LockBit 5.0 Resurfaces: Faster Encryption and Randomized Extensions, Hackers Say in Interview They See Themselves as Penetration Testers
Key Takeaways
- Operational resurgence: The LockBit ransomware group has reappeared as LockBit 5.0, as an evolution of the previous network despite law enforcement disruptions.
- Enhanced tactics: The new version features a faster encryption engine, randomized file extensions to evade detection, and enhanced anti-debugging and obfuscation layers.
- RaaS model: The group continues its Ransomware-as-a-Service (RaaS) model, restructuring its affiliate program with a modest upfront fee for panel access.
The notorious LockBit ransomware group has re-emerged as LockBit 5.0 following significant law enforcement action earlier this year. This new iteration claims to be a more sophisticated and operationally efficient version of its predecessor.
Their reappearance confirms that even major takedowns may only serve as temporary disruptions to well-organized cybercriminal enterprises.
Analyzing the Evolution and Threat of LockBit 5.0
In a recent interview with HackManac, representatives described the group not as criminals but as "penetration testers," highlighting the industrialized nature of the modern ransomware ecosystem.
“We are not a state‑backed APT,” they said. “Our goal is to monetize vulnerabilities while presenting ourselves as a sort of penetration‑testing service with a 'post‑attack' payout model.”
LockBit 5.0 reportedly introduces several new approaches and technical enhancements designed to bypass conventional cybersecurity defense strategies:
- The encryption engine has been optimized for speed, reducing the response time for defenders.
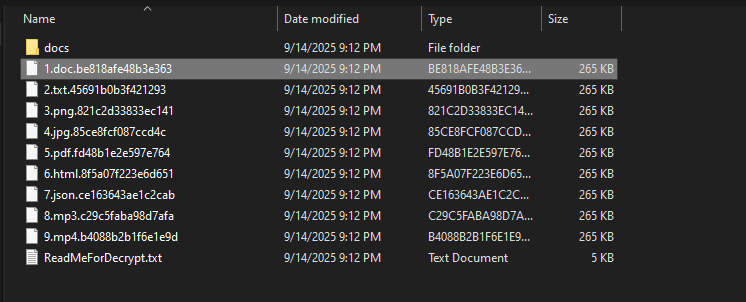
- Each infection now uses a unique, randomly generated 16-character file extension, complicating signature-based detection.
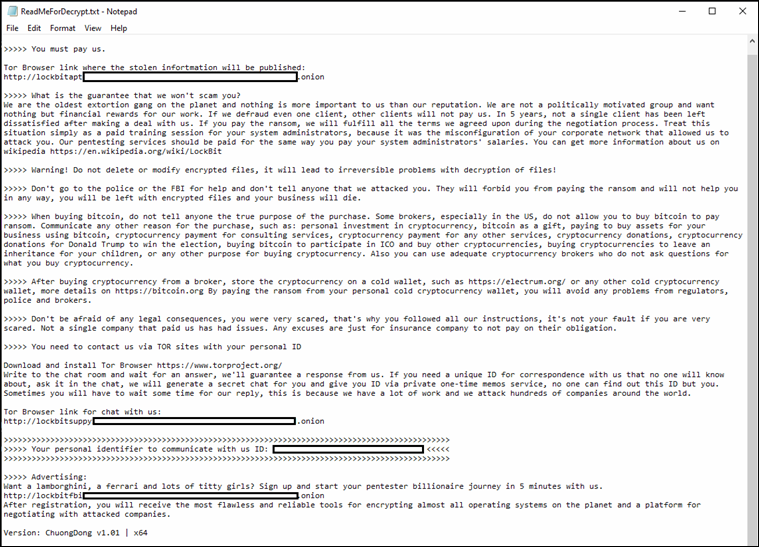
- The extortion process has been standardized, with victims given a 30-day deadline to pay the ransom before their stolen data is published.
The group maintains its Ransomware-as-a-Service (RaaS) model, onboarding new affiliates for a $500 fee that grants them access to the tools and infrastructure needed to launch attacks.
Evaluating the Defensive Posture Against LockBit 5.0
For cybersecurity defenders, the resurgence of LockBit ransomware underscores the persistent and adaptive nature of ransomware threats. The group's leaders view law enforcement actions as temporary setbacks and rely on a decentralized affiliate structure and operational security to ensure resilience.
While LockBit 5.0 claims to exclude non-profit organizations and healthcare institutions from its targets, its profit-driven model means any organization with perceived vulnerabilities can become a target, including banks.
September reports analyzed the new version, with Trend Micro underscoring its seamless cross-platform capabilities across Windows, Linux, and ESXi systems and Vectra revealing that affiliates gained more flexibility with customizable ransom notes.
This reality demands that organizations move beyond reactive measures and implement proactive defense strategies, including:
- robust endpoint protection,
- continuous network monitoring,
- comprehensive employee training to counter the social engineering tactics often used as an initial entry vector.
According to an October Kela cybersecurity report, global ransomware attacks are surging, endangering 50% of critical industries and threatening national security.
In October 2024, the U.K. unmasked Maksim Yakubets, a high-ranking Russian affiliate of the LockBit ransomware group, as an alleged leader of Evil Corp. In December 2024, prominent Russian cybercriminal Mikhail Pavlovich Matveev and Rostislav Panev were arrested in connection with LockBit.