memory, not config files,
- S3-compatible storage, not AWS proper,
- Repository-level isolation, not bucket-level,
- File-list driven backups, suggesting selective targeting.
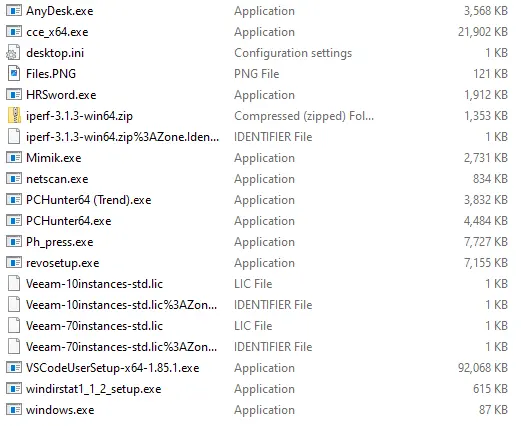
This critical mistake allowed the research team to enumerate the attacker-controlled backup server, discovering in the process that the threat actor leveraged:
- AnyDesk for redundant remote access,
- Mimikatz (mimik.exe) for credential harvesting,
- iperf3 for network throughput testing,
- PC Hunter for low-level process and kernel inspection,
- Revo Uninstaller for post-activity cleanup.
This investigation confirmed the presence of encrypted data belonging to 12 unrelated U.S. organizations affected by separate INC ransomware incidents. The team then recovered the data and coordinated with law enforcement to return it to its rightful owners.
Cybersecurity Best Practices and Detection
This incident highlights how even sophisticated ransomware groups can make critical errors, as it also happened last month, when researchers exposed the LockBit 5.0 infrastructure, including a Key IP Address and domain.
For defenders, this reinforces the importance of thorough incident response. Based on their findings, the researchers developed YARA and Sigma rules to help other organizations detect suspicious Restic use in their environments.
INC Ransom claimed to have attacked the major automotive supplier Yazaki Group last month, and the U.S. CodeRED emergency alert system in November.