Multiple CrowdStrike npm Packages Targeted in Supply Chain Attack as Attack Surface Expands
- CrowdStrike compromise: Multiple CrowdStrike npm packages were compromised in a growing supply chain attack.
- Identical malware: The Shai-Hulud malware is identical to that used in previous attacks, which affected over 40 other packages.
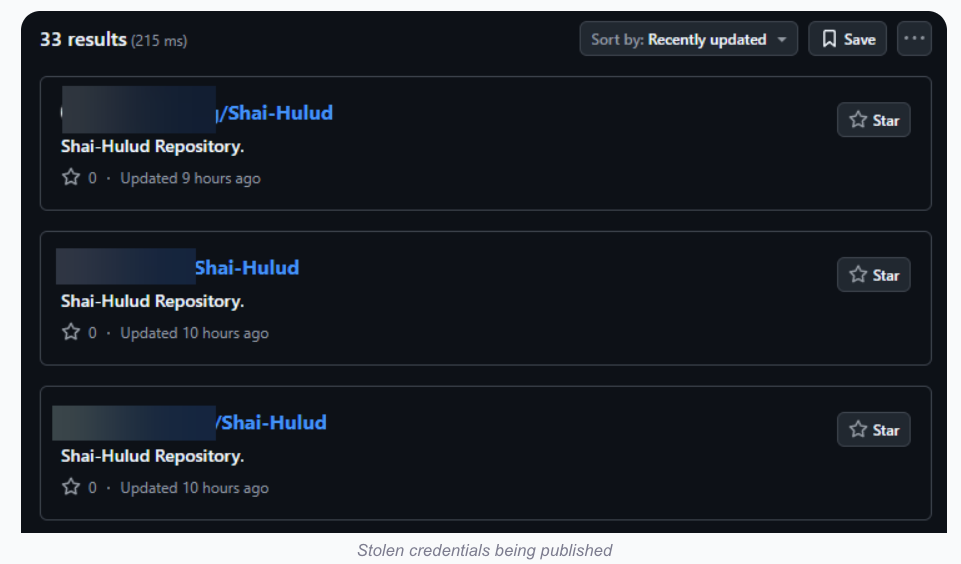
- Self-replicating: The malware steals and publishes more credentials every time a compromised package is installed.
An ongoing software supply chain attack, identified as a continuation of the "Shai-Hulud" campaign, has compromised multiple npm packages published by CrowdStrike. This incident highlights the persistent and evolving threats to software supply chain security, targeting widely used developer ecosystems to distribute malware.
Shai-Hulud Malware and Compromise Method
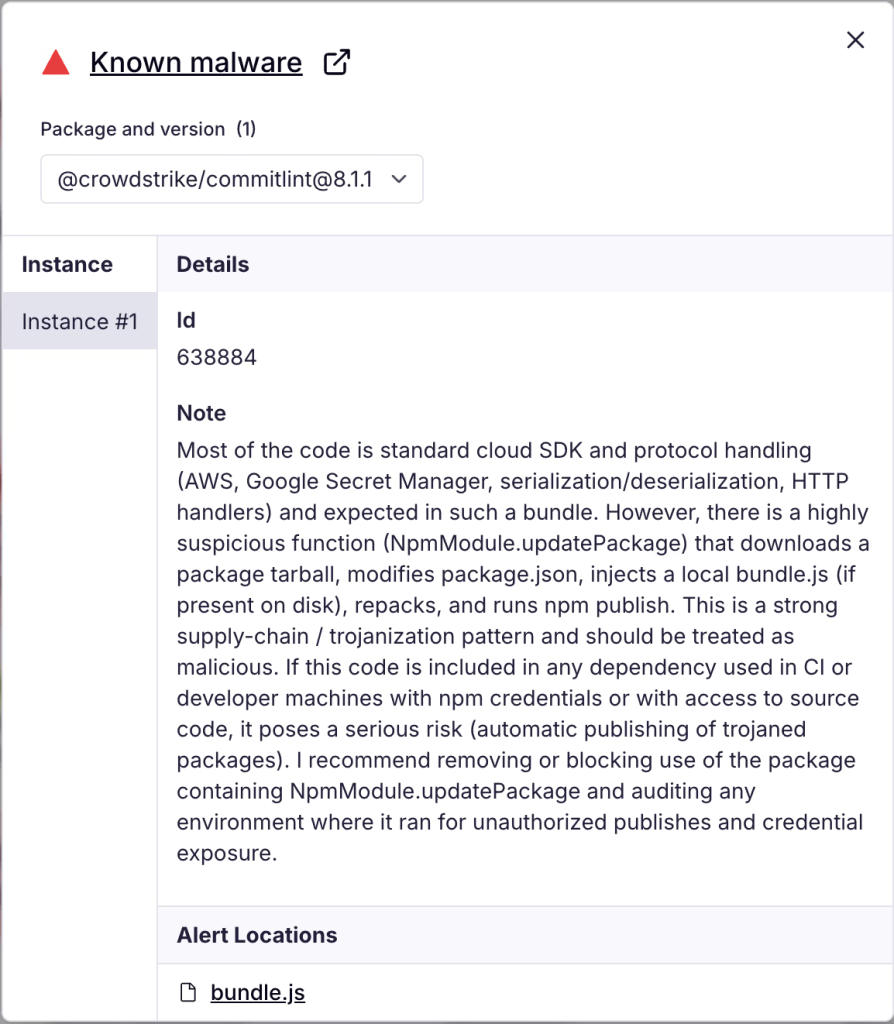
The attack involves the injection of malicious code into various npm packages, including several under the official CrowdStrike scope, as reported by Socket. The npm registry has since removed the compromised package versions.
