Iran-Linked MuddyWater Launches Phoenix Backdoor Espionage Campaign via Compromised Accounts
- Targeted espionage: MuddyWater APT is conducting a sophisticated phishing campaign targeting international organizations for foreign intelligence gathering.
- Compromised accounts: Hackers utilize compromised email accounts, accessed via legitimate VPN services, to send phishing emails that appear authentic.
- Malware deployed: A malicious Microsoft Word document that executes a multi-stage infection process deploys version 4 of the Phoenix backdoor.
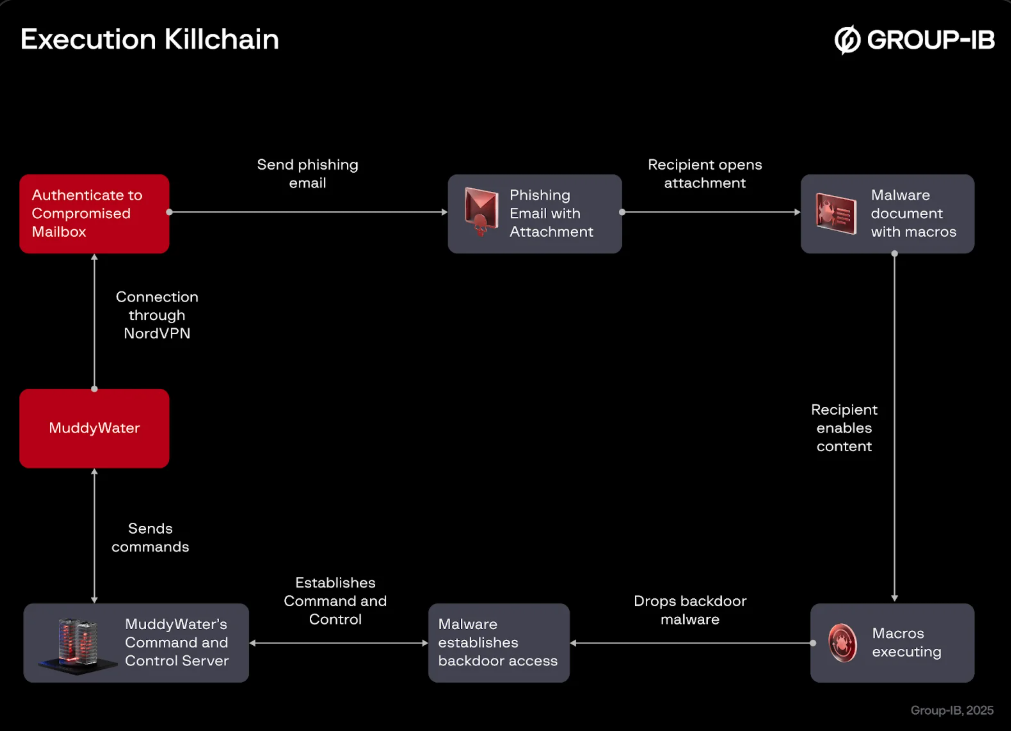
The state-sponsored group MuddyWater, linked to Iran, is utilizing sophisticated phishing techniques to infiltrate high-value targets and gather foreign intelligence. The widespread espionage campaign leverages compromised email accounts, accessing them through legitimate services like NordVPN to send malicious emails.
In the analyzed sample, the phishing email header is a NordVPN exit node located in France. By exploiting the inherent trust of these accounts, MuddyWater significantly increases the likelihood of deception, tricking recipients into activating the attack chain.
Phoenix Backdoor Malware Infection Chain
The attack begins with a phishing email containing a malicious Microsoft Word attachment. The document prompts the recipient to "enable content" to view what appears to be blurred text, Group-IB threat intelligence has uncovered.
Once the user enables macros, malicious Visual Basic for Application (VBA) code executes. This code functions as a dropper, writing a loader known as FakeUpdate to the disk.
The FakeUpdate loader then decrypts and injects the final payload, version 4 of the Phoenix backdoor malware, which has an embedded Portable Executable (PE) file designed to establish persistence.
This updated version of the backdoor establishes persistence and initiates communication with a command-and-control (C2) server for remote access and data exfiltration.
Attribution and State-Sponsored Cyberattacks
Group-IB attributes this campaign to MuddyWater (also tracked as Seedworm and TA450), believed to operate under Iran's Ministry of Intelligence and Security (MOIS), with high confidence based on the tools, techniques, and procedures (TTPs) employed.
The use of the custom FakeUpdate loader and Phoenix backdoor, along with specific code logic in the malicious macros, links directly to previously observed MuddyWater operations.
This cyberespionage campaign is a clear example of how state-sponsored cyberattacks are evolving, abusing trusted communication channels and legitimate infrastructure to evade detection while pursuing geopolitical objectives.
In July, MuddyWater disseminated a previously undocumented custom backdoor, named BugSleep/MuddyRot that mainly targeted Israeli organizations and deployed DCHSpy surveillanceware against government and private institutions disguised as legitimate applications like VPN or banking apps.