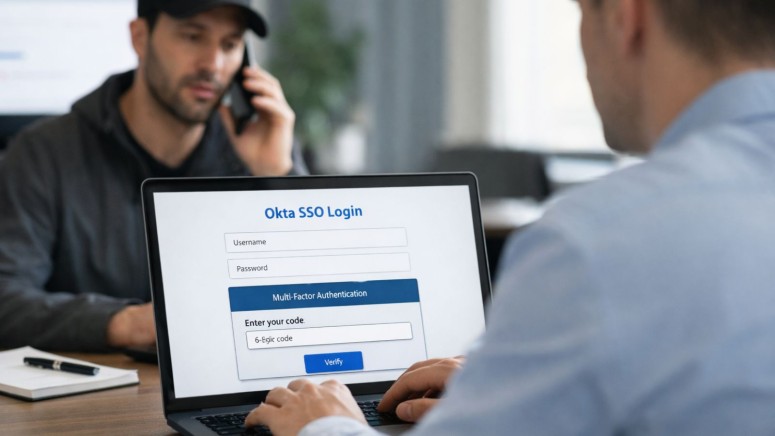
Okta SSO Accounts Targeted in Vishing Campaign that Uses Custom Phishing-as-a-Service Kits, ShinyHunters Allegedly Behind It
- Vishing Tactic: Sophisticated voice-based social engineering attacks combined with real-time phishing kits to target employees and steal Okta SSO credentials.
- MFA Bypass: Custom phishing platforms manipulate the victim's authentication process during a call, bypassing even push-based MFA, including number-matching.
- Data Theft Objective: Attackers gain access to a company's wide range of integrated cloud services to exfiltrate sensitive data and issue extortion demands.
UPDATE: ShinyHunters claimed today that they are behind the recent Okta vishing campaign in a message to Hudson Rock’s Alon Gal, alleging they have published stolen records containing Personally Identifiable Information (PII) from Crunchbase (2 million), SoundCloud (30 million), and Betterment (20 million), with more to follow.
Okta warned of active social engineering campaigns targeting users of its single sign-on (SSO) services. These Okta SSO phishing attacks use custom-built kits designed for voice phishing (vishing) that impersonate a company's IT staff and call employees to set up new security features, such as passkeys.
During the call, the victim is directed to a malicious site where their actions can be manipulated in real time via an attacker's command-and-control (C2) panel.
Advanced Vishing Kits Compromise Okta SSO
The success of this vishing-based data theft relies on the synchronization between the voice call and the fraudulent web page. As the employee enters their credentials, the attacker relays them to the legitimate Okta service, triggering a multi-factor authentication (MFA) challenge, an Okta advisory said.
The attacker's C2 panel then instantly updates the phishing site to display a matching prompt, tricking the user into providing the MFA code or approving a push notification. The attackers then use the intercepted credentials to access the victim's Okta dashboard and steal valuable data.
“Using these kits, an attacker on the phone to a targeted user can control the authentication flow as that user interacts with credential phishing pages,” said Moussa Diallo, threat researcher at Okta Threat Intelligence.
“They can control what pages the target sees in their browser in perfect synchronization with the instructions they are providing on the call,” bypassing any form of MFA that is not phishing-resistant.
Recommendations and Cybersecurity Best Practices
Okta integrates with services such as Microsoft 365, Salesforce, Slack, Zoom, Citrix, Atlassian Jira and Confluence, Google Workspace, and more. Reports suggest that some extortion demands are allegedly signed by ShinyHunters.
To counter these sophisticated threats, Okta strongly recommends adopting phishing-resistant MFA methods such as Okta FastPass or FIDO passkeys, which are not susceptible to social-engineering-based interception.
Organizations must educate employees to be skeptical of unsolicited IT calls and verify any requests through official channels. “The key is to know where your legitimate requests come from, and allowlist those networks,” Diallo said.
In June 2025, GTIG discovered that the UNC6040 threat actor (ShinyHunters) targeted Salesforce via sophisticated vishing campaigns. Following the Salesforce compromise, UNC6040 has demonstrated the ability to move laterally, using harvested credentials and multifactor authentication codes to target additional cloud environments such as Okta and Microsoft 365.
In September, the FBI highlighted active Salesforce exploitation campaigns by two cybercriminal groups that Google confirmed: UNC6040 focused on vishing to impersonate IT desks, while UNC6395 exploited compromised Salesloft Drift OAuth tokens.