
LockBit 5.0 Infrastructure Details Exposed by Researchers in Major Security Failure, Including a Key IP Address and Domain
Key Takeaways
- Critical leak: The core infrastructure of the LockBit 5.0 ransomware operation, including a key IP address and domain, has been publicly exposed.
- Identified server: The server, hosted on a network known for illicit activity, was found by security researchers to have multiple open ports, including RDP.
- Operational failure: This exposure represents a significant operational security lapse for the prolific ransomware group, providing defenders with actionable intelligence.
In a significant operational security failure for one of the world's most notorious ransomware groups, critical details of the LockBit 5.0 infrastructure have been exposed. Cybersecurity researcher Rakesh Krishnan identified and publicized the IP address and the domain hosting the group's latest data leak site.
LockBit 5.0 Server Details Leak
This LockBit server leak offers a rare glimpse into the operational backbone of the cybercriminal organization and provides valuable intelligence for network defenders:
- The IP address 205.185.116.233
- The domain karma0[.]xyz
The server is hosted by FranTech Solutions (AS53667), a network provider frequently associated with malicious activities. The domain was registered on November 2, 2025, using Cloudflare nameservers and privacy protection services.
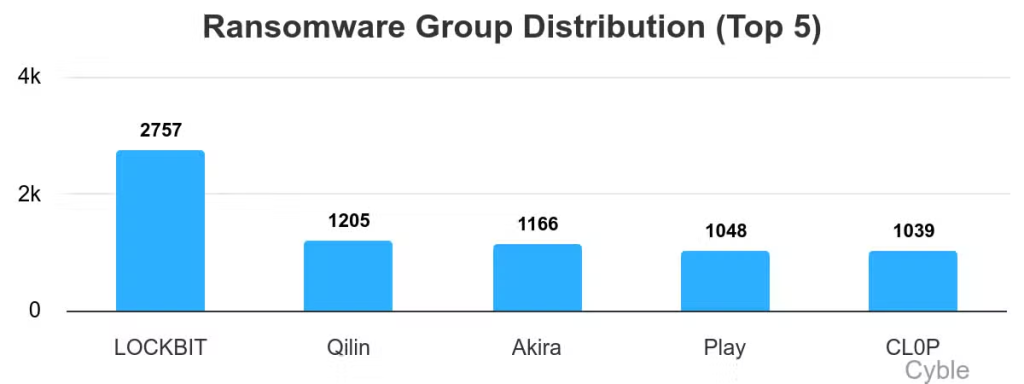
The researcher said in a post on X that, by analyzing the 23 new victims the group announced on December 4 on its new leak site, they discovered that some victims were recycled from the April 2025 LockBit leaks. Meanwhile, Cyble reported that only seven of the victims were new.
Exposed Cybersecurity Vulnerabilities
Security scans of the identified server revealed numerous open ports, highlighting severe cybersecurity vulnerabilities in the group's setup. Port 3389 was found open, exposing the Remote Desktop Protocol (RDP) and providing a direct vector for unauthorized access.
Other open ports included FTP, HTTP, and WinRM, some running on an Apache server with OpenSSL and PHP. The exposure of these services indicates a lack of fundamental security hardening, a surprising lapse for a sophisticated threat actor.
This ransomware group's exposure enables law enforcement and security teams to analyze its technical configuration and potentially disrupt its operations.
Implications of the Infrastructure Exposure
The LockBit 5.0 ransomware variant, which emerged around late September 2025, features enhanced capabilities targeting Windows, Linux, and ESXi systems. Despite previous law enforcement disruptions, the group has demonstrated significant resilience.
However, this public exposure of their core infrastructure allows security professionals to proactively block the identified IP address and domain to mitigate potential attacks.
The incident underscores the persistent challenges threat actors face in maintaining anonymity and secure infrastructure, even as they continue to launch campaigns and incorporate tools like Smokeloader to deliver their payloads.
Last month, Russian hosting provider Media Land was sanctioned for supporting LockBit, BlackSuit, and Play Ransomware.
In October 2024, Maksim Yakubets was unmasked as a high-ranking Russian affiliate of LockBit, who is also believed to be the leader of Evil Corp. Two months later, two individuals were arrested in connection with LockBit: prominent Russian cybercriminal Mikhail Pavlovich Matveev and Rostislav Panev.



![Domain information for karma0[.]xyz](https://cdn.technadu.com/wp-content/uploads/2025/12/image-11.png)