“After detecting several malicious Node Package Manager (NPM) packages in the public NPM registry, a third-party open source repository, we swiftly removed them and proactively rotated our keys in public registries. These packages are not used in the Falcon sensor, and the platform is not impacted. We identified the single source and isolated it quickly, customers remain protected and do not need to take any actions,” a CrowdStrike spokesperson told TechNadu.
The malware is identical to that used in previous "Shai-Hulud" attacks, which affected over 40 other packages, including tinycolor.
According to KrebsOnSecurity, 187 code packages have been infected with the self-replicating worm. The Socket report highlighted that the attack surface is expanding and provided a list of 477 npm packages and their corresponding versions.
Charlie Eriksen, a researcher for security firm Aikido, said the malware looks for an npm token in the environment and, upon finding it, “modifies the 20 most popular packages that the npm token has access to, copying itself into the package, and publishing a new version.”
The malicious payload, typically embedded in a bundle.js script, is designed to exfiltrate sensitive data from compromised systems.
Upon execution, the malware utilizes the legitimate secret-scanning tool TruffleHog to search developer environments and CI/CD systems for credentials, tokens, and other secrets. It then exfiltrates this information to a hardcoded webhook endpoint.
"This latest supply chain attack on over 40 npm packages, including popular ones like @ctrl/tinycolor, highlights the escalating sophistication of adversaries targeting open source ecosystems," said Mike McGuire, Senior Security Solutions Manager at Black Duck.
"Attackers are exploiting the inherent trust developers place in registries like npm," he further added.
A key feature of the Shai-Hulud malware is its persistence mechanism. The script attempts to create an unauthorized GitHub Actions workflow file named shai-hulud.yaml within the compromised repository. This ensures that the data exfiltration step can be triggered in future CI runs, long after the initial infection.
Randolph Barr, Chief Information Security Officer at Cequence Security stated, "This isn’t just about code quality, it’s about trust in the entire CI/CD pipeline." Barr shared the following high-impact actions:
- Pin dependencies to avoid unexpected package updates
- Use tools like Snyk or OWASP Dependency-Check for SCA
- Scan commits with Gitleaks or TruffleHog to prevent hardcoded secrets
- Validate tokens using scoped access policies
- Review build agent privileges to avoid overly broad access
- Implement centralized logging to detect credential scanning or metadata probing
Impact and Security Implications
This CrowdStrike npm supply chain attack underscores the significant risk posed by compromised dependencies in modern software development. By targeting packages from a reputable cybersecurity firm, the attackers increase the likelihood of their malware being integrated into sensitive corporate and developer environments.
The compromise of the @crowdstrike/commitlint and @crowdstrike/foundry-js packages, among others, illustrates the broad reach of this campaign.
Security teams are advised to audit their environments for the presence of affected package versions and rotate any potentially exposed credentials.
Addressing the risks, Shane Barney, Chief Information Security Officer at Keeper Security said, "This incident, which injected malicious code into npm packages to scan for and steal developer credentials, demonstrates how quickly a single compromised component can ripple across an ecosystem and become an entry point for wider breaches."
Nicholas Weaver, a researcher with the International Computer Science Institute, recommended that NPM and similar package repositories immediately switch to a publication model with explicit human consent for every request using a phishing-proof 2FA method.
TechNadu reported on September 9 that at least 18 popular packages, including debug and chalk, which collectively account for over 2 billion weekly downloads, were compromised. In March, security researchers noted the North Korean Lazarus Group targeted developers with a new wave of malicious npm packages.
This story has been updated with a statement from CrowdStrike.