17 Trojanized NPM Packages Deliver Vidar Infostealer Malware in New Campaign
Key Takeaways
- Packages compromised: A threat cluster tracked as MUT-4831 published 17 trojanized npm packages masquerading as legitimate SDKs.
- Payload delivery: The packages execute a post-install script that downloads and runs the Vidar infostealer malware.
- Supply chain threat: This is the first publicly documented instance of the Vidar malware being distributed via the npm package registry.
A malicious campaign involving 17 trojanized npm packages delivers the Vidar infostealer malware to Windows systems. The campaign, attributed to a threat activity cluster named MUT-4831, involved publishing packages that appeared to be benign SDKs or forks of popular projects like React and Cursor.
The discovery was made on October 21, 2025, after a static analysis tool flagged suspicious activity within the packages.
Attack Vector and Payload Analysis
The npm packages, which masqueraded as legitimate software development kits (SDKs), were downloaded over 2,200 times before being removed from the npm registry, a Datadog Security research report said.
The attack chain begins when a developer installs one of the malicious packages. A post-install script automatically executes, downloading a password-protected ZIP archive from a command-and-control (C2) server.
This archive contains the second-stage payload, an executable identified as a variant of the Vidar infostealer. Once executed, Vidar harvests sensitive information, including:
- browser credentials,
- cryptocurrency wallets,
- system files.
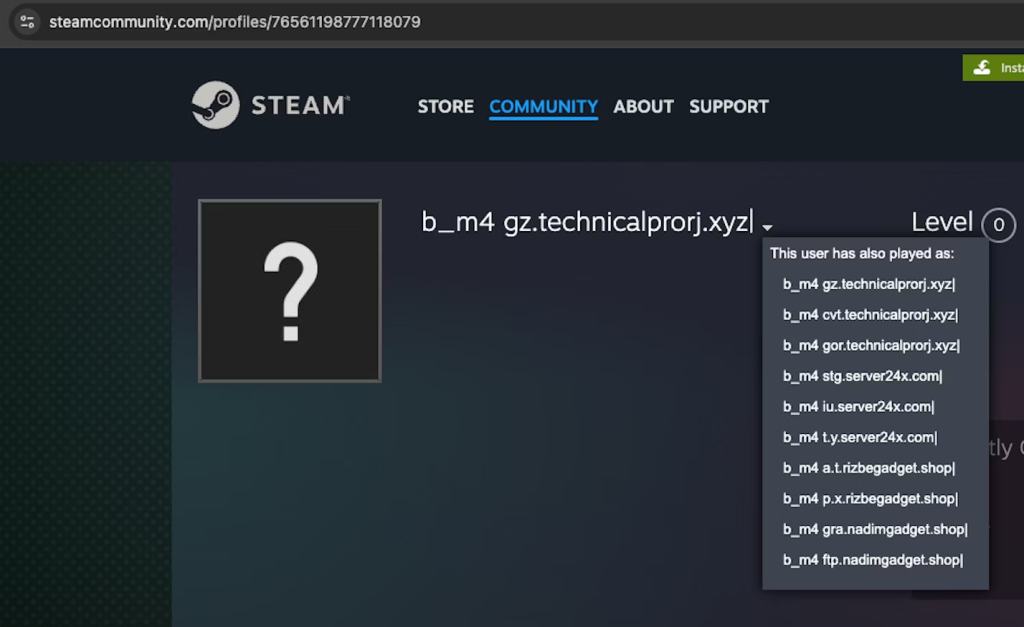
The malware then exfiltrates this data to C2 servers, using platforms like Telegram and Steam to retrieve C2 infrastructure details, before deleting itself to evade detection.
This Vidar malware attack demonstrates a classic two-stage delivery method adapted for the npm ecosystem.
Implications for Software Supply Chain Security
The MUT-4831 campaign represents a critical escalation in software supply chain security threats. While open-source registries have long been a target for threat actors, the use of npm to distribute a well-known infostealer like Vidar is a concerning development.
It shows that attackers are actively abusing trusted developer ecosystems as a reliable initial access vector.
This incident underscores the importance for development teams to scrutinize dependencies, disable automatic script execution during package installation, and employ security tools capable of detecting malicious code signatures within their software supply chain.
In September, multiple CrowdStrike npm packages were targeted in a supply chain attack, and at least 18 popular packages, including debug and chalk, were compromised.
Earlier this year, a trojanized npm package posing as a PDF converter compromised the Atomic and Exodus wallets, and the North Korean Lazarus Group targeted developers with malicious npm packages. Also, attackers leveraged GitHub to distribute Lumma Stealer, Vidar Stealer, SectopRAT, and Cobeacon.