Sneaky2FA Phishing Kit Adopts Browser-in-the-Browser Tactics to Steal Credentials via Fake Microsoft Login Pages
Key Takeaways
- New capabilities: The Sneaky2FA PhaaS toolkit has integrated BITB functionality to simulate legitimate authentication windows.
- Evasion techniques: The kit employs advanced evasion methods, including Cloudflare Turnstile for bot protection and conditional loading to redirect security scanners.
- Dynamic adaptation: The phishing page dynamically adjusts the appearance of the fake pop-up window to match the victim's operating system and browser environment.
The Sneaky2FA phishing page now incorporates Browser-in-the-Browser (BITB) techniques to compromise user credentials, security researchers have identified. This development marks a shift from standard reverse-proxy setups to more deceptive interfaces, indicating the malware's evolution.
Evolution of the Sneaky2FA Phishing Page
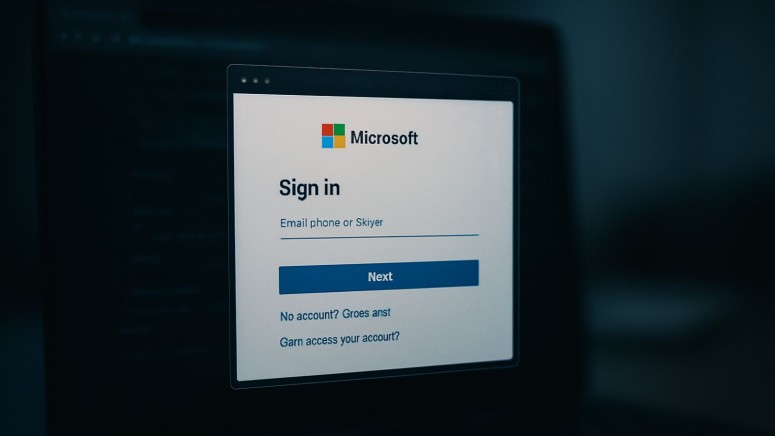
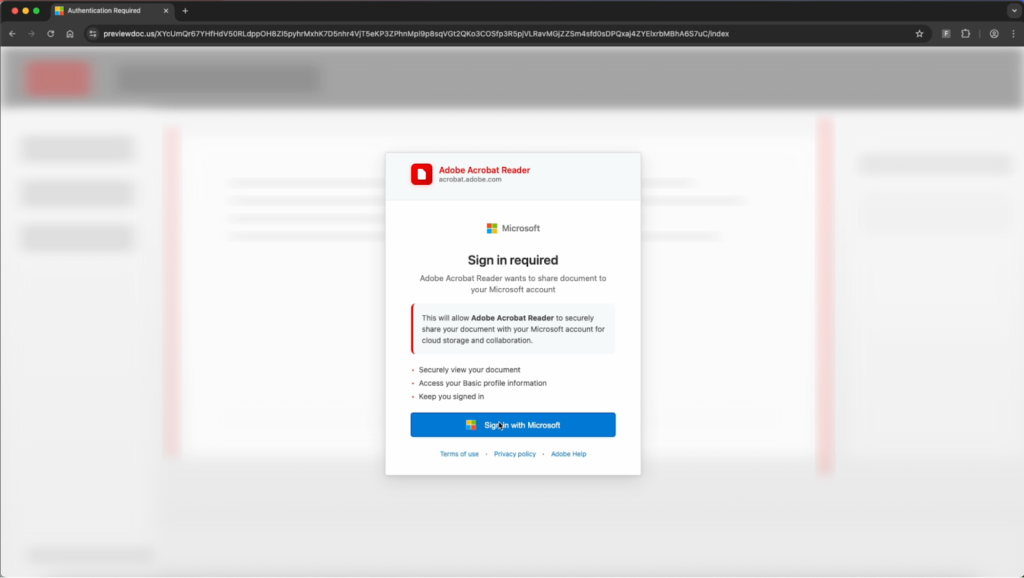
The Sneaky2FA Adversary-in-the-Middle (AiTM) phishing kit, targeting Microsoft 365 session cookies to circumvent MFA, was observed in a Phishing-as-a-Service (PhaaS) campaign that directs victims to a document preview lure that prompts a "Sign in with Microsoft" action.
Instead of a standard redirect, the kit launches a simulated pop-up window that mimics a legitimate Microsoft login prompt adapted to the user's specific OS (e.g., Windows or macOS), as noted in the most recent Push Security report.
This Browser-in-the-Browser phishing method displays a falsified URL bar, effectively masking the malicious domain and deceiving users who rely on URL verification for security.
Sekoia’s Threat Detection & Research (TDR) team obtained the leaked source code and published an analysis earlier this year showing the phishing kit includes some source code from the W3LL Panel OV6, an AiTM phishing kit reported by Group-IB in September 2023.
Sophisticated Phishing Detection Evasion
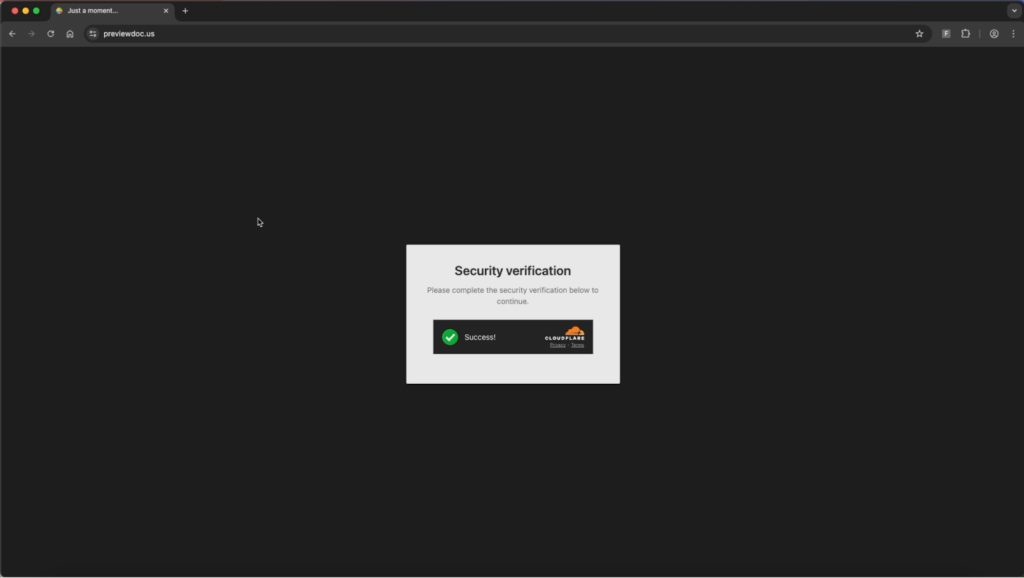
To defeat email scanners, web-crawling security tools, and web proxies analyzing network traffic, the landing page requires visitors to pass a Cloudflare Turnstile bot check before loading malicious content.
Furthermore, the kit utilizes conditional loading; if the visitor's parameters do not match specific targeting criteria (such as geolocations or recognized user agents), the traffic is redirected to benign sites like Wikibooks.
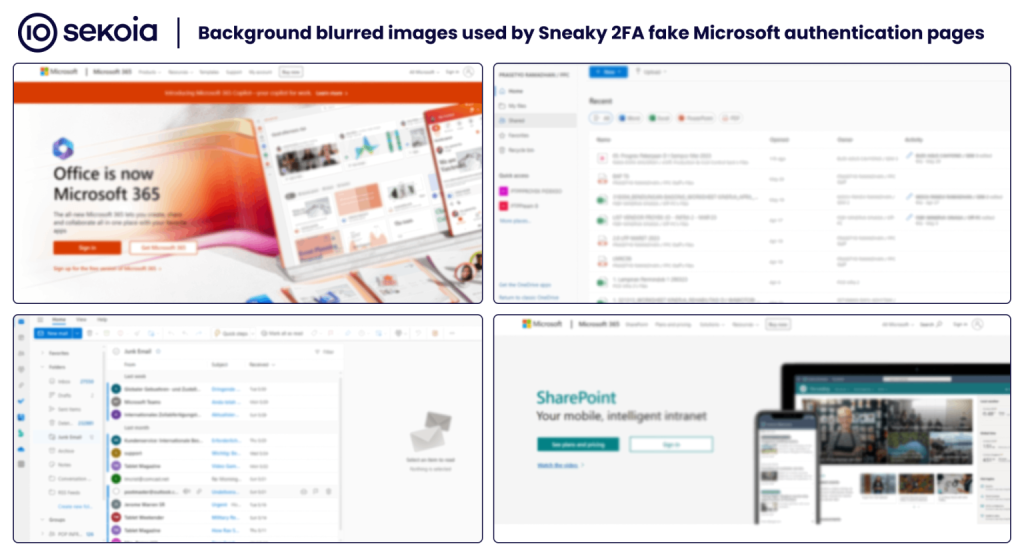
The underlying HTML and JavaScript are heavily obfuscated via changes that are invisible to the user, including:
- Breaking up UI text with invisible tags,
- Embedding background and interface elements as encoded images instead of text.
Sneaky2FA also employs stealthy hosting and domain tactics such as domain rotation and URL masking.
Escalating Cybersecurity Threats
The integration of BITB into widely available PhaaS kits represents an escalation in cybersecurity threats facing enterprise environments. This rapid infrastructure rotation, combined with advanced obfuscation, challenges traditional email gateways and web filters that rely on domain reputation and pattern matching to identify malicious activity.
In September, the VoidProxy PhaaS was used in AiTM attacks targeting Google and Microsoft accounts.