ForumTroll APT Campaign Deploys the Dante Next-Gen Commercial Spyware in Russia, Belarus
- Sophisticated espionage: A cyber-espionage campaign dubbed "Operation ForumTroll" targets organizations in Russia and Belarus with spear-phishing attacks.
- Zero-day exploit: The campaign utilized a sophisticated zero-day exploit to escape the Google Chrome sandbox and deliver its payload.
- Commercial spyware link: It was linked to Dante, a commercial spyware tool developed by Memento Labs, the company that succeeded the notorious Hacking Team.
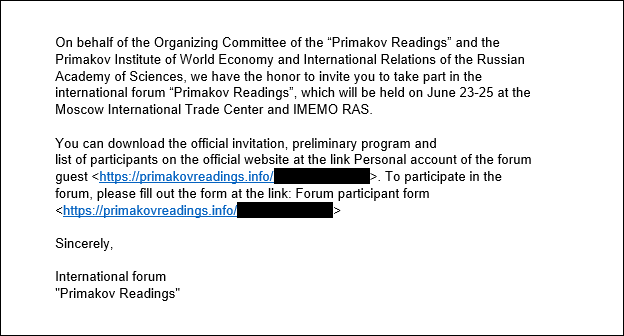
A highly sophisticated cyber espionage operation that initiated attacks using personalized spear-phishing emails containing malicious links primarily targeted media outlets, research centers, and government entities in Russia and Belarus. Visiting the malicious website was sufficient to trigger exploitation in vulnerable browsers.
LeetAgent and the Dante Connection
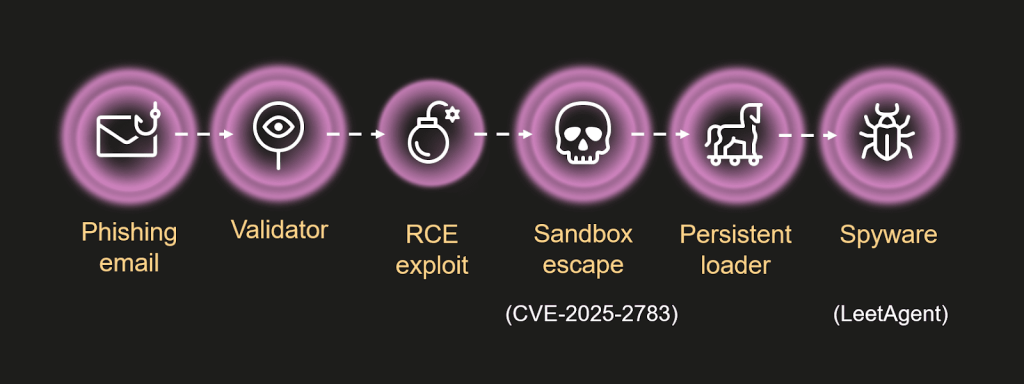
Kaspersky researchers uncovered this espionage campaign and tracked it as ForumTroll, which led to the discovery of a previously unknown commercial spyware called Dante. Simply visiting the malicious website using Google Chrome or another Chromium-based web browser triggered the infection.
These attacks successfully deployed a zero-day exploit (CVE-2025-2783) against Chromium-based browsers, allowing the threat actor to bypass the browser's sandbox and execute malicious code.
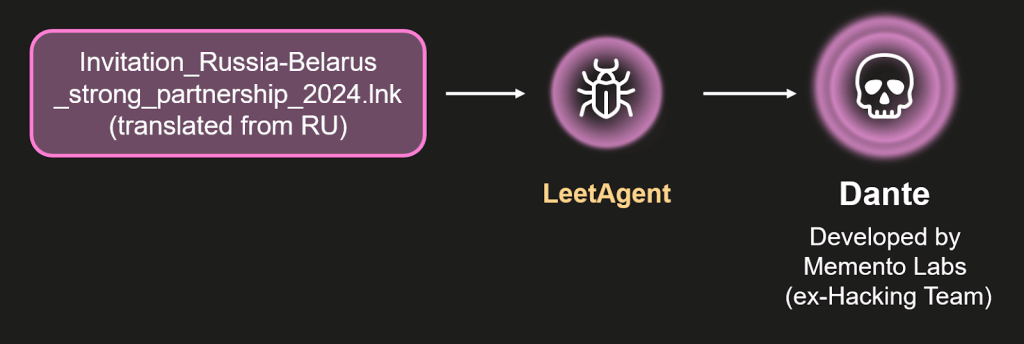
The initial payload observed in the ForumTroll campaign was a spyware module named "LeetAgent." This malware established persistence and communicated with a command-and-control server (C2) to execute further commands and exfiltrate data.
However, further investigation into related attacks revealed a connection to a more advanced spyware platform.
In some instances, LeetAgent was used to launch this second-stage payload, which was identified as Dante, which deletes itself and all traces of its activity if it doesn’t receive commands within the number of days specified in the configuration.
The Dante spyware is linked to Memento Labs, the Italian firm that emerged after the rebranding of the infamous spyware vendor Hacking Team.
Advanced Capabilities of Dante Spyware
The Dante spyware represents a significant evolution from Hacking Team's previous Remote Control Systems (RCS) platform. It is heavily obfuscated with VMProtect and employs numerous anti-analysis and anti-debugging techniques to evade detection by security researchers.
The spyware's architecture is modular, allowing attackers to load different capabilities as needed for espionage. Dante’s orchestrator displays the code quality of a commercial product, running keylogging and file-stealing tasks in the background.
The connection between the ForumTroll APT and a powerful commercial tool like Dante underscores the growing threat posed by the private surveillance industry and the proliferation of advanced offensive cyber capabilities.
Several companies currently develop surveillance software, including NSO Group, Intellexa, Paragon Solutions, Quadream, Memento Labs (formerly Hacking Team), and RCS Labs.
A few days ago, the SideWinder APT group was seen displaying evolved tactics while deploying the new ClickOnce malware. Earlier this month, a ClayRat Spyware campaign was observed targeting Android users via Telegram and fake websites for WhatsApp, TikTok, and YouTube.