Tennessee Man to Plead Guilty to 2023 US Supreme Court Hacking
- Guilty Plea Expected: Nicholas Moore, 24, is scheduled to plead guilty to accessing the Supreme Court's electronic filing system without authorization.
- Repeated Unauthorized Access: Court documents indicate Moore breached the system on 25 separate days in late 2023.
- Lack of Details: Court documents do not mention how it happened or what information was impacted.
A Tennessee resident is set to admit guilt on Friday regarding a significant breach of federal judicial infrastructure. Nicholas Moore, 24, of Springfield, Tennessee, faces charges related to the unauthorized access of the U.S. Supreme Court’s electronic document filing system on dozens of occasions over a three-month period in late 2023.
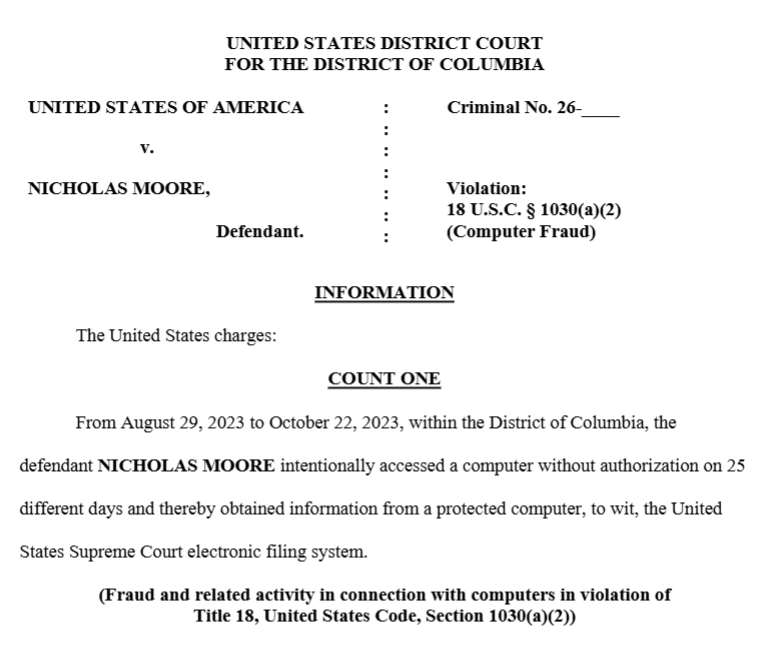
Nicholas Moore Case Overview
Prosecutors allege that Moore intentionally accessed protected computers from August 29, 2023 to October 22, 2023, on 25 different days. According to filings from the U.S. District Court for the District of Columbia, the Nicholas Moore guilty plea is scheduled for Friday via video feed.
While specific details regarding the exact nature of the data accessed remain under seal, the charges confirm that information was obtained from the protected system. Prosecutors have not publicly disclosed the methods Moore used to bypass the court's authentication measures or the specific motive behind the intrusion.
The case was initially flagged by researchers monitoring court documents.
Cybersecurity in Government Infrastructure
The US Supreme Court hacking incident is not isolated; it occurs amid an increasing threat to federal court systems.
In August 2025, the Administrative Office of the U.S. Courts announced a separate cyberattack on its case management system, Public Access to Court Electronic Records (PACER), which exposed sensitive data and was attributed to state-sponsored actors, allegedly from Russia.
In December 2024, TechNadu reported on a U.S. Treasury breach via BeyondTrust’s remote support by Chinese state-sponsored actors, and Iranian hackers MuddyWater targeted U.S. and other governments with DCHSpy in July 2025.