Amazon EC2 and ECS Targeted in Cryptomining Campaign Using Compromised IAM Credentials
Key Takeaways
- Targeted services: An ongoing cryptomining campaign is targeting Amazon Elastic Compute Cloud (EC2) and Amazon Elastic Container Service (ECS).
- IAM credentials: The campaign leverages compromised AWS Identity and Access Management (IAM) credentials.
- Novel persistence technique: The threat actor disables API termination on deployed EC2 instances to disrupt incident response and prolong mining operations.
Amazon Web Services (AWS) has identified an ongoing cryptomining campaign that began in early November 2025. The operation leverages compromised IAM credentials to deploy cryptocurrency mining resources across customer environments using both Amazon EC2 and Amazon ECS.
The activity was first detected by AWS security engineers who observed similar attack patterns across multiple customer accounts, indicating a coordinated effort.
Attack Methods and Persistence Tactics
According to AWS, the campaign does not exploit a vulnerability in its services but rather relies on valid but compromised user credentials.
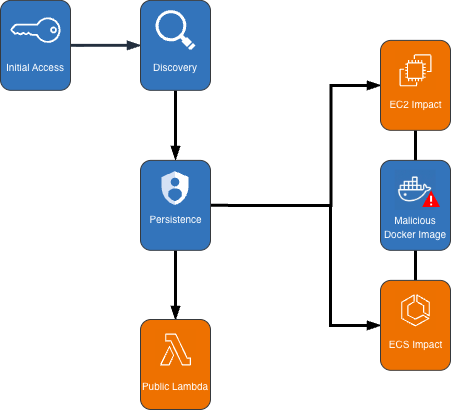
The threat actor behind this cryptomining campaign on AWS follows a systematic approach. After gaining initial access with compromised IAM credentials, they perform reconnaissance by checking EC2 service quotas and testing IAM permissions using the DryRun flag.
The actor deploys miners by creating dozens of ECS clusters – sometimes exceeding 50 in a single attack – and launching EC2 instances via auto-scaling groups configured with aggressive scaling parameters.
A key persistence technique involves modifying instance attributes to disable API termination, a method designed to complicate and delay security teams' remediation efforts by forcing users to re-enable API termination before deleting the impacted resources. This tactic represents an advancement in the persistence methodologies used in cloud security threats.
AWS Response and Threat Detection
AWS GuardDuty threat detection capabilities, including the recently launched Extended Threat Detection, were used in identifying and correlating the various stages of the attack.
To mitigate risks associated with Amazon EC2 and ECS security, AWS recommends customers implement strong identity controls, including:
- multi-factor authentication (MFA),
- least-privilege permissions.
AWS has alerted customers and shared indicators of compromise (IoCs), including the malicious Docker Hub image and specific cryptomining domains.
This month, an international operation dismantled €700 million crypto fraud and laundering network.