Maverick Banking Trojan Spreads on WhatsApp Using Worm-Like Propagation
- Distribution vector: A new banking Trojan, named Maverick, is being distributed on a massive scale through WhatsApp messages.
- Worm-like spread: It hijacks the victim's WhatsApp Web session to automatically send the malicious file to their contacts, enabling rapid, worm-like propagation.
- Advanced capabilities: This sophisticated, multi-stage, fileless threat can capture banking credentials, take screenshots, and log keystrokes.
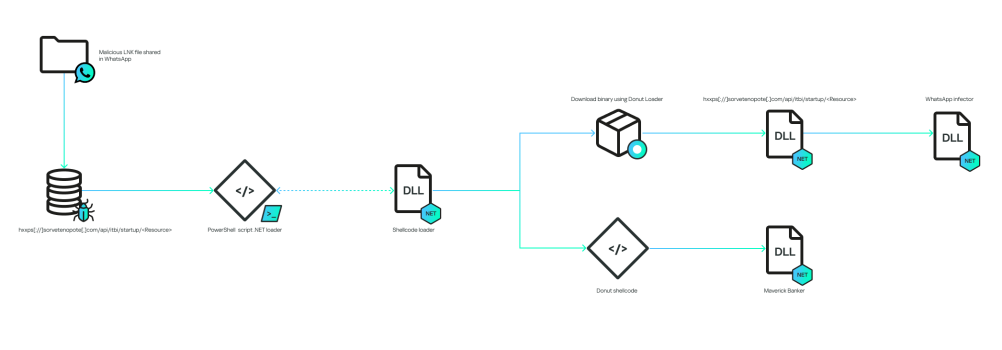
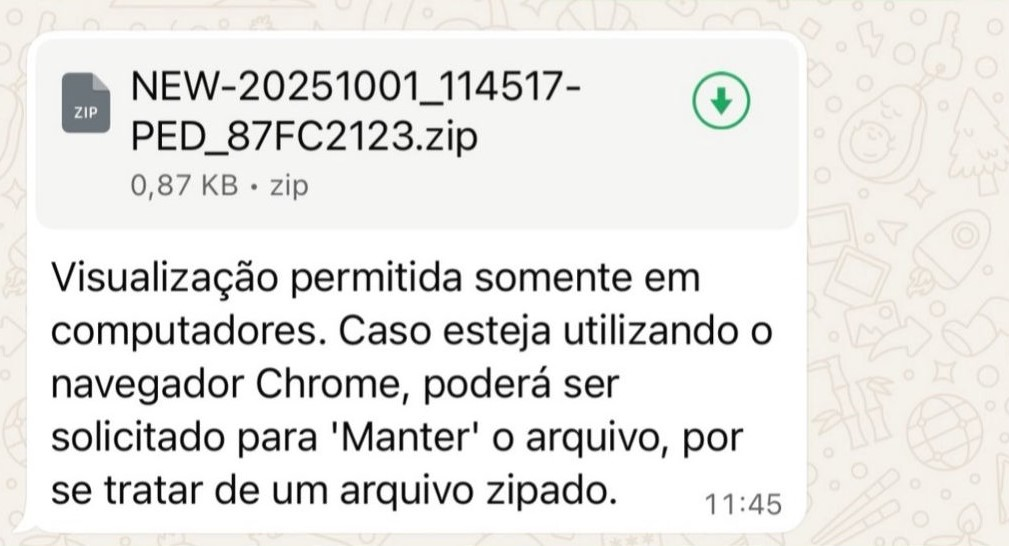
A highly sophisticated malware campaign is leveraging WhatsApp to distribute a new banking Trojan dubbed Maverick. The attack, which has primarily targeted users in Brazil, utilizes a complex, fileless infection chain that begins when a victim opens a malicious LNK file sent within a ZIP archive.
This method bypasses WhatsApp's typical file-blocking measures and has resulted in tens of thousands of infection attempts, according to cybersecurity researchers.
The Maverick Infection Chain and Capabilities
The Maverick banking Trojan employs a multi-stage, in-memory attack that minimizes disk activity to evade detection, a recent report from Secure List by Kaspersky says.
Upon execution of the initial LNK file, a series of PowerShell scripts and .NET loaders are executed to download and decrypt the final payloads.
It is designed to monitor a victim's browser activity on Chrome, Firefox, MS Edge, Brave, Internet Explorer, and specific bank web browsers, specifically targeting:
- 26 Brazilian banks
- Six cryptocurrency exchanges
- One payment platform
One component of this WhatsApp malware hijacks active WhatsApp Web sessions using the open-source WPPConnect project, automatically spreading the malicious ZIP file to the victim's entire contact list.
The primary payload is a powerful banking Trojan that shares code similarities with the previously identified Coyote Trojan. The Maverick certificate decryption and general code development are written with AI.
Cybersecurity Implications of the Attack
This banking Trojan's capabilities are extensive, including taking screenshots, deploying a keylogger, controlling the mouse, and overlaying phishing pages on legitimate banking websites to steal credentials.
The entire infection is modular and fileless, making it difficult for traditional security solutions to detect. While the campaign currently checks for a Brazilian time zone and locale before fully executing, its worm-like nature means it could easily spread globally.
The use of AI in the code-writing process further indicates the growing sophistication of financial cybersecurity threats.
This month, the ClayRat spyware targeted Android users via Telegram and fake WhatsApp, TikTok, and YouTube sites. In June, TechNadu reported on eight countries plagued by the Crocodilus Android banking trojan.