HoneyMyte APT Campaign Uses Kernel-Mode Rootkit to Deploy ToneShell
- Evolved Tactics: The HoneyMyte APT group now uses a kernel-mode rootkit driver signed with a stolen digital certificate to deploy the ToneShell backdoor.
- Targeted Espionage: Government organizations in Southeast and East Asia are targeted, probably using previous infections to deploy persistence mechanisms.
- Stealth Capabilities: The rootkit utilizes advanced evasion techniques: protecting malicious files, registry keys, and processes from security software and user deletion.
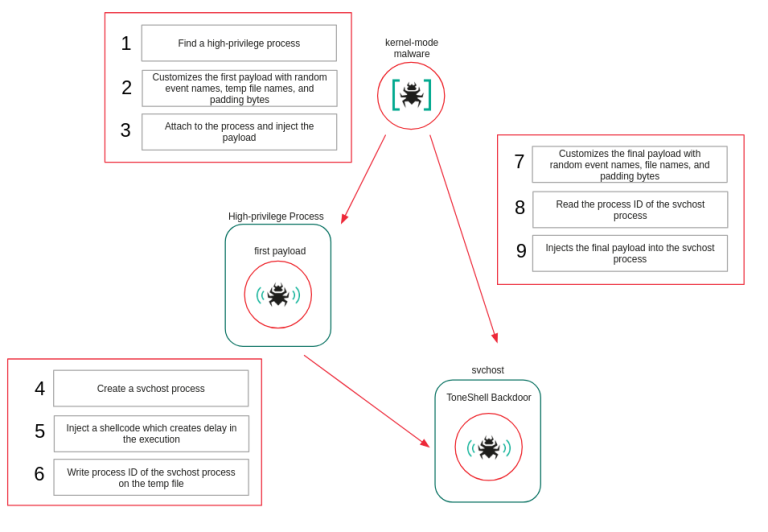
The HoneyMyte advanced persistent threat (APT) group demonstrated significant evolution in its tradecraft. Security researchers have identified a malicious kernel-mode driver being used to deploy the ToneShell backdoor in a new cyberespionage campaign attributed to the group. This driver functions as a rootkit to conceal the attacker's presence.
By operating at the kernel level, the HoneyMyte rootkit can deeply manipulate system behavior, employing file system mini-filters to protect its components from deletion and registering callbacks to block access to its registry keys and processes.
Technical Analysis of the ToneShell Backdoor
The campaign's primary payload is a new variant of the ToneShell backdoor, now injected directly via the kernel-mode driver’s embedded payload, SecureLabs by Kaspersky said in a report released today.
The infection process involves complex multi-stage shellcode execution. The driver, signed with a compromised digital certificate from an old technology vendor, disables security monitoring by tampering with Microsoft Defender's WdFilter altitude settings.
“The first payload spawns an svchost process and injects a small delay-inducing shellcode,” the report said. The backdoor is then injected into the system process that the first payload created.
This version of ToneShell uses fake TLS headers to disguise its command-and-control (C2) communications traffic. The malware supports remote capabilities that allow comprehensive intelligence gathering, including:
- File upload/download,
- Remote shell execution,
- Session management.
“Notably, nearly all affected victims had previously been infected with other HoneyMyte tools, including the ToneDisk USB worm, PlugX, and older variants of ToneShell,” the SecureList report said.
Implications for Cyber Defense
The shift toward kernel-mode deployment represents a dangerous escalation in sophistication for HoneyMyte APT.
Traditional security tools may be blinded to the malware's activities, as it deploys a small user-mode component for the final injection step, along with several obfuscation techniques, callback routines, and notification mechanisms.
This month, another APT targeted Asia, as an Evasive Panda APT cyberespionage campaign poisoned DNS requests to deliver MgBot.