After-Hours Cyber Threats Rise, Arctic Wolf 2025 Report Says
- After-hours threats: Findings show acceleration in threat activity, with more than half of the attacks occurring outside business hours.
- Why it matters: Threat actors exploit reduced staffing, slower response times, and periods of lower vigilance.
- Study sample: The report observed approximately 10,000 organizations in over 100 countries.
A significant acceleration in the threat landscape, with adversaries increasingly targeting organizations outside of standard business hours, was detailed in a comprehensive analysis of the evolving cyber threat landscape, drawing on more than 330 trillion security observations from over 10,000 organizations in 100+ countries.
Report Details
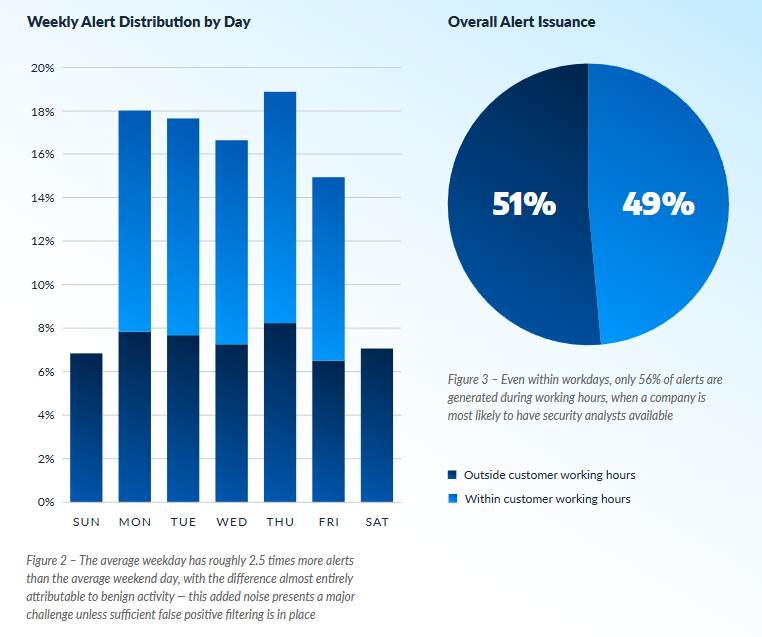
Arctic Wolf’s 2025 Security Operations Report findings highlight a pronounced acceleration in threat activity, with adversaries increasingly launching attacks outside traditional business hours—51% of security alerts now occur after hours, and nearly one-sixth (15%) of all alerts are generated on weekends.
This trend reflects a deliberate strategy by threat actors to exploit reduced staffing, slower response times, and periods of lower vigilance.
Addressing this, Tim Bazalgette, Chief AI Officer at Darktrace, said, "With the shortage of skilled cyber professionals continuing to grow, organizations are increasingly turning to AI-powered tools to improve efficiency in the SOC. In fact, 88% of security professionals believe that the use of AI is vital to freeing up time for security teams to become more proactive, according to the 2025 State of AI Cybersecurity report."
Casey Ellis, Founder at Bugcrowd, said, "The proliferation of AI-powered vulnerability discovery tools, as well as the growth of AI-assisted code generation, means that a fresh, vulnerable attack surface is being created at an increasing rate, and the tooling to find and exploit this attack surface is doing so more effectively. All of this nets out to higher throughput into the SOC, which necessitates a shift in thinking around the economics of processing SOC alerts."
Key Cybersecurity Trends for 2025
The report identifies several critical trends and statistics shaping enterprise security performance:
- 24/7 vigilance is essential: The surge in after-hours and weekend alerts demonstrates the inadequacy of business-hours-only monitoring. Effective security operations require persistent, around-the-clock visibility to rapidly detect and disrupt threats, which often strike when organizations are least prepared.
- Complex threat signals are buried in data noise: Arctic Wolf’s platform efficiently reduced 330 trillion raw observations to just 8.6 million actionable alerts, achieving one alert for every 138 million observations—a 99.99999999% reduction rate. Of these, 71% were further suppressed as benign or expected activity through context analysis and threat intelligence integration, ensuring analysts focus on genuine threats.
- AI-driven advancement: A machine learning solution automatically triaged 10% of security alerts, eliminating more than 860,000 manual reviews and contributing to a 37% decrease in Mean Time to Ticket (MTTT), which now stands at just over 7 minutes.
- Attackers target identity: 72% of active response actions were identity-based, reflecting that compromised credentials are the most common vector for initial access and escalation.
- Top targeted industries: Education, healthcare, and manufacturing report the highest alert volumes, driven by the presence of outdated infrastructure, high-value data, and operational requirements that limit downtime tolerance.
Campaigns such as those exploiting Fortinet FortiGate (Console Chaos) and SonicWall (CVE-2024-40766) vulnerabilities illustrated how intrusions could progress from initial access to broad privilege escalation and endpoint encryption in as little as 90 minutes.
Early detection is critical. Only 2% of the 9,000+ security investigations conducted during the report period were confirmed threats, highlighting the challenge of distinguishing malicious activity within massive volumes of operational telemetry.
Operational Recommendations and Conclusion
Addressing the challenges and offering advice, James Maude, Field CTO at BeyondTrust, said:
"Threat actors rarely work 9 to 5, so it is no surprise that 51% of alerts occur outside business hours and 15% happen on the weekend. In many cases, this is not simply a time zone difference but a deliberate ploy to strike when you are away from the keyboard. This is especially effective for identity-based attacks, as a user logging in on a weekend might not seem as suspicious an alert that malware is running.
One of the key reasons that users’ identities are easily exploited out of hours is that they have standing privileges and more often than not are overprivileged. When that is the case, if a threat actor is able to compromise an identity, they acquire 24/7 access with all the privileges the user has during the working day. This is why it is essential to reduce and ideally eliminate standing privileges using modern just-in-time approaches that only grant privilege when needed and take a zero-trust approach to validating the user’s identity.
Credentials are stolen, weaker forms of MFA can be bypassed, and helpdesks might even help a threat actor reset the credentials, so the best line of defense is to reduce the “blast radius” in the event of an identity compromise. Making sure that no matter what time of day or night it is exploited, the privileges, access, and risk are limited in scope.