RedVDS Cybercrime-as-a-Service Disrupted by Germany, Europol, and Microsoft in Coordinated Takedown, Phishing Infrastructure Disabled
- International Takedown: Europol and German authorities dismantled the RedVDS cybercrime-as-a-service platform with Microsoft’s help.
- Massive Phishing Operations: In a single month, over 2,600 RedVDS virtual machines sent approximately 1 million phishing messages per day to Microsoft customers.
- Financial Impact: The RedVDS cybercrime-as-a-service enabled over $40 million in fraud losses in the U.S.
Microsoft's Digital Crimes Unit supported a coordinated international law enforcement operation, including Europol, to disrupt the RedVDS cybercrime platform, a key enabler of the cybercrime-as-a-service ecosystem. The operation involved civil actions in the U.S. and the U.K., leading to the seizure of two primary domains and a server in Germany.
RedVDS provided criminals with disposable virtual machines (VMs) running unlicensed software, including Windows, allowing them to conduct large-scale fraud operations anonymously and with minimal investment – for a subscription fee as low as $24 per month.
Operational Impact of the Cybercrime-as-a-Service Model
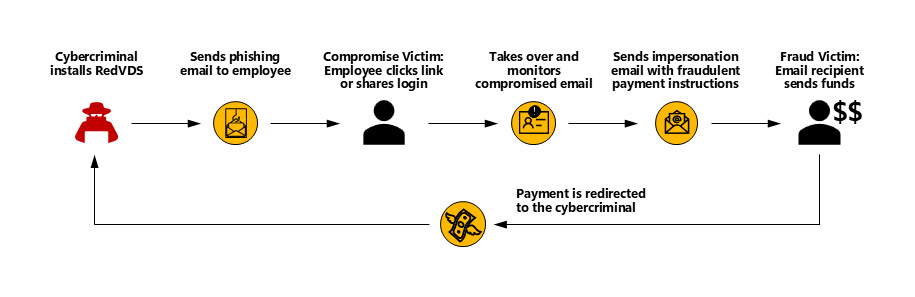
The RedVDS platform was a significant source of malicious activity, primarily facilitating payment diversion fraud and business email compromise (BEC) schemes. Microsoft's investigation revealed that the malicious infrastructure was used to send an average of one million phishing messages per day from its network of VMs.
The platform rented servers from hosting providers in North America and Europe, allowing attackers to bypass geolocation security filters by launching attacks from IP addresses close to their targets.
Since September, these attacks have resulted in fraudulent access to the Microsoft email accounts of over 191,000 organizations, Microsoft said in a recent report, adding that in one month, over “2,600 distinct RedVDS virtual machines sent an average of one million phishing messages per day to Microsoft customers alone.”
The real estate sector was a primary target, with threat actors impersonating realtors and escrow agents to divert home payments, resulting in devastating financial losses for victims.
It also affected other sectors, including construction, manufacturing, healthcare, logistics, education, and legal services. Among the victims are H2-Pharma and the Gatehouse Dock Condominium Association, both targeted through sophisticated BEC schemes that exploited trust and timing.
Strategic Disruption of Criminal Networks
This Microsoft RedVDS takedown marks the company's 35th civil action against malicious infrastructure..
“Microsoft is also working closely with international law enforcement, including Europol’s European Cybercrime Centre (EC3), to disrupt the broader network of servers and payment networks that supported RedVDS customers as part of the ongoing disruption,” the report said.
The disruption of RedVDS and its supporting payment networks represents a significant blow to the accessible, low-cost tools that fuel the modern cybercrime economy.
A feature in Microsoft 365 Exchange Online, known as Direct Send, was being actively exploited by malicious actors for phishing and BEC in October. The following month, the Sneaky2FA phishing kit adopted Browser-in-the-Browser tactics to steal credentials via fake Microsoft login pages.