Hundreds of Free VPNs Have Major Security Risks, Including Critical Vulnerabilities and Privacy Flaws
- Widespread flaws: An analysis of 800 free VPN apps for Android and iOS found several that exhibit dangerous security and privacy vulnerabilities.
- Critical flaws: These come with outdated code vulnerable to the old Heartbleed bug, request excessive permissions, and fail to meet app store privacy requirements.
- Enterprise threat: Flawed VPNs can create a weak link in an organization's security posture, exposing sensitive corporate data.
Significant VPN security risks across hundreds of free mobile VPN applications were found while analyzing 800 apps on both Android and iOS. A substantial number of these apps provide little to no real privacy, with some leaking personal data, requesting dangerous permissions, or relying on dangerously outdated code.
Key Findings from Zimperium zLabs Research
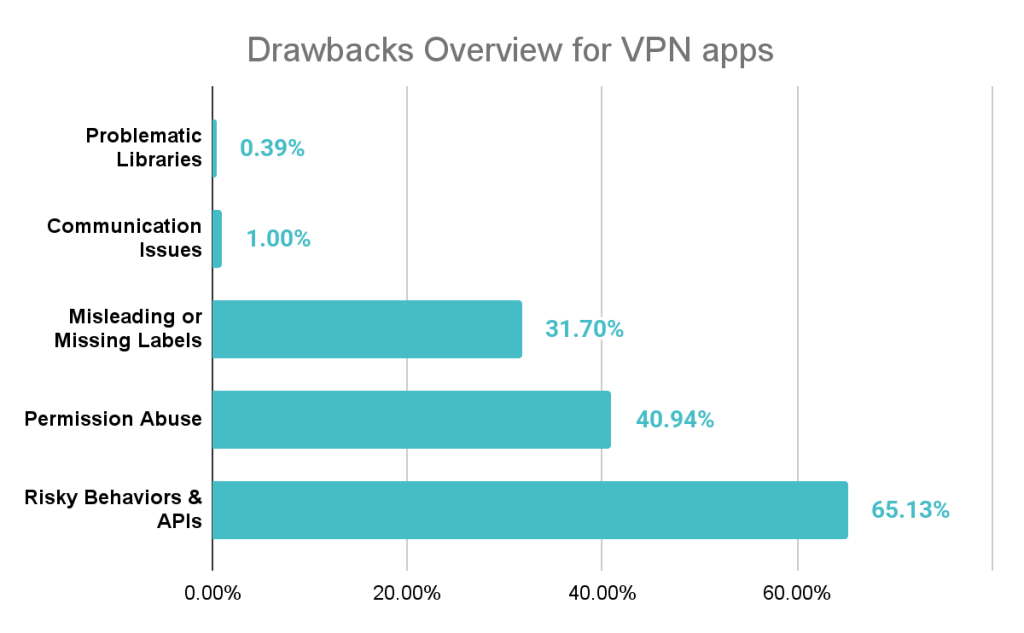
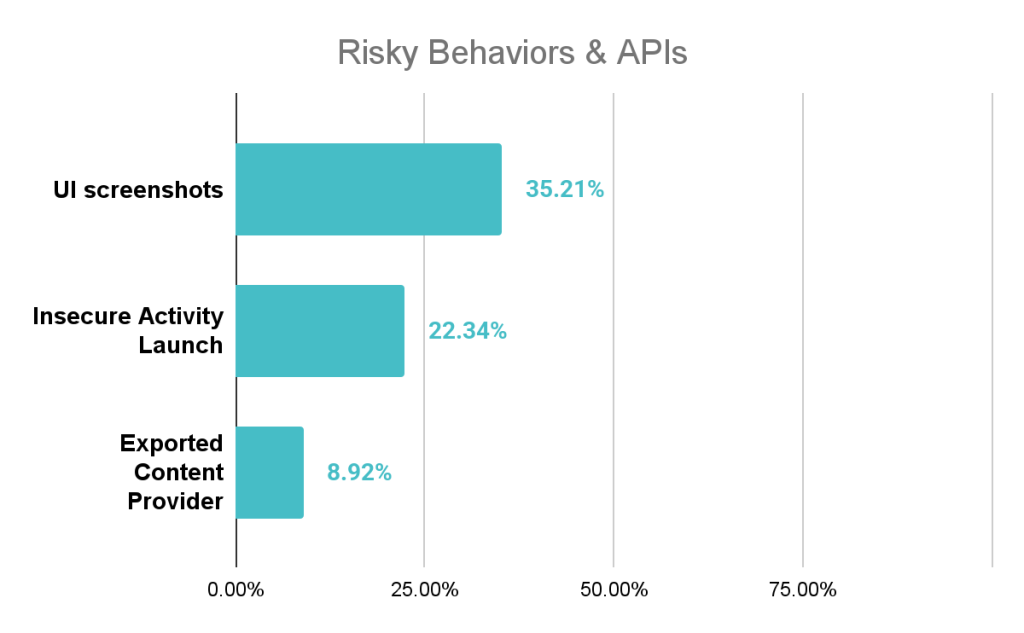
A comprehensive security analysis by Zimperium zLabs has identified several alarming trends. A notable 25% of the analyzed iOS VPN apps failed to include a valid privacy manifest, a violation of Apple's transparency requirements.
More concerning, 6% of iOS apps requested private entitlements, which grant powerful system-level permissions far beyond the scope of a typical application.
The analysis also discovered multiple apps still using a version of the OpenSSL library vulnerable to the infamous Heartbleed bug (CVE-2014-0160), a critical flaw disclosed over a decade ago.
Other permission abuses included unjustified requests for access to microphones, system-wide logs, and persistent location tracking.
A recent TechNadu write-up featuring experts’ opinions on free VPNs revealed that 88% of the top 100 free Android VPNs leaked user data, 71% shared information with third parties, 84% leaked traffic, and 18% failed to encrypt data at all.
“Today, we are facing a concerning reality that many enterprise mobile apps still lack basic protections such as code obfuscation, secure storage, and updated third-party libraries,” said Vishrut Iyengar, Senior Solutions Manager at Black Duck. “These weaknesses remain exploitable even in managed enterprise environments.”
Implications for BYOD Cybersecurity
These mobile VPN vulnerabilities present a direct threat to enterprise security, particularly for organizations with bring-your-own-device (BYOD) policies. When employees use these insecure VPN apps on their personal devices, they can inadvertently create an entry point for attackers into corporate networks.
Visibility into hidden risks, including outdated libraries and weak encryption, as well as misleading privacy policies and excessive permissions, is critical for protecting sensitive enterprise data and ensuring trust in mobile defenses, according to Zimperium.
“In today’s work-from-home environment, these risks multiply because personal devices are often outside IT’s control - but those devices are still interacting with proprietary data,” underlined David Matalon, CEO at Venn.
“The problem is intensified by the fact that many consumer VPN apps and browser extensions don’t undergo independent audits, and they can be an incomplete security solution, leaving users vulnerable to weak encryption and companies vulnerable to data loss,” Matalon added.
The research highlights the crucial need for organizations to implement mobile application vetting and mobile threat defense solutions to mitigate the risks associated with untrustworthy third-party apps.
An app with excessive permissions or unpatched vulnerabilities could be exploited to steal sensitive business data, credentials, or monitor communications.
“Organizations need a multi-layered response. Endpoint visibility and management are table stakes,” said Brandon Tarbet, Director, IT & Security at Menlo Security. “However, what is rapidly becoming a requirement is the need for web content-level data security.”
“Using Zero Trust Network Access (ZTNA) technologies alongside a robust zero trust and least privilege approach to identity security is critical to limit the blast radius in the event of exploitation or identity compromise,” said James Maude, Field CTO at BeyondTrust.
Iyengar recommends that security teams test mobile apps continuously, on real devices, and incorporated into a broader application security strategy. “This strategy should cover proprietary code, third-party SDKs, and open-source components to ensure complete risk coverage and application security without compromise.”
In other news, an Ontinue recent study said USB-delivered malware saw an increase this year compared to the second half of 2024.