Ransomware Attacks Surged 58% in 2025, New Report Finds
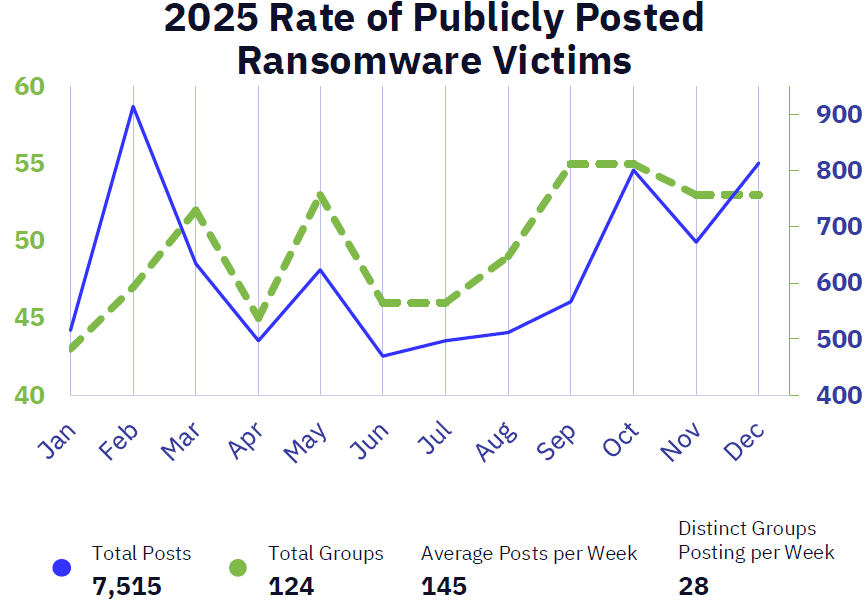
- Unprecedented Growth: Observed ransomware victims increased by 58% year-over-year in 2025, with a record-breaking 124 distinct threat groups tracked.
- Dominant Threat Groups: Qilin and Akira emerged as the most prolific ransomware groups, filling the void left by the disruption of former leaders like LockBit and Alphv.
- Most Impacted Sectors: The Manufacturing industry was the most targeted sector, accounting for 14% of all observed victims, followed by technology, retail, and healthcare.
A new report on 2026 ransomware trends reveals a dramatic escalation in cyber extortion activity, with the number of publicly posted victims surging by 58% year-over-year in 2025. The GRIT 2026 Ransomware & Cyber Threat Report documents a record 7,515 victims claimed by 124 distinct threat groups, indicating a significant expansion and adaptation of this ecosystem.
Despite law enforcement disruptions in 2024, former mid-tier groups such as Qilin and Akira have risen to prominence, absorbing affiliates and increasing their operational tempo to become the year's most impactful attackers. Q4 2025 shattered all previous records for the highest number of victims observed in a single quarter.
Analysis of Ransomware Industry Impact
The cyber threat report highlights that the manufacturing sector remains the primary target for ransomware gangs, with 1,060 publicly claimed victims. The technology, retail and wholesale, and healthcare industries also remained top targets, demonstrating their high value to attackers due to their operational sensitivity and the sensitive data they hold.
The report said that the most impactful ransomware groups last year were:
- Qilin – While Qilin is the most prolific in terms of victims, they are far from the most “profitable.”
- Akira – It was responsible for the second-highest number of observed victims in 2025 through its mass exploitation of SonicWall SSL VPNs.
- Cl0p – Clop had two campaigns that two campaigns accounted for 461 victims: one based on the Cleo 2024 attacks and a November one exploiting Oracle’s eBusiness Suite (EBS).
GuidePoint assesses that Qilin’s growth in 2025 “was likely fueled in part by affiliates who migrated to Qilin” after the alleged April shutdown of former major RaaS player, RansomHub.
The report also notes a significant 132% year-over-year (YoY) increase in attacks targeting the legal industry, underscoring the growing risk to sectors that manage highly sensitive client information. Geographically, the United States remains the most affected nation, accounting for over 55% of all observed victims.
Democratization of advanced techniques and the operationalization of artificial intelligence (AI) dominated the ransomware landscape, which was also marked by the widespread adoption of Bring Your Own Vulnerable Driver (BYOVD) attacks and the measured integration of AI into attack chains.
Key Vulnerabilities and Cybersecurity Insights
The most damaging campaigns in 2025 stemmed from the exploitation of zero-day and critical vulnerabilities in internet-facing enterprise software and perimeter devices. Established groups like Qilin and Akira demonstrated sophisticated capabilities by exploiting these flaws to gain initial access.
The report also shows a dramatic 82.5% YoY increase in new vulnerabilities added to the Known Exploited Vulnerabilities (KEV) catalog in the first quarter of 2025.
“While law enforcement disruptions have reshaped the RaaS ecosystem, group fragmentation is driving new patterns of high-volume, repeatable operations, pushing overall activity to record-breaking levels,” said Jason Baker, Lead Threat Analyst at GuidePoint Security.
Baker recommends that organizations focus on well-resourced defenders, proactive vulnerability management, and real-time threat intelligence for mitigating risk in the year ahead.
Where Ransomware Defenses Fail and Why Qilin Scaled in 2025
We asked Grayson North, Principal Threat Intelligence Consultant at GuidePoint Security to pinpoint the critical risk vectors. North emphasized that "identity and access control is crucial for disrupting almost every part of the ransomware kill chain," noting that in 2025 the most common initial access threat actors used was authenticating to a corporate VPN with stolen employee credentials.
That often enabled access to the systems and data assigned to the compromised account. To curb this, North urged, "Introducing properly configured controls such as multifactor authentication (MFA) and data loss prevention (DLP) that can slow down these types of attacks significantly."
Beyond initial access, North explained that threat actors will typically steal as much data as they can and then launch an encryption attack, rendering an organization’s most important data inaccessible unless a ransom is paid. To mitigate the impact of such scenarios, North outlined two additional priorities:
- Having regular, functional, and immutable backups in the event that a ransomware actor successfully infiltrates the network.
- Ransomware actors regularly seek and delete or disable legacy backup systems. As a result, using an offsite solution that does not allow even the most privileged administrators to delete the backed-up data can significantly reduce the impact of an otherwise successful encryption attack.
Last month, security researchers discovered that Shanya Packer-as-a-Service (VX Crypt) powers modern Akira, Qilin, and Medusa ransomware attacks. Among Qilin’s latest victim claims is the City of Santa Paula, which disrupted government services.
This story has been updated to include additional threat intelligence analysis on ransomware access vectors and Qilin’s 2025 activity.