Qilin Ransomware’s Evolving Attack Methods Include Leveraging VPN Credentials Exposed on the Dark Web
- High-volume attacks: Qilin ransomware is highly active, attacking over 40 victims per month in the second half of 2025, primarily targeting the manufacturing sector.
- Double-extortion strategy: It employs a double-extortion model to harvest credentials and disable security software before executing the ransomware.
- Advanced intrusion techniques: The actor leverages leaked VPN credentials, remote management tools, and custom scripts.
A recent analysis by Cisco Talos provides an in-depth look at the tactics, techniques, and procedures (TTPs) of the Qilin ransomware group (formerly Agenda), one of the most prolific and impactful threat actors currently active, focusing on the sophisticated and multi-stage approach Qilin affiliates use to compromise networks and exfiltrate data.
Analysis of Ransomware Attack Tactics
The group, which operates a Ransomware-as-a-Service (RaaS) model, has been responsible for a high volume of attacks globally, with the manufacturing, professional services, and wholesale trade sectors being the most affected.
Most severely affected countries include the U.S., Canada, the U.K., France, and Germany.
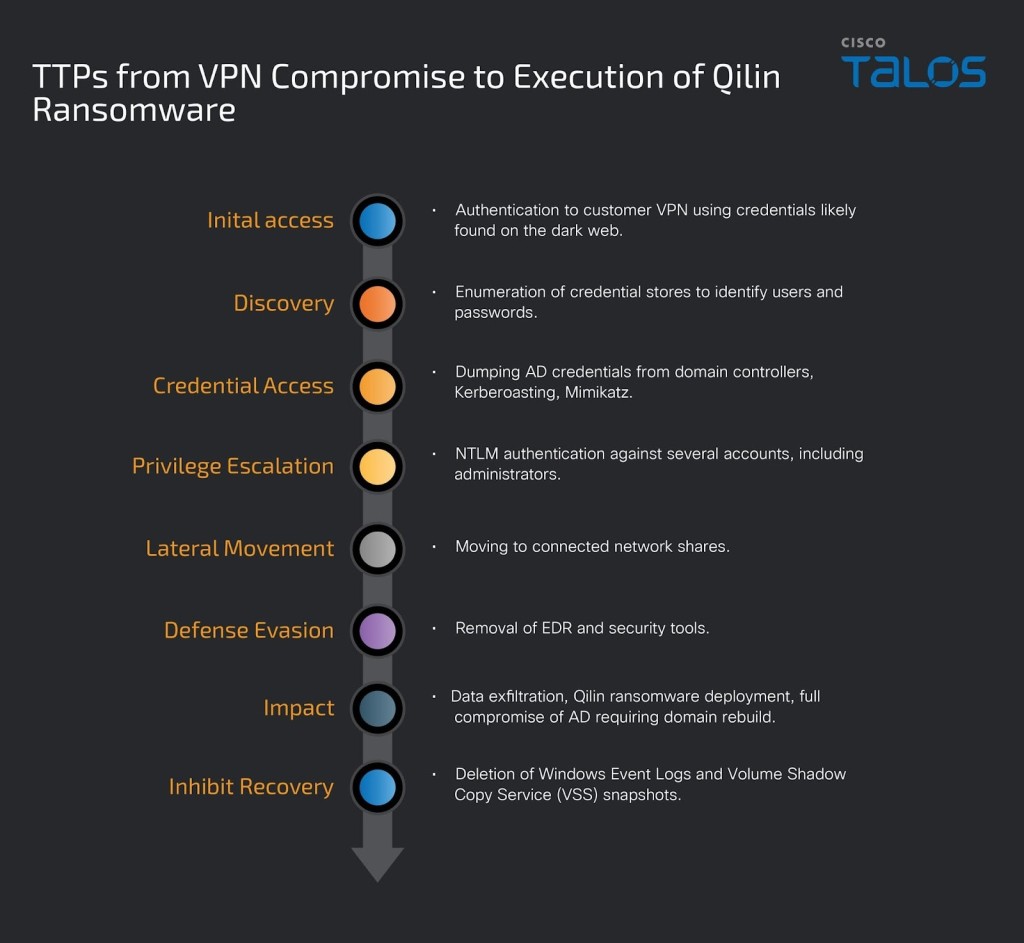
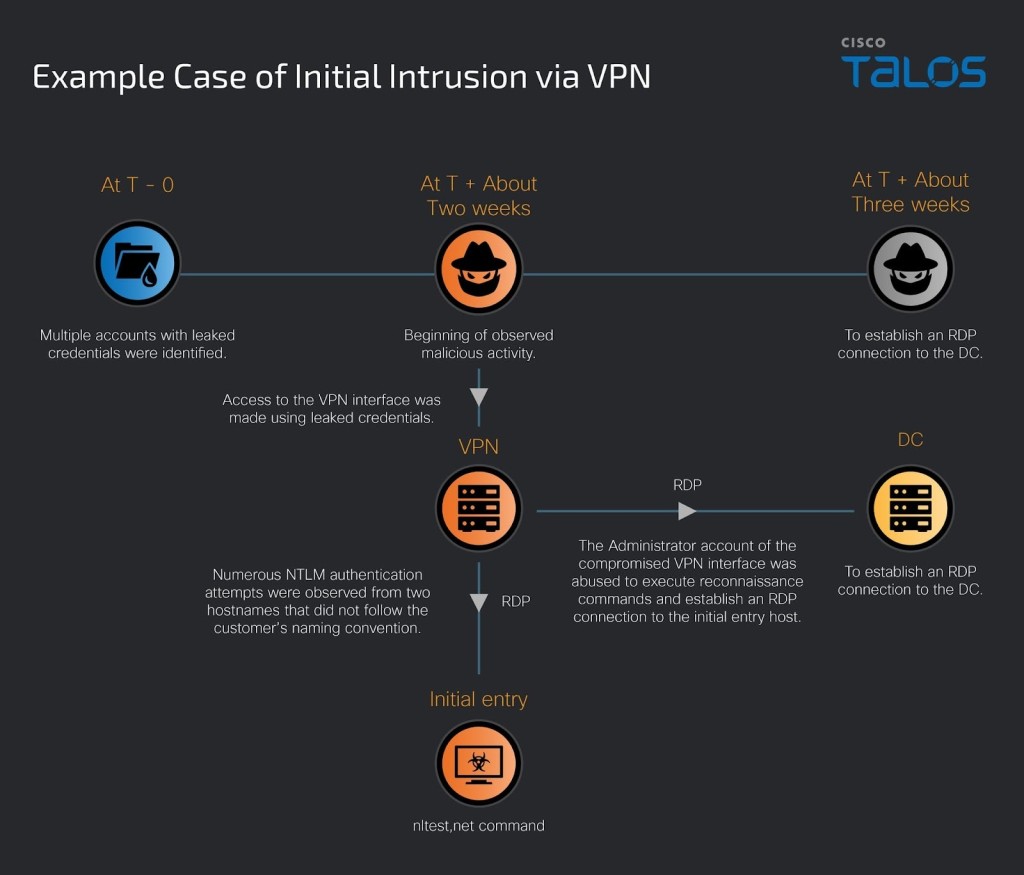
The Qilin ransomware methods detailed by researchers show a consistent pattern, sometimes starting with initial access through compromised VPN credentials, particularly where multi-factor authentication (MFA) is not enabled, and using Group Policy (AD GPO) changes that enabled Remote Desktop Protocol (RDP) to reach networks.
Once inside a network, the attackers conduct extensive reconnaissance using standard network tools and enumerate hostnames, domain users, groups, and privileges. They then deploy a custom toolkit, including Mimikatz and other NirSoft utilities, to harvest credentials from various applications.
They extract, redirect, and persist stored authentication data from multiple client applications for privilege escalation and lateral movement, including:
- WinSCP,
- Navicat,
- Xmanager,
- TeamViewer,
- FileZilla,
- Foxmail,
- TortoiseSVN,
- Google Chrome,
- RDCMan,
- SunLogin.
Data exfiltration is frequently carried out using legitimate tools like Cyberduck, which enables file transfers to cloud servers has been widely used in cases involving Qilin ransomware, to transfer large archives to cloud storage, effectively hiding malicious traffic.
“Talos found that the attackers used mspaint.exe, notepad.exe, and iexplore.exe to open and inspect files while searching through numerous files for sensitive information,” the report says.
Before encryption, attackers are observed disabling EDR solutions and using obfuscated PowerShell scripts to evade detection.
Dual Deployment and Double-Extortion Impact
A key finding is Qilin’s use of double-extortion ransomware tactics combined with a dual-deployment strategy for maximum impact. One encryptor is spread across multiple hosts using PsExec, while a second is sometimes used to target network shares, including critical infrastructure like Cluster Shared Volumes (CSVs).
The ransomware’s configuration is often customized for each victim, with hardcoded credentials to facilitate privilege escalation.
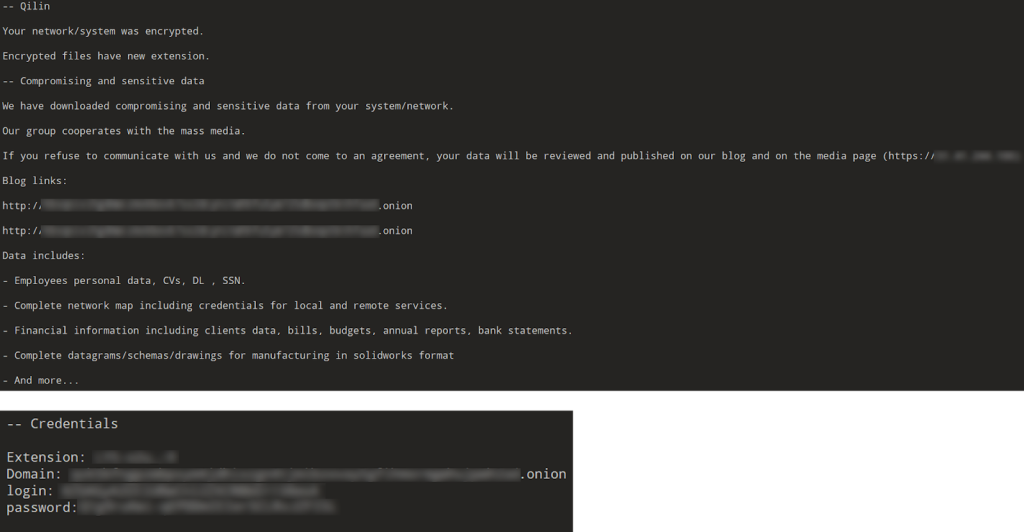
By exfiltrating data before encryption and threatening to leak it, the Qilin group applies immense pressure on organizations, making their ransomware attack tactics particularly destructive and effective.
In March, TechNadu reported on the Arcane Stealer targeting VPNs and crypto wallets of YouTube and Discord communities, a malware that also abused Cyberduck. RansomHub ransomware was also seen using malware such as Mimikatz.