Stealit Malware Abuses Node.js Single Executable Application, Disguised as Games and VPNs on File-Sharing Sites
- Novel distribution vector: A new Stealit malware campaign is actively leveraging Node.js's experimental SEA feature to package and distribute its payloads.
- Evading detection: The malware utilizes heavily obfuscated, multi-layered Node.js scripts and multiple anti-analysis techniques.
- Comprehensive data theft: Stealit can exfiltrate browser credentials and crypto wallet data, and provides extensive remote access capabilities.
An active Stealit malware campaign is employing a novel distribution method that abuses the Node.js Single Executable Application (SEA) feature. This experimental function enables developers to bundle a Node.js script and its dependencies into a single standalone binary, allowing it to run on systems without a pre-installed Node.js runtime.
Threat actors are exploiting this capability to package heavily obfuscated malware, disguising it as installers for games and VPN applications distributed via file-sharing sites. This approach succeeds previous campaigns that used the Electron framework for similar purposes.
Technical Analysis of the Malware
FortiGuard Labs uncovered this campaign following a spike in detections of a particular Visual Basic script, which was later determined to be a persistence component in the Stealit malware campaign.
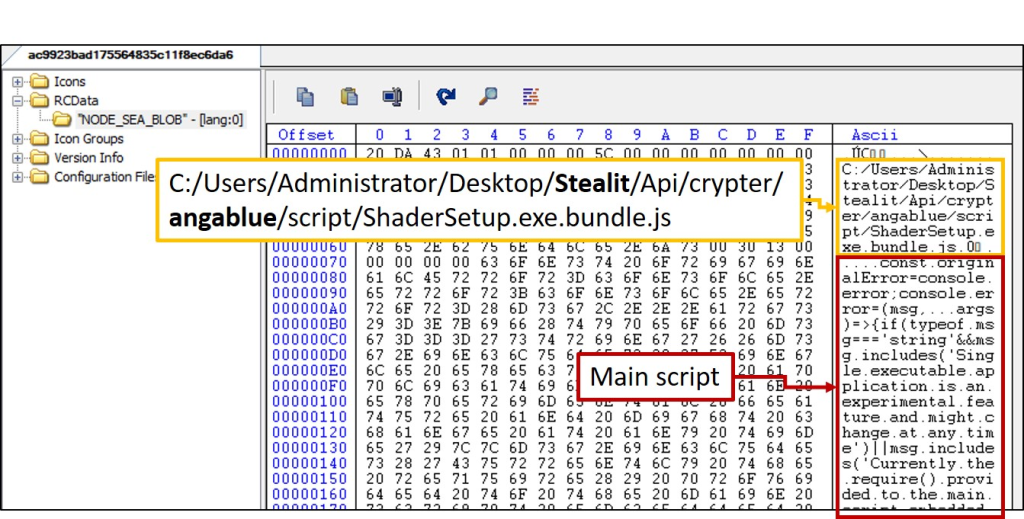
The attack begins with an installer that contains multiple layers of obfuscated Node.js scripts. The primary malicious script is stored as a raw data resource (RCDATA) named NODE_SEA_BLOB.
Upon execution, the malware performs extensive anti-analysis checks to detect virtual machines and debugging environments before proceeding. If it passes these checks, it downloads several components from its Command-and-Control (C2) server.
These components, packaged as executables, are designed to steal information from various applications, including web browsers, messaging clients such as Telegram and WhatsApp, and cryptocurrency wallets.
A persistence mechanism is established by placing a Visual Basic script in the Windows startup folder.
Remote Control and Emerging Cybersecurity Threats
The main client component, game_cache.exe, communicates with the C2 server, awaiting commands from the threat actor. The malware provides extensive remote access trojan (RAT) functionalities, including live screen and webcam viewing, remote command execution, and file extraction.
The campaign remains active and is evolving; researchers have already observed the operators switching C2 domains and reverting to the Electron framework in newer samples, indicating continuous development to bypass security measures.
The concept of "write once, run anywhere" is a “perpetual dream of developers, and it's ironic that JavaScript is now achieving this goal, originally envisioned by Java,” says Michael King, Senior Solutions Engineer at Black Duck.
King advises security teams to consult the API reference documentation for Node.js, which advises checking for node binaries without signatures or those signed by unauthorized parties.
Trey Ford, Chief Strategy and Trust Officer at Bugcrowd, stated that the gaming ecosystem is “a mess of binaries and network connections BEFORE you start adding in helpers, performance mods, and cheating resources.”
Ford added that the existing large population of privileged IT workers who are avid gamers means “hardware used for work and play, lateral network access to their laptops, and extortionary material on those users are all levers to be used for coordinated adversarial development.”
These evolving cybersecurity threats highlight the need for up-to-date threat intelligence and robust endpoint protection.
Another recent campaign disseminates ClayRat spyware, targeting Android users via Telegram and fake WhatsApp, TikTok, and YouTube sites.