Australian Cyber Threat Report: 11% Increase in Incident Rate, State-Sponsored Actors Continue to Be a Threat
- Increased volume: The ACSC responded to over 1,200 cybersecurity incidents, an 11% increase from the previous year.
- Rising costs: The average self-reported cost of cybercrime for businesses surged by over 50% and 219% for large businesses.
- Persistent threats: State-sponsored cyber actors are actively targeting government and critical infrastructure for espionage and pre-positioning.
The latest Australian Cyber Threat Report indicates a 16% increase in calls to the Australian Cyber Security Hotline, an 11% rise in the number of cybersecurity incidents responded to by the Australian Cyber Security Centre (ACSC), and state-sponsored actors, such as APT40, actively targeting the nation.
Cyber Incidents and Costs Continue to Climb
The latest Australian Cyber Threat Report from the Australian Signals Directorate (ASD) highlights a significant escalation in malicious cyber activity.
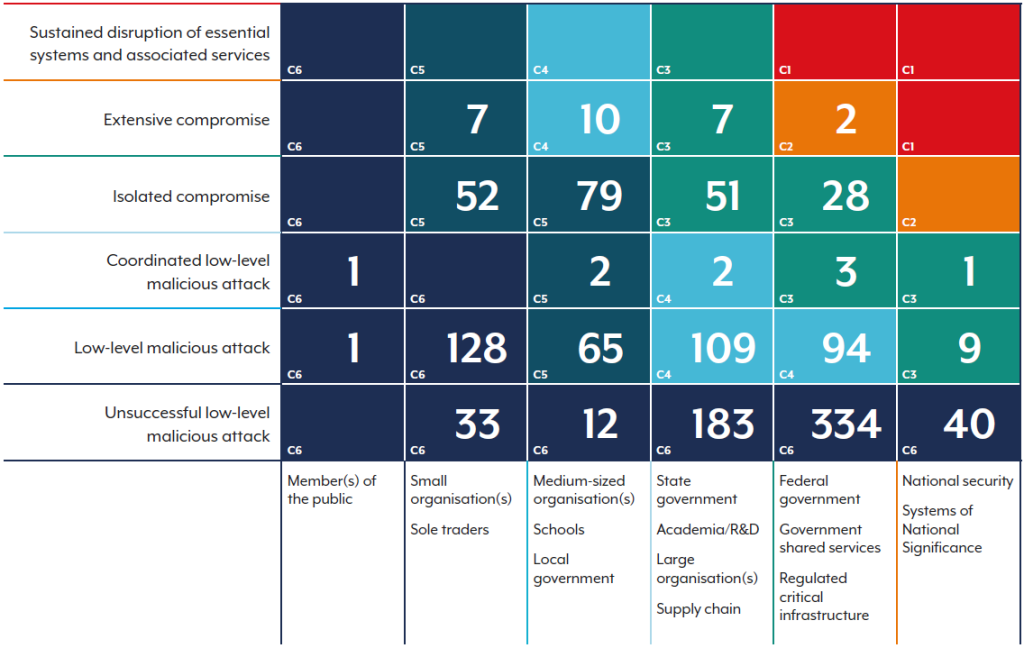
In the 2024–25 fiscal year, the Australian Cyber Security Hotline received over 42,500 calls, a 16% increase, while the number of cybersecurity incidents requiring a response from the ACSC grew by 11% to over 1,200.
The financial impact on Australian businesses has intensified, with the average cost per cybercrime report increasing by 55% for medium-sized businesses and by a staggering 219% for large businesses.
The Evolving Threat from State-Sponsored Actors
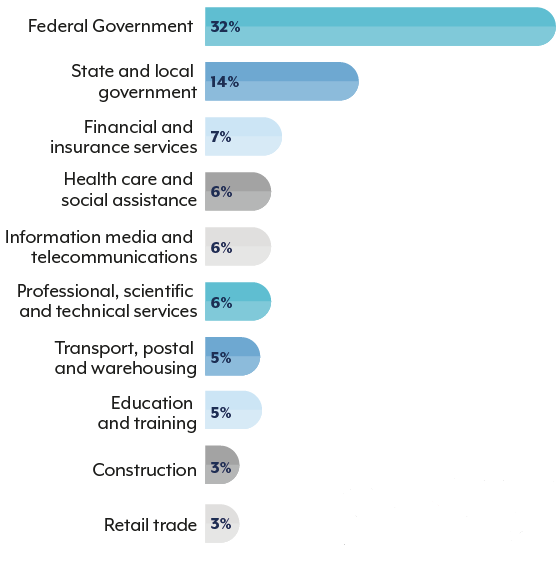
A key focus of the report is the persistent and sophisticated threat posed by state-sponsored cyber actors. These groups continue to target Australian government networks, critical infrastructure, and businesses to conduct espionage and pre-position for potential future disruptive attacks.
The report notes that these actors are increasingly using "living off the land" (LOTL) techniques, leveraging built-in network tools to evade detection.
The ACSC proactively notified entities of potential malicious activity over 1,700 times, an 83% increase, underscoring the aggressive nature of these threats.
“APT40 regularly conducts malicious activities against Australian and regional networks that possess information of value to the PRC,” the report said regarding the PRC state-sponsored group also known as Kryptonite Panda, Gingham Typhoon, Leviathan, and Bronze Mohawk.
ASD’s ACSC received over 84,700 cybercrime reports through ReportCyber and responded to 138 ransomware incidents.
“BianLian targeted Australian critical infrastructure sectors in addition to professional services and property development,” the report mentioned.
ASD also highlighted the financial sanctions and travel bans on three Russian nationals due to their senior roles in the cybercrime group Evil Corp and targeted sanctions on cyber infrastructure entity ZServers and five of its Russian employees.
Furthermore, the most recent Office of Australian Information Commissioner (OAIC) report noted the OAIC received 595 data breach notifications in the second half of 2024, an increase of 15% compared to the first half.
Also, in April 2025, Operation Firestorm discovered that a scam centre in Bangkok, Thailand, was targeting Australians with investment bond scams.
Enhancing National Cyber Resilience
In response to the escalating threat landscape, the report emphasizes the critical need for enhanced cyber resilience. Key vulnerabilities exploited by malicious actors include stolen credentials, unpatched software, and insecure edge devices.
The ACSC recommends that all organizations prioritize foundational security measures, such as implementing multi-factor authentication, maintaining regular backups, and patching systems promptly.
For businesses, the report advocates for:
- implementing effective event logging,
- replacing legacy IT,
- managing third-party risk,
- preparing for post-quantum cryptography to build a more defensible architecture against future challenges.
In other recent news, MI5 has warned U.K. politicians of state-sponsored espionage threats from China, Russia, and Iran.