Triofox Unauthenticated Access Flaw, Chained with AV Scanning Feature Abuse to Deploy Remote Access Tools
Key Takeaways
- Vulnerability exploited: A critical vulnerability in the Triofox file-sharing solution is being actively exploited by threat actors for remote access.
- Novel attack vector: Hackers are abusing a built-in antivirus scanning feature to bypass security and execute malicious code.
- Payload delivery: The exploit chain enables the installation of remote access tools, giving attackers persistent control over compromised systems.
An n-day unauthorized access vulnerability in the Gladinet Triofox secure file-sharing and collaboration platform is being actively exploited, chained with the abuse of the software's integrated antivirus (AV) scanning feature to achieve remote code execution (RCE).
Antivirus Feature Abuse
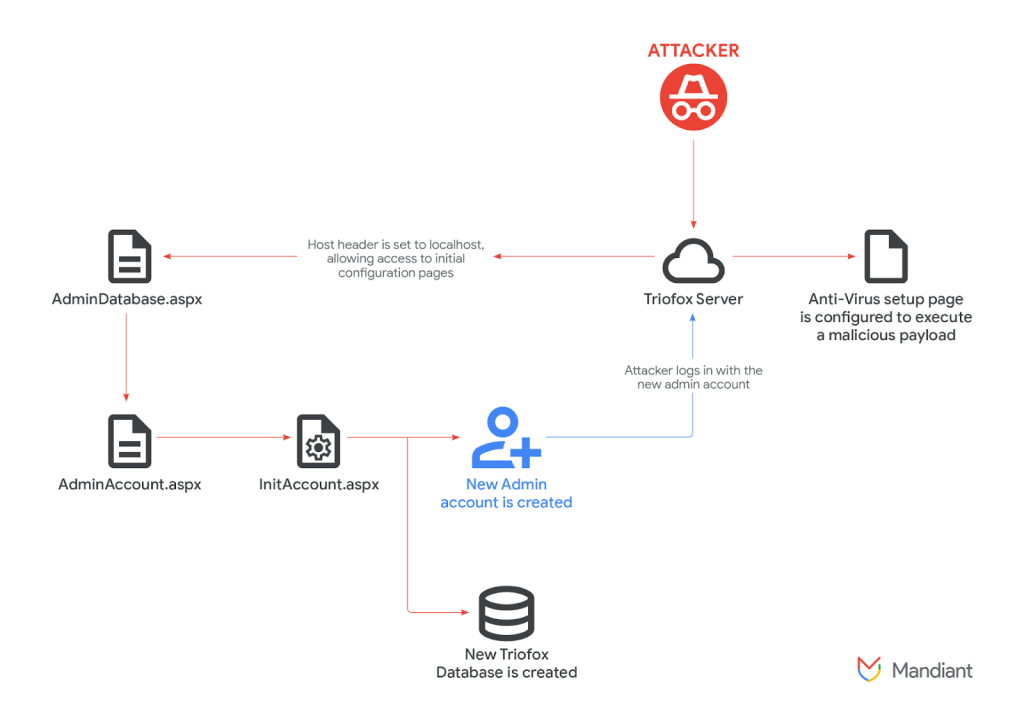
This now-patched Triofox vulnerability, tracked as CVE-2025-12480, allows unauthenticated attackers to upload a malicious file that, when processed by the legitimate AV engine, triggers a payload delivery mechanism.
GTIG observed a threat cluster tracked as UNC6485 exploiting the unauthenticated access flaw together with the abuse of the built-in AV for RCE as early as August 2025.
The core of this attack lies in manipulating the AV scanner integrated into Triofox. Attackers craft a specific file that, upon being scanned, initiates the download and execution of a secondary payload from a remote server, a Google Threat Intelligence Group (GTIG) report said.
This method represents a creative form of AV feature abuse, as it circumvents typical file upload restrictions and security checks.
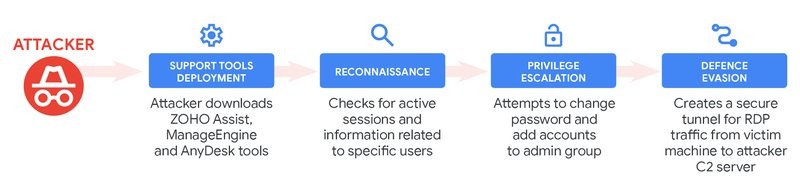
Once the initial payload is executed, the attackers proceed to deploy a legitimate copy of the Zoho Unified Endpoint Management System (UEMS) software installer and well-known remote access tools such as Zoho Assist and AnyDesk.
These tools are leveraged to:
- enumerate active SMB sessions and user information.
- change existing accounts’ passwords.
This grants them persistent access to the compromised server, enabling further malicious activities.
Cybersecurity Risks and Mitigation Actions
This flaw, which affects Triofox version 16.4.10317.56372, highlights critical cybersecurity risks for organizations using the platform. Administrators of Triofox instances are urged to immediately apply the vendor's security patches to remediate the vulnerability, which is resolved in new versions of Triofox.
This incident serves as a crucial reminder that even security-focused features can be weaponized if not properly implemented and hardened against manipulation. Organizations should prioritize timely patching and continuous monitoring to defend against such evolving threats.
Mandiant recommends that organizations:
- Audit admin accounts.
- Verify that Triofox’s Anti-virus Engine is not configured to execute unauthorized scripts or binaries.
- Hunt for attacker tools using the provided hunting queries.
- Monitor for anomalous outbound SSH traffic.
Earlier this month, Windows GDI flaws exposed systems to RCE and data leaks. In September, a MostereRAT phishing campaign leveraged AnyDesk and TightVNC to target Windows systems.