Avatel Telecom Allegedly Targeted in Data Breach
- Telco attack: Spain’s prominent telecommunications provider Avatel Telecom was allegedly targeted by a cyberattack.
- Breach scope: ByteToBreach claims it stole approximately 380 gigabytes of user data from an Oracle database.
- What was exposed: Exfiltrated data is reportedly related to infrastructure, financial, contracts, clients, and users.
A claimed cyberattack against Avatel Telecom, a prominent telecommunications provider in Spain, was announced by a threat actor going by the alias ByteToBreach.
Details of the Claimed Avatel Telecom Data Breach
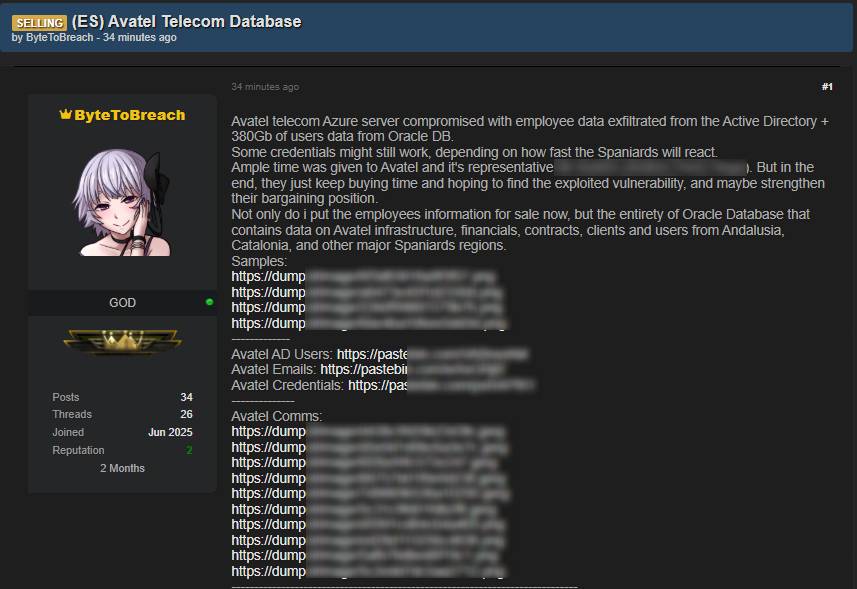
According to posts on a dark web breach forum, the ByteToBreach cyberattack was initiated by compromising one of Avatel's Azure servers. This initial access point was said to have enabled the threat actors to pivot and exfiltrate employee data directly from the company's Active Directory.
Furthermore, ByteToBreach said it extracted approximately 380 gigabytes of user data from an Oracle database.
The dataset is purported to be extensive, containing a wide range of sensitive information. The compromised information reportedly pertains to customers across multiple Spanish regions, including Andalusia and Catalonia, and includes:
- infrastructure details,
- financial records,
- contractual documents,
- client and user data.
Following the exfiltration, the relatively new-registered user listed the data for sale on a cybercrime forum, substantiating its claims with proof-of-access, such as credentials, internal documentation, and server configuration files.
Implications for Telecom Cybersecurity
This alleged telecom cybersecurity incident serves as a critical alert for the industry. The potential Spain data breach would place its customers at high risk of fraud and identity theft.
The alleged event underscores the necessity for robust security postures, continuous monitoring of cloud environments, and stringent access controls to defend against determined threat actors.
In August, a TPG Telecom cyberattack exposed thousands of customers’ data through an iiNet breach in Australia, while South Korea’s SK Telecom suffered a data breach in July.