2026 Fortinet Cloud Security Report: The Cloud Complexity Gap Widens
- Growing Gap: Almost 70% of organizations cite tool sprawl and visibility gaps impeding cloud security, widening the disconnect between cloud velocity and security capabilities.
- Confidence Decline: Despite rising budgets, 66% of organizations lack confidence in their cloud threat real-time detection and response, up from 64% the previous year.
- Talent Shortage: Almost 75% report an active shortage of qualified cybersecurity professionals, forcing overextended teams to rely on reactive, alert-driven workflows.
The 2026 Fortinet Cloud Security Report reveals a critical structural mismatch in modern enterprise security: the cloud complexity gap. While 88% of organizations now operate across hybrid or multi-cloud environments, security teams are struggling to maintain real-time visibility. The report indicates that the speed of cloud adoption has significantly outpaced the maturity of security operations.
Consequently, fragmentation has become a primary risk driver, with organizations forced to manually correlate alerts across disconnected systems that were never designed to integrate, significantly slowing detection and response times.
Multi-Cloud Security Challenges and Risks
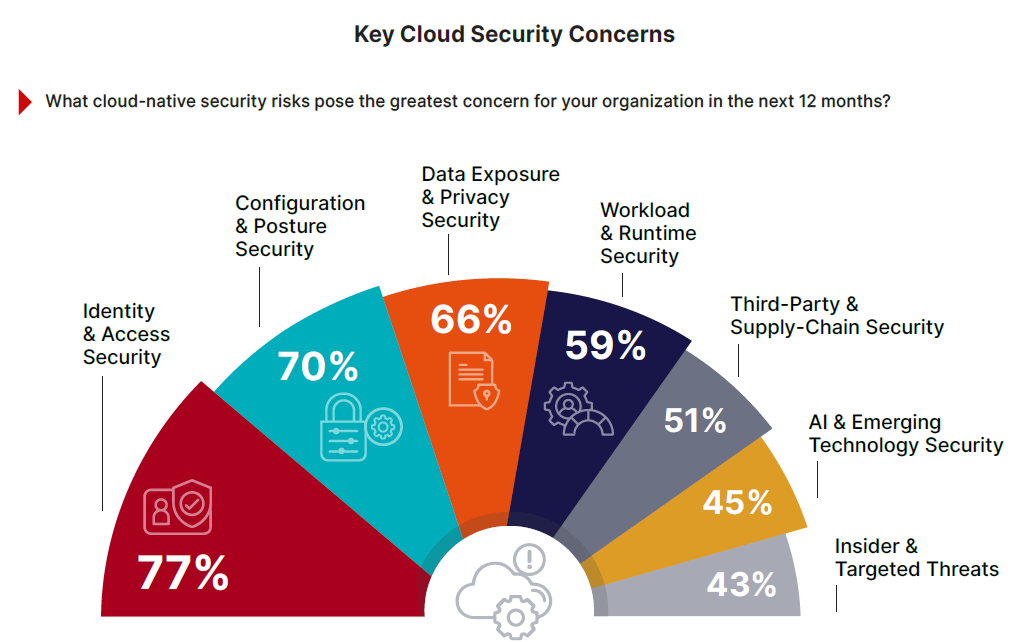
As the attack surface expands across multiple providers, multi-cloud security challenges have intensified. The report identifies the top cloud-native concerns as:
- Identity and access security (77%),
- Misconfigured cloud services (70%),
- Data exposure (66%).
These risks are exacerbated by the fact that 59% of organizations still rate their cloud security posture at initial or developing stages. Adversaries are now leveraging automation and AI to exploit these gaps faster than human-led defenses can react.
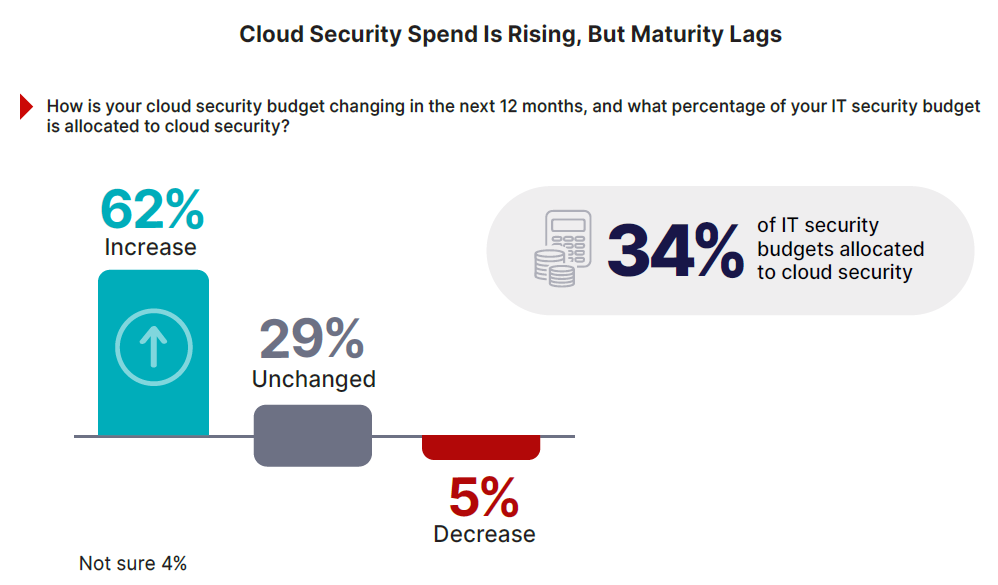
The survey underscores that high investment levels, with cloud security averaging 34% of IT security budgets, are not translating into maturity due to the operational friction caused by tool sprawl.
Recommendations and Cybersecurity Trends 2026
In response to these structural failures, cybersecurity trends 2026 point toward a massive shift in strategy. The data shows that 64% of organizations would choose a single-vendor platform that unifies network, cloud, and application security if starting from scratch.
“Organizations that simplify their cloud and AI security stack and enable effective automation will be far better positioned to safely scale AI as threats continue to evolve,” said Diana Kelley, CISO at Noma Security. Ram Varadarajan, CEO of Acalvio, recommends an AI-first shift from reactive blocking to AI-driven preemptive defense.
Shane Barney, CISO at Keeper Security, recommends organizations that accelerate their use of AI and multi-cloud environments to treat cloud security as an operating model, not a collection of products. “Prioritizing identity-first security through a modern Privileged Access Management (PAM) platform, simplifying architectures, and enabling context-driven automation are essential steps.”
ColorTokens’ Agnidipta Sarkar suggested moving from being secure to breach-ready, and recommends that operational cyber resilience practices “leverage AI-based capabilities to anticipate and prepare for attackers, using available information from CISA, MITRE, and others to narrow attack surfaces.”