273,000 Indian Bank Transfer Records Exposed in National Automated Clearing House Cloud Server Leak
- Significant exposure: An unsecured cloud server exposed 273,000 PDF documents containing sensitive bank transfer details of Indian customers.
- Sensitive information leaked: The exposed files included account numbers, transaction amounts, and personal contact details from forms.
- The source: The leaked information is related to India's National Automated Clearing House system.
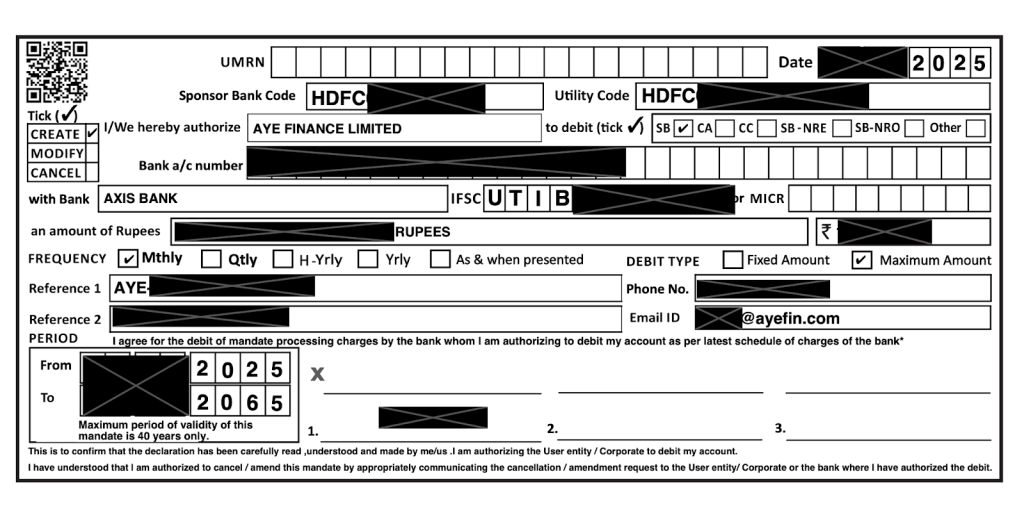
A significant Indian bank data exposure has been discovered on an unsecured, publicly accessible cloud server. The files were related to transactions processed through the National Automated Clearing House (NACH), a centralized payment system in India used for high-volume, recurring payments like salaries and loan installments.
Nature of the NACH Data Leak
Security researchers at UpGuard found 273,000 PDF documents in late August containing sensitive bank transfer information. The data was linked to at least 38 different Indian banks and financial institutions.
- 273,160 total files (UpGuard sample: 55K)
- 210GB total size (UpGuard sample: 42GB)
- 38 affected banks discovered in sample
- April 10, 2025 earliest document creation data
- ~3,000 new files added every day
The exposed transaction forms contained a wealth of personal and financial information, including customer bank account numbers, transaction figures, and contact details.
An analysis of a sample of 55,000 documents revealed that over half mentioned Aye Finance, a prominent Indian lender, with the State Bank of India also appearing frequently.
The misconfigured Amazon-hosted storage server left this critical information accessible to anyone on the internet, posing a severe risk to the individuals involved and raising serious questions about cybersecurity in banking.
Data Breach Response
Upon discovering the data leak, UpGuard notified Aye Finance, the National Payments Corporation of India (NPCI), and India’s computer emergency response team, CERT-In. The data was secured shortly after CERT-In was alerted.
An NPCI spokesperson denied that the data originated from its systems. “A detailed verification and review have confirmed that no data related to NACH mandate information/records from NPCI systems have been exposed/compromised,” they told TechCrunch.
The incident highlights the challenges in assigning accountability and ensuring timely notification to affected individuals when third-party data handlers are involved.
In other news, automotive data was exposed in a Git file leak at a major roadside assistance and insurance vendor in August.