Afghan Government Workers Targeted with Phishing Lures in Nomad Leopard Campaign Delivering FalseCub Malware
- Targeted Campaign: A cyber campaign, dubbed Operation Nomad Leopard, is actively targeting Afghan government employees with spear-phishing emails.
- Deceptive Lures: Decoy documents disguised as official correspondence trick victims into opening malicious files.
- Malware Deployed: The campaign deploys the FalseCub malware, which collects and exfiltrates sensitive data from infected systems.
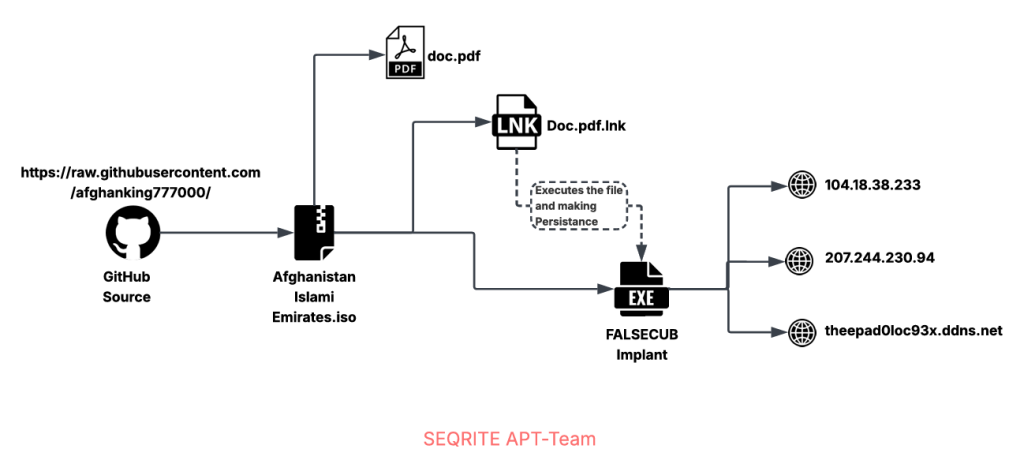
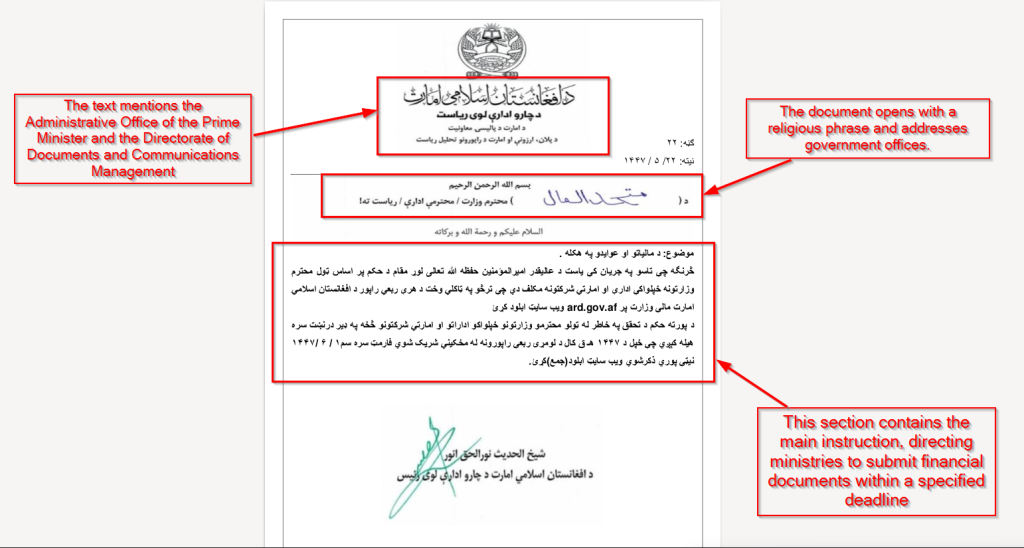
An Afghan government phishing attack targeting employees across various ministries and administrative offices leverages sophisticated social engineering tactics. The campaign, identified by security researchers in December and tracked as Operation Nomad Leopard, distributes emails containing decoy documents that mimic legitimate government letters.
The files, complete with forged signatures of senior officials, attempt to establish credibility and entice recipients to engage with the malicious payload, indicating that threat actors have conducted extensive reconnaissance of Afghan government structures and communication protocols.
Technical Analysis of FalseCub Malware
Upon interaction with the malicious document, the attack chain delivers the FalseCub malware, a recent Seqrite Labs report said. This payload is designed to harvest and exfiltrate data from compromised endpoints.
In this campaign, the attackers utilized GitHub temporarily for command-and-control (C2) and payload hosting.
The threat actor, using the alias "Afghan Khan," has also been observed uploading various legal- and administrative-themed documents to public libraries, likely for use in future campaigns.
Cybersecurity in Afghanistan and Regional Threats
While the campaign is not attributed to a specific group, its focus and the reuse of online personas suggest it is the work of a small, regionally focused cluster with low-to-moderate sophistication. Evidence, including a shortened link used in the campaign, points to potential origins in Pakistan.
Government entities are advised to enhance employee awareness training to recognize phishing attempts, implement stringent email filtering, and restrict the execution of unauthorized files to mitigate the risk posed by the Nomad Leopard campaign and similar threats.
A Veeam report this month said the remote access compromise, phishing, social engineering, and rapid flaw exploitation remain the top threats.