Chinese APT24 Cyberespionage Campaign Targets Taiwan with BADAUDIO Malware
Key Takeaways
- Sustained campaign: GTIG is tracking a three-year cyber espionage campaign conducted by APT24, a threat actor linked to the People's Republic of China (PRC).
- Malware deployed: The campaign utilizes BADAUDIO, a downloader designed to establish persistent access and deliver secondary payloads like Cobalt Strike Beacon.
- Evolving tactics: APT24 has shifted to more targeted supply chain attacks, including the repeated compromise of a digital marketing firm in Taiwan.
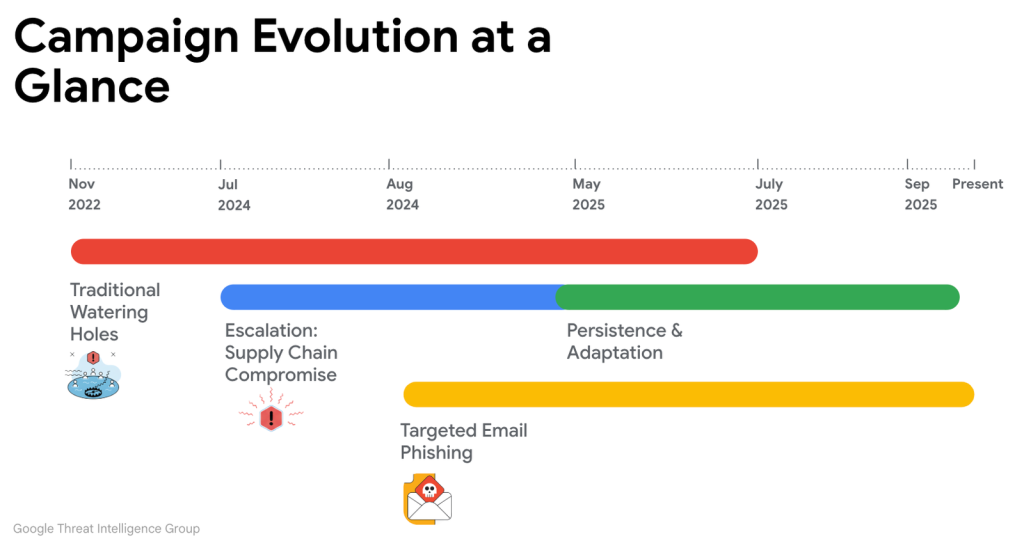
Google's Threat Intelligence Group (GTIG) has detailed a long-running and adaptive APT24 cyberespionage campaign. Active for at least 3 years, the operation by the PRC-nexus threat actor leverages a custom first-stage downloader, BADAUDIO, to infiltrate and maintain access to victim networks.
The campaign demonstrates a clear evolution in tactics, moving from opportunistic, broad-based attacks to highly sophisticated and targeted operations. This shift highlights the increasing capabilities and persistence of state-nexus adversaries.
BADAUDIO Malware Analysis and Delivery Mechanisms
The primary tool in this campaign is BADAUDIO, a malware variant engineered for stealth and persistence.
A technical BADAUDIO malware analysis reveals its use of advanced obfuscation, including control flow flattening, to impede reverse engineering. It is typically delivered as a malicious DLL that leverages DLL Search Order Hijacking for execution.
Upon execution, BADAUDIO:
- collects basic system information,
- encrypts it,
- sends it to a command and control (C2) server within a cookie value to retrieve a secondary payload.
In at least one instance, this payload was identified as Cobalt Strike Beacon, confirmed by a unique watermark previously associated with APT24.
From Web Compromise to Supply Chain Cyberattacks
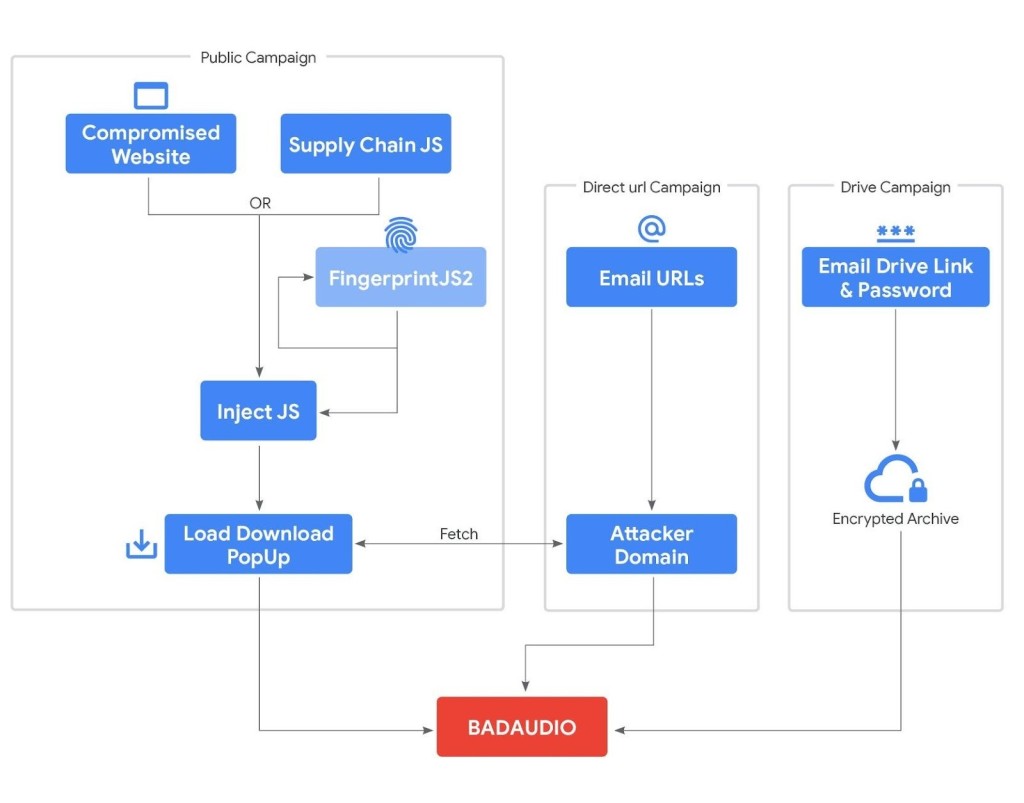
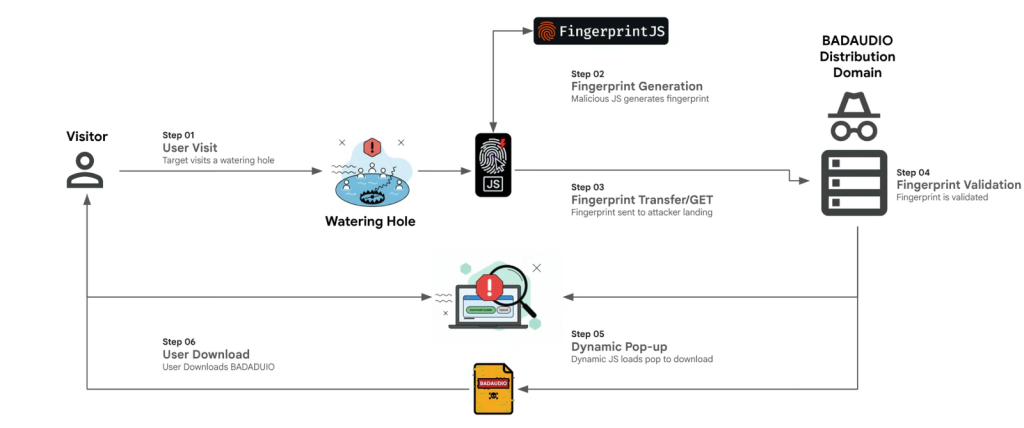
Initially, APT24 relied on strategic web compromises, injecting malicious JavaScript into over 20 legitimate websites to fingerprint visitors and selectively deliver the BADAUDIO payload, sometimes leveraging a typosquatting domain to impersonate a legitimate Content Delivery Network (CDN).
More recently, the group has escalated its methods of malware delivery, executing supply chain cyberattacks and targeted phishing campaigns.
GTIG observed the repeated compromise of a Taiwanese digital marketing firm, which impacted over 1,000 domains using the firm's JavaScript libraries. APT24 also employed targeted phishing campaigns, abusing legitimate cloud services like Google Drive to distribute encrypted archives containing the malware.
Recently, Anthropic published an analysis stating that the Chinese state-sponsored GTG-1002 leverages Claude AI for cyberespionage targeting tens of organizations. In October, a Fortinet investigation revealed evolving phishing campaigns that deliver HoldingHands malware across China, Taiwan, Japan, and Malaysia.